Archive for August 2012
Tuesday, August 28, 2012
Chris Foresman:
Specialist performance will now be directly measured in part by how many accessories they can sell with each hardware item sold. So if you walk in to buy a MacBook Air, the new metrics would encourage sales people to push you to buy cases, hard drives, AirPort base stations, and more.
It’s sad that it sounds like Tim Cook is pushing towards a Steve Ballmer–style sales guy strategy. However, an anonymous genius writes:
As a current Genius at a very high profile Apple Retail store, I’m happy to report that ifoAppleStore’s (and other’s) sources are either flat-out wrong or highly exaggerated. Very little has changed since Browett has taken over, and what has changed has been overwhelmingly for the better.
I was unable to load the original ifoAppleStore article.
Update (2012-08-29): Gary Allen on ifoAppleStore:
According to accounts, Cook pushed Johnson “quite hard” about how other channels were selling more Mac’s per-capita than the retail stores. Without Jobs’ support, Johnson found it was nearly impossible to keep Cook and Oppenheimer from switching the chain’s primary purpose from a superior experience to revenues.
Apple Retail Stores John Browett Ron Johnson Tim Cook
Brent Simmons:
The Next Web reports that Google has pulled its undocumented weather API. I dread the day when this happens to the also-undocumented Google Reader API.
Google RSS Web API
Dropbox:
Two-step verification is an optional but highly recommended security feature that adds an extra layer of protection to your Dropbox account. Once enabled, Dropbox will require a six-digit security code in addition to your password whenever you sign in to Dropbox or link a new computer, phone, or tablet.
Cloud Dropbox Security
Ray Dillinger (via Manuel Simoni):
C is not just a simple language. Heck, it’s nowhere near as simple as, say, Scheme or Haskell. C is a simplistic model of the machine, memory, and runtime environment. It provides a few facilities for abstraction, but as a deliberate design choice, it makes sure that there are specific, simple, known ways for programmers to break every abstraction. That’s really what the ultra-simple memory model of C is all about; enabling programmers to break abstractions.
That isn’t a mistake or a design failure; That is exactly what the designers of the language set out to do. It is a goal in which they succeeded.
C Programming Language Language Design Programming
Ben McCormack:
To solve this problem, we added a simple script called ‘Backup FogBugz’ to the recipes section of the FogBugz XML API Development wiki. It checks FogBugz for unread cases, then saves the updated case info to a local HTML file. It doesn’t save everything—you wouldn’t be able to e.g. restore FogBugz with this data—but it does give you a relatively fresh copy of the data on your local machine.
Bug Tracking FogBugz
Jordan Golson:
After three days of deliberations, the jury reached a unanimous verdict in the Apple vs. Samsung trial. The jury found largely for Apple, ruling that Samsung had willfully infringed on both Apple patents and trade dress for the iPhone -- though notably the jury found in favor of Samsung on questions regarding its tablets. The jury found that Samsung owes Apple $1.05 billion in damages for willfully infringing on Apple’s intellectual property.
Thomas Baekdal:
Why didn’t I patent it? Well, because it’s not an invention. All I did was to find a solution to a problem. If you had the same problem you would have found the same solution. I didn’t invent anything. I only looked at what we had and said “hmmm ...we need to be able to click on that...”
The idea that one company can own a solution to a problem is absolutely insane.
Nick Wingfield:
Consumers could end up with some welcome diversity in phone and tablet design — or they may be stuck with devices that manufacturers have clumsily revamped to avoid crossing Apple.
Andy Ihnatko:
The lesson here is that the so-called Patent Wars, mostly a campaign of skirmishes before now, has suddenly turned into global thermonuclear war.
Matt Drance:
I must admit I’m uncomfortable with the idea that the world’s largest corporation, whatever its name, could be given such a big stick as early as this week. However the verdict falls, I feel like there are no winners here in the long term — certainly not us.
Ryan Kim:
Samsung still faces the stigma of being a copy cat and there is the looming threat that the damages could be tripled because of willful infringement. But it might have been worth it if Samsung’s brand gets elevated to Apple’s level, said Reuters.
Enrique Gutierrez:
I’m writing this post after the fourth group of Starbucks patrons have made the connection that Samsung is now the same as Apple. They don’t know the details, they don’t really care, what they know is Apple is saying that Samsung is the same as Apple…and with one simple Google Search, you get prices that are basically half for what seems to be the same products—for nearly everything.
Apple Brands Lawsuit Patents Samsung
Andreas Fredriksson:
I recently moved from Sweden to the US. Now that my bank is here in the US, I switched my Apple account over to the US region.
Doing so made everything under “Purchases” and “Updates” disappear in the Mac App Store. After a long frustrating email exchange I was told by the App Store support that apps are tied to a region, so if you have downloaded an app in one region it’s forever tied to that region. Their message was: You have to keep your account in the Swedish region to receive updates. Note that this applies even to free stuff like Twitter!
Mac Mac App Store
Friday, August 24, 2012
Armin Vit:
Apple has always been the anti-Microsoft and Microsoft has always been the anti-Apple, pretty much in all respects. Speaking graphically: while Microsoft was unleashing Hideous on its Windows OS in the 1990s, Apple’s “Classic” OS was a thing of simplistic beauty, which then they fucked up with OS X but that’s another story. And while Microsoft shied away from its corporate logo, Apple steamrolled the entire country with its stores and its glowing apple logo as a beacon of simplicity and goodness. Lately Apple has also been fucking up its logo with extraneous texture effects, coupled with OS X and all the core Apple applications that have become ghastly, putting us Apple-devotees in a position where Apple being the anti-Microsoft is a negative thing. Microsoft’s commitment to graphic simplicity is what attracted us to Apple and its OS in the first place and now that that is disappearing it leaves these four, dumb squares as the next beacon of simplicity and goodness.
I like the new logo and Segoe.
Apple Graphic Design Logo Microsoft
Daniel Jalkut:
How does this kind of “blacklisting” occur on Mac OS X 10.8? I suppose in the future we might see restrictions that tie in to the new Gatekeeper signing system, but that is of no help if the targeted apps are not signed. The current mechanism is in the form of a crude XML file installed by Apple in your System folder:
/System/Library/CoreServices/CoreTypes.bundle/Contents/Resources/Exceptions.plist
There are lots of interesting overrides there.
Mac VMware
Thursday, August 23, 2012
Agen G. N. Schmitz:
Shortly after Mountain Lion was released, MacBook Air and MacBook Pro owners reported on Apple’s support forums that running 10.8 caused significant battery drainage issues, with some complaining that battery life was reduced to almost half the normal amount. Ars Technica then ran what they called “real world” tests on its MacBook Pro with Retina Display (which, according to Apple, should have an 8-hour battery life on a full charge), and their testing results never yielded more than 5 hours and a few minutes of run time.
Jim Tanous:
With great anticipation, we installed the final build of 10.8.1 this morning and ran our benchmark again, only to be disappointed by the results. Battery life did improve by about 17 minutes over the prerelease build, but we are still over an hour short on battery life compared to 10.7.4’s numbers, a difference of about 20 percent.
Battery Life Mac Mac OS X 10.8 Mountain Lion
Jonathan Dann (formerly of Sofa) on the previously announced rewrite from HTML5 to Objective-C:
One of the biggest advantages we’ve gained from building on native iOS has been the ability to make the app fast. Now, when you scroll through your news feed on the new Facebook for iOS, you’ll notice that it feels much faster than before. One way we have achieved this is by re-balancing where we perform certain tasks. For example, in iOS, the main thread drives the UI and handles touch events, so the more work we do on the main thread, the slower the app feels. Instead, we take care to perform computationally expensive tasks in the background. This means all our networking activity, JSON parsing, NSManagedObject creation, and saving to disk never touches the main thread.
Jacqui Cheng:
Facebook’s previous app—particularly the version just before this, 4.1.1—did not have a good reputation. Ratings on the App Store hovered around the two-star mark, and on any given day, a search on either Facebook or Twitter would yield hundreds of complaints about the mobile app’s slowness or bugginess.
Facebook iOS iOS App Software Rewrite
John Carmack:
I had mentioned something about how, you I’ve been learning a whole lot, and I’m a better programmer now than I was a year ago and the interviewer expressed a lot of surprise at that, you know after 20 years and going through all of this that you’d have it all figured out by now, but I actually have been learning quite a bit about software development, both on the personal craftsman level but also paying more attention by what it means on the team dynamics side of things.
Craft John Carmack
Wednesday, August 22, 2012
Allan Odgaard:
As for the latter key though, ⌘B is also bound to “Bold” in many markup languages so we have a conflict. The Build command “wins” because the attribute scopes are more specific than the content scopes which means that if we press ⌘B in our README.md then we will build the project rather than make a word bold.
I no longer use TextMate, but I still find its design interesting.
Mac Mac App TextMate
Bill Van Hecke:
But during the course of pursuing our iPad or Bust initiative, we decided that we would never have a better time to make our app icons more consistent. Better to change all the icons at once than to wait for each of our five huge productivity apps (spread across three platforms) to reach major versions, updating the icons one by one. So we got to work on coming up with a consistent style.
I like these more icon-style icons.
Graphic Design Mac Mac App The Omni Group
Tuesday, August 21, 2012
Amazon Glacier is like Amazon S3 except that it’s much cheaper to store data (1 cent vs 13 cents per GB per month, uploading still for free) and accessing that data takes much longer (hours!). It will be interesting to see whether backup applications such as Arq will able to take advantage of Glacier (probably in combination with S3).
Update (2012-08-22): sintaks:
While the link between your device and the service will be much fatter, the reason Glacier is so cheap is because of the custom hardware. They’ve optimized for low-power, low-speed, which will lead to increased cost savings due to both energy savings and increased drive life. I’m not sure how much detail I can go into, but I will say that they’ve contracted a major hardware manufacturer to create custom low-RPM (and therefore low-power) hard drives that can programmatically be spun down. These custom HDs are put in custom racks with custom logic boards all designed to be very low-power. The upper limit of how much I/O they can perform is surprisingly low - only so many drives can be spun up to full speed on a given rack.
Jeff Barr:
Retrieval requests are priced differently, too. You can retrieve up to 5% of your average monthly storage, pro-rated daily, for free each month. Beyond that, you are charged a retrieval fee starting at $0.01 per Gigabyte (see the pricing page for details). So for data that you’ll need to retrieve in greater volume more frequently, S3 may be a more cost-effective service.
Amazon Amazon Glacier Amazon S3 Cloud
Jeff LaMarche:
SceneKit provides some functionality for creating scenes from scratch right in your code, but is primarily designed for working with 3D scene data exported from an external application like Maya, 3DS Max, Modo, LightWave, or Blender. SceneKit uses the Collada file format, which is supported by most (if not all) major 3D programs (though with some caveats I’ll discuss later). The Collada file format doesn’t support just 3D objects, it can store information about an entire 3D scene including lights and cameras as well as armatures and animation data for both simple object animation and complex skeletal animation.
Framework Mac Scene Kit
Mac OS X Hints shows how to make applications save new documents to “On My Mac” by default, rather than iCloud (via Chris Foresman).
Cloud Esoteric Preferences iCloud Mac Mac OS X 10.8 Mountain Lion
Saturday, August 18, 2012
Mike Bierly and Rob Burdine have taken over development from Matt Milano and Infinity Data Systems:
The company that we established for MailForge is Macsimize Software. We are in the process of getting the site ready right now. Our expectation is that we will have something up and running early to mid next week. The first priority will be to get the basics set up - email setup for support, questions, all of those things. To me, the basics are getting forums and an issue/enhancement reporting system available.
And on the new Macsimize forum:
I would like to reassure people that the primary purpose for MailForge is to be a Eudora replacement. […] I am in total agreement with the folks who have said work on stability before adding features. I’m sure you recognize that no software is ever 100% bug free but it is absolutely reasonable to expect an application to behave and function as expected 99.99% of the time. MailForge is going to be used as our own primary email tool. That way we will have the incentive to make sure it is stable sooner rather than later.
E-mail clients are a tough business, but it’s good to see that both the developers and users are excited. I wish them the best of luck, and I look forward to working with them on integration with my products.
E-mail Client Mac Mac App MailForge
Apple QA1758:
Prior to iOS 6 / OS X 10.8, using the the Zombies instrument or NSZombieEnabled or the "Enable Zombie Objects" Xcode diagnostic, prevented ARC from “cleaning up” instance variables at deallocation-time. Your -dealloc methods would still be run, however any instance variables that you didn’t explicitly set to nil would be untouched. If an instance variable strongly referenced an object, then that object would be kept alive forever by the abandoned instance variable.
Via Cédric Luthi, who offers a workaround.
Automatic Reference Counting (ARC) Debugging Objective-C
Zongyao Qu (via Slashdot):
Sandboxing, although said to be a good protection from the malware, brings too many troubles to the applications themselves. I have made 6 builds trying to make MPlayerX pass Apple’s review and I have explained why some privileges are so important for MPlayerX to achieve this and that features, But the answer is NO, NO, NO, NO, NO and NO.
MPlayerX will lose so many features if it adopted Sandboxing, it could not load the subtitle automatically, it could not play the next episode for you automatically, it could not save the snapshots to the place where you want to, etc. Without those features, MPlayerX were just another lame Quicktime X, which I could not accept.
It’s a better player than QuickTime Player, plus it supports more video formats.
Mac Mac App Mac App Store Sandboxing
Thursday, August 16, 2012
This post from Michael Sippey sounds like the end for third-party Twitter clients. They’ll be restricted in the number of users they can have as well as in the ways they can display tweets. Multi-network clients, e.g. for Twitter and App.net, are prohibited.
See also: comments from Marco Arment, Lex Friedman, Dr. Drang, Manton Reece, and Iconfactory.
Update (2012-08-28): Paul Haddad:
With the above rules being in place its easy to see why continuing the public alpha/beta would be problematic. Someone might use the app, decide they don’t like it and the token would be gone forever.
Twitter Web API
Allan Odgaard:
We could modify this command to support the special issue scheme, but that is not elegant. Instead we make a minor but important change to the injection grammar from above. We change the name key to markup.underline.link.$2.hyperlink. What we did was add $2 which is the second capture from the regular expression, namely the URL scheme (more about syntax allowed in format strings).
[…]
What’s great about this is that we can now create a new command, still using enter as key equivalent, but using a more specific scope selector so that it only targets issue links.
Jeff LaMarche:
I received a fairly prompt response from AppStoreNotices@apple.com with regards to the Tile Cutter infringement I blogged about earlier today. They’ve sent an e-mail to Wang Ting, the “developer” fond of taking apps off of GitHub and selling them as his own creations. Apple has asked him to voluntarily take down TileCutter or provide evidence that he has the right to publish the app.
[…]
Maybe if Apple gets enough DMCA takedown notices for the same developer in a short enough period of time, they’ll consider doing the right thing. I’m not holding my breath, mind you, but I feel like I have to try and make the right thing happen if I can. Finding a way to get word all the rights holders seem the best and only way to do that right now.
Omar Choudary (via Dave Dribin):
During the past year Joachim Metz, Felix Grobert and I have been analysing this encryption mechanism. We have identified most of the components in FileVault 2’s architecture and we have also built an open source tool that can read volumes encrypted with FileVault 2. This tool can be useful to forensic investigators (who know the encryption password or recovery token) that need to recover some files from an encrypted volume but cannot trust or load the MAC OS that was used to encrypt the data. We have also made an analysis of the security of FileVault 2.
They’ve published a paper and the code.
Ken McKinney and Hacker News report that Joyent is reneging on its lifetime hosting plans that were promised to be honored for “as long as we exist” (via Nicholas Riley). They also haven’t given customers much notice before the October 31 sunset date.
Update (2012-09-06): TextDrive co-founder Dean Allen:
I’d like to announce that on November 1st, 2012, TextDrive will relaunch anew as a separate hosting company, staffed and funded, run by me. Please consider the recently announced end-of-life for Joyent’s shared hosting customers now revised to be a continuation-of-life, to be carried out in the same friendly, creative, publishing-centered spirit of TextDrive’s early days.
Wednesday, August 15, 2012
The GCC project (via Slashdot):
What matters for GCC going forward is that it continue to be comprehensible and maintainable. That is a struggle that GCC has faced for its entire existence as a free software project. It is certainly true that using C++ unwisely can make that struggle more difficult. But this issue is not qualitatively different from the issues we face today.
Tuesday, August 14, 2012
Dr. Drang:
I guess the real question is whether those who’ve signed up for app.net are actually prepared to leave Twitter for it. So far, it looks like most of them are still tweeting, and I’m curious as to how many of them can leave.
I get why people are looking for a Twitter alternative, but using Twitter plus another service doesn’t seem to be a very good solution. And the robotweeting and having to pay to reserve your username leave a bad taste.
Alex Hillman:
App.net is a fascinatingly similar Rorschach test on the community surrounding it. It’s a mirror, it reflects back to them what they want and care about. And people are spending $50, $100, & $1000 at a time based on what they believe the creator intends to do. Dalton has stated his intentions, to a point, but most of the 3rd party discussion has turned to speculation.
Dave Winer:
What seems very unlikely to me is that the new thing will fall neatly in place on one company’s servers, or even with one company’s servers at the center. It’s never been that way.
Clark Goble:
The main debugger, lldb, comes with Python built in! […] it appears you can actually have a Python script run when a breakpoint gets hit. The current stack frame and breakpoint location are passed to your function.
I tend to instrument my code because I really dislike clicking around in the debugger. This seems to have a lot of potential for making debugging faster.
Update (2012-08-15): Clark Goble:
What you could do to make the above function a tad more useful is keep a global counter that is incremented in every call to the Python function and then increment the column in Numbers by the same amount. That’ll give you a nice spreadsheet listing variables and their value according to time. More than a slight bit more readable than trying to traverse the output of numerous NSLog calls. You could even write a script that reads the values in say the first column down, treating them as variable names, and then print their values.
Update (2012-08-16): Clark Goble:
When you print things from your Python scripts the first time off a break not everything will print. At first I thought Python-lldb weren’t seeing all the variables. However everything gets copied to the spreadsheet properly. So it’s really a bug in Xcode where all the text output isn’t getting displayed correctly. This is useful to know if you start relying on lldb and scripting. Interestingly the second time you run your script on a single breakpoint the problem disappears. Until you advance your position in code whereupon it all begins again. Undoubtedly a small bug that will be fixed in a future Xcode version.
John Gruber:
I’ve been staring at a variation of that cursor since the 1980s. Perfectly vertical on the left, stair-stepped at precisely 45° on the right. Now, though, on this machine, it’s a perfect arrow, as perfectly un-jaggedly straight on the diagonal as it is on the vertical.
I think this is one of those cases where the technology was inevitable, but Apple getting behind Retina displays will really speed up their adoption. As Gruber says, you kind of have to see it to believe it. I hope that my external display holds up, but I don’t want to buy a new one that’s non-Retina.
Incidentally, Daring Fireball has now been a top-quality site for ten years. Congratulations. That’s about as long as I’ve been following other Mac writers and developers via RSS and writing my own blog. I hope that we’ll all be around in another ten.
Glenn Fleishman and Jeff Carlson:
You could set up device-specific iMessage accounts and mark each as the Caller ID sender for its particular device. This is a little absurd, but it would work for enabling you to receive an incoming message on all devices, but have subsequent replies directed only to a particular device. For example, Glenn could set up glenn@tidbits.com on each of his devices, so iMessages to that address would show up everywhere. But, if the Caller ID address for his Mac was glenn-osx@tidbits.com and his iPhone was glenn-iphone@tidbits.com, responses to his iPhone-generated replies would come back solely to the iPhone. Similarly, when he initiates a conversation from a given device, his recipient doesn’t need to know that’s where it comes from; they just reply.
Monday, August 13, 2012
Shriram Krishnamurthi (via Lambda):
We will be making this course, Brown’s upper-level programming languages offering, available for free on the Web. People anywhere are welcome to view the lectures, read the materials, and do the assignments.
Based on what I’ve seen from Krishnamurthi before, this should be interesting.
Christopher Breen:
The interesting thing here is that while Mail will allow you to save printed PDF files to iCloud, there’s no way to access them because Mail doesn’t have a documents window. Likewise, if you were to go to icloud.com and click on Mail, you’d find no storage location for anything created by Mail. It doesn’t exist.
The fallback is to access the local copy in your hidden Library folder, but that’s not really meant to be touched.
ToS;DR (via Michael Lopp):
ToS;DR aims at creating a transparent and peer-reviewed process to rate and analyse Terms of Service and Privacy Policies in order to create a rating from Class A to Class E.
Great idea.
Sunday, August 12, 2012
Mike Ash:
CommonCrypto is a convenient library provided with Mac OS X and iOS that provides a range of cryptographic primitives. It provides cryptographic hashes, message-authentication codes and key-derivation functions based on those hashes, and symmetric encryption. It's not a fully-featured cryptography library like OpenSSL, as it's missing more complex features such as public key cryptography and common protocols like TLS. However, if your needs fit within its capabilities, CommonCrypto is easy to use and requires no third-party code.
Chris Espinosa:
Of all the things I have worked on at Apple, HyperCard changed me most. It was deeply revolutionary, deeply misunderstood, deeply controversial. I have never had to fight Apple internal organizations so much, or received so much amazing support, on any other project. The Apple of 1986 and 1987 was still reeling from the departure of Steve Jobs, yet trying to claw its way back to relevance and success through execution, and HyperCard was seen as a hangover of the Steve era. It was a skunkworks project, written entirely off-campus, out of the normal management chain. The Engineering group didn’t want to spend resources on it. Evangelism thought that bundling it with every Mac would complicate our delicate relationships with software vendors. And nobody could really explain what it did or why we needed to do it.
Andy Lee:
As of this moment, Googling for “scene kit sample code site:developer.apple.com” still doesn’t find these examples, which I find odd, since they’ve been available for a good ten days. The Scene Kit API docs don’t point to the examples yet, but this is less surprising; I’m sure the docs will be updated in good time.
Scene Kit looks like great technology, but I’m not really sure what to do with it.
Oliver Taylor (via Clark Goble):
While BBEdit has many great tools for prose writers, its cursor movement and selection shortcuts do not compare impressively with its own coding shortcuts, or with certain other editors. This package of scripts aims to substantially improve your movement and selection abilities when writing prose in BBEdit.
Majd Taby and
joocode have some good tips (via
Clark Goble).
Thursday, August 9, 2012
Allan Odgaard:
Today I am happy to announce that you can find the source for TextMate 2 on GitHub.
I’ve always wanted to allow end-users to tinker with their environment, my ability to do this is what got me excited about programming in the first place, and it is why I created the bundles concept, but there are limits to how much a bundle can do, and with the still growing user base, I think the best move forward is to open source the program.
I’m not really sure what this means, but he’s not abandoning the project and is already receiving criticism about the GPL 3 license.
Update (2012-08-12): Chris Foresman interviews Allan Odgaard:
My motivation is and always was to create a great editor. If I find something better that fills my needs, I will switch to that—but I doubt it [will happen]. I will continue using and working on TextMate for as long as I am a Mac user.
On the other hand, though work is ongoing, it doesn’t sound like TextMate 2.0 is very close to being completed.
TextMate
Wednesday, August 8, 2012
Tom Dalling:
There was an interesting question on StackOverflow this morning: Why doesn’t NSOrderedSet inherit from NSSet? It’s interesting because the reason is so easy to miss. I thought it would make a good blog post because it turned out to be a nice, real-life example of the Liskov substitution principle (herein abbreviated to LSP).
He points to the -mutableCopy method, but I think there’s a problem with the -isEqual: method even when considering only immutable sets. An ordered set wants to include order in its definition of equality, while a regular set cares only about membership. Equality can’t be implemented in a way that’s symmetric and transitive. Thus, it makes sense for them not to be subtypes.
Rui Carmo:
I find it somewhat disturbing that a single username and password provides access to all my personal data on iCloud and to my iTunes Store account - and urge you to consider allowing customers to opt in to higher-grade security and allowing for privilege separation between different kinds of Apple IDs.
John Paczkowski (via John Gruber):
Authored by Samsung’s product engineering team, the document evaluates everything from the home screen to the browser to the built-in apps on both devices. In each case, it comes up with a recommendation on what Samsung should do going forward, and in most cases, its answer is simple: Make it work more like the iPhone.
I’m torn here. On the one hand, these are such little details. It would be absurd to suggest that Samsung’s Web browser shouldn’t display the number of tabs because Safari does that on the iPhone. On a quick skim, I didn’t see anything that seems like it should be patentable. On the other hand, it’s unsettling that Samsung seems to be going through detail-by-detail to clone Apple’s design work.
Tuesday, August 7, 2012
Lloyd Chambers:
Time Machine has repeatedly and silently added both my Boot and Master volumes to its “Exclude these items...” list.
This is not a one-time thing, I have seen it happen 15-20 times in 3 months. This includes after erasing the backup drive and the original volumes, so it is not tied to a particular volume; it is a general bug. With OS X Lion and Mountain Lion.
I never saw this bug when I was using Leopard or Snow Leopard. With Lion, I stopped using Time Machine as it was severely slowing down my system and frequently corrupting its backups.
This is a guest post by Jonathan Grynspan. I followed his reporting of this issue on Twitter with interest. The basic issue is that, with the default settings, if your Mac is asleep or booted up and logged out, anyone who has your Apple ID and password can access your encrypted FileVault 2 files. This is true even if you have not shared your FileVault recovery key with Apple. Far more than 140 characters were needed to get the full picture, so I encouraged Jonathan to blog about it. As he does not currently have a blog, we decided to post his report here. —Michael
I’m Jonathan Grynspan. I write code. I’m a little wordy. This is gonna be a long one, ’cause of the wordiness.
I, like a number of other security-minded Mac users, turned on FileVault 2 before my new MacBook Air was even out of the box. Whole-drive encryption? Damn skippy! Turns out however that, as of Mountain Lion, FileVault 2 has a 50/50 chance of being completely broken on your system. There’s a backdoor that appears to have been accidentally built in by Apple, and it can be used by an attacker to gain root access on your system.
Mac OS X v10.7 Lion and later include a feature intended to help users with oddly spotty memory. If you’ve forgotten your login password, but remember your Apple ID password, you can reset your login password based off that. (If alarm bells are going off in your head right now, they might be because of Mat Honan’s recent bad luck involving his iCloud account, which doubles as an Apple ID.) In order to use this feature, you must enable it in System Preferences → Users & Groups. That looks like this:
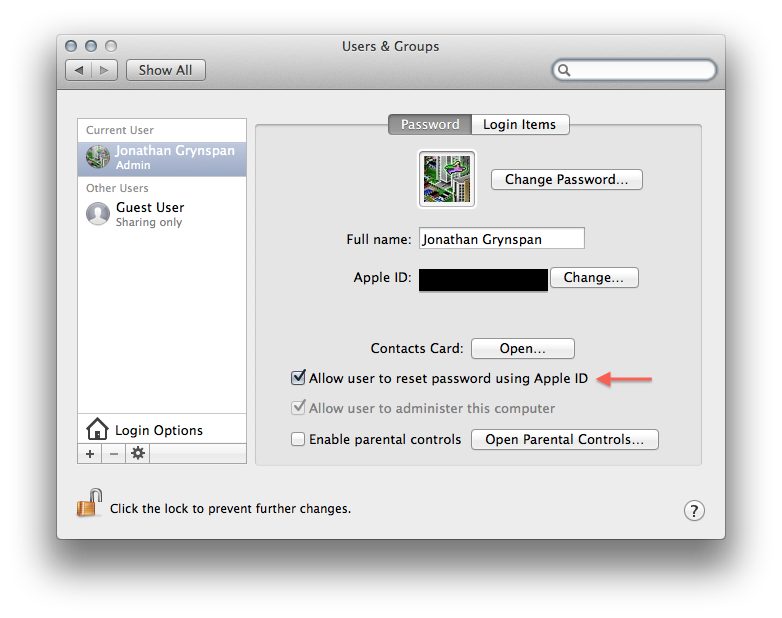
Worryingly, this was enabled by default on my MacBook Air as soon as I upgraded from the copy of Lion it shipped with. I did not enable this feature.
OS X also includes a feature called FileVault 2, as I previously mentioned, that encrypts your entire hard drive and requires your login password to decrypt it. When FileVault 2 is enabled, resetting your password by entering your Apple ID is intended to be disabled (as suggested by the FileVault 2 tech note linked above.) Problem is, it’s not disabled—the option is just hidden from view in System Preferences. As I found out a few days ago, if the setting is enabled when you encrypt your drive, the checkbox disappears and you cannot disable it. The only way to turn off Apple ID–based password recovery is to decrypt your drive, change the setting, and re-encrypt. That process can take a very long time depending on the size of your drive and whether it’s a hard disk or an SSD. The 1 TB drive on my iMac takes several hours to process completely.
My iMac, though protected with FileVault 2, can be accessed fully (including root access via sudo using my login password) by an attacker who knows my Apple ID password, almost completely defeating FileVault 2. I should note that, to my knowledge, this issue requires physical access to your Mac. That said, FileVault 2 is explicitly designed to protect against attacks even when the user has physical access; whole-drive encryption is kind of pointless otherwise. But it gets worse. An Apple employee might never touch your keyboard, but Apple ID–based password recovery as designed may allow a malicious Apple employee to gain access—there’s no guarantee or promise from Apple that turning off the feature in the OS UI actually disables the logic involved.
I don’t want to be alarmist. I believe this was an honest oversight by Apple’s engineers, and one that can be corrected in a point release. I’m a loyal Apple user and have been for years. I make a living writing code that only runs on Apple products. But Apple’s boilerplate response when I reported this backdoor was worrisome at best:
Thank you for filing this issue via Apple’s bug reporting system. Apple takes every report of a potential security issue very seriously. After examining your report we do not see any actual security implications. [emphasis mine]
My Apple ID controls much of my data—especially the data I associate with my dealings with Apple, Inc. My login password, on the other hand, protects via FileVault 2’s encryption: every photo of my loved ones that I’ve ever taken; identifying information including my address, phone number, Social Insurance Number, and passport number; all my banking records and tax returns; my medical records…this is personal stuff, not work stuff. I don’t want somebody to be able to decrypt my drive and see it because they have an unrelated Internet-facing password.
Worse, what if I had incriminating evidence on my hard drive (e.g. some movie torrents, or photos of me and my friends and eleven herbs and spices)? A government (foreign or domestic) could serve Apple with a warrant and unlock my encrypted drive for me and I wouldn’t be able to stop them—I don’t even know if turning off the feature in System Preferences would actually do any good! Kim Dotcom would go apeshit over this backdoor.
If the system is coming up from a cold boot, the option to use your Apple ID is not present, presumably because the system can’t load network drivers until it has decrypted them. You’re safe at that point. But once the system is up, if you log out or turn on the screen saver or close the lid or somehow wind up at the login screen, the option appears and can be used. When the setting is enabled, the password hint popup looks like this:
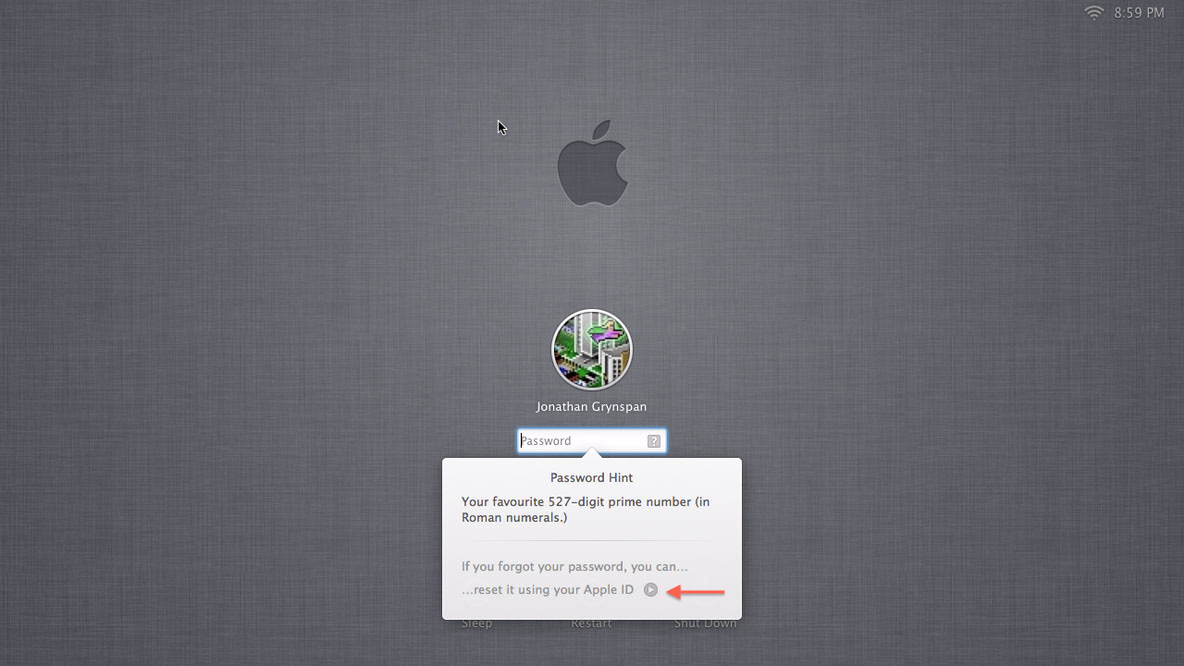
And the attacker can use that arrow button to gain access very quickly. There is therefore a workaround, but it requires vigilance. Whenever you leave your computer for more than a few seconds, shut it down entirely. Don’t let it go to the login screen unless it’s the one presented by FileVault 2 at boot time. And don’t let your Mac out of your sight.
My thanks to Michael for giving me a soapbox on which to stand here.
Apple ID FileVault Mac Mac OS X 10.7 Lion Mac OS X 10.8 Mountain Lion Security Top Posts
Kevin Malakoff (via Hacker News):
_.m is a port of Underscore.js to Objective-C. It strives to provide the fullest feature set possible in a way that is familiar to JavaScript developers (despite the differences between JavaScript and Objective-C).
There are some neat features and ideas here, but it would be interesting to see how they could be expressed with more Objective-C-style naming and syntax. I think most of the utility is in the functionality, not the low character count.
See also: Underscore.m (via Groxx).
Update (2012-08-12): Clark Goble mentions Underscore.ObjC.
Nathan Olivarez-Giles and Mat Honan:
An Apple worker with knowledge of the situation, speaking on condition of anonymity, told Wired that the over-the-phone password freeze would last at least 24 hours. The employee speculated that the freeze was put in place to give Apple more time to determine what security policies needed to be changed, if any.
This is a good first step.
In an earlier attempt on Tuesday to change an AppleID password (which is the same password used to log into iCloud and iTunes), Apple customer service offered up a different response, saying that passwords could only be changed over the phone if we were able to supply a serial number for a device linked to the AppleID in question — for example, an iPhone, iPad or MacBook computer.
This seems like a bad idea, as anyone who had not specifically deactivated a device before selling or donating it would be vulnerable.
Yesterday, Apple issued a statement noting that “we found that our own internal policies were not followed completely.” However, Wired’s internal source at Apple said that if the support representative who took the hacker’s call issued a temporary password based on an Apple ID, billing address, and the last four digits of a credit card, he or she would have “absolutely” been in compliance with Apple policy.
Kenneth Ballenegger:
We have many computing devices; Macs, iPhones, and iPads, and we want to be able to pick up any of them and have access to our data. They need to sync instantly and effortlessly. This means that they require a backend web software component. This means running and maintaining servers. Writing code in a foreign programming language and dealing with a wholly new class of problems. (How do you scale your backend software? Which language / platform / framework do you use? At which point do you re-architect for a distributed system? Wait, this shit runs on Linux?)
This is one thing that, from an outside perspective, Microsoft seems to have done rather well. For more than ten years, it’s been shipping a unified framework (.NET) and language (C#) for Web and desktop programming. NeXT had WebObjects/EOF and Objective-C, then it moved WebObjects to Java and added the Cocoa-Java bridge on the desktop, and we know how that went.
I just came across a link to Lloyd Chambers’s epic Drobo review from 2009:
The DiskTester results are shown below. These are the slowest results with Firewire 800 I’ve ever seen, by at least a factor of two, and about 1/3 the speed achievable with a laptop hard drive in an OWC On-The-Go case.
I didn’t understand the fascination when Drobo first came out and still don’t really see the appeal. It’s not fast, it’s not cheap, and you need at least two if you want to have a backup. What are you really gaining from all the custom hardware and software?
In the wake of Mat Honan’s story, Marko Karppinen shares his story from 2008 in which “Apple just gave out my Apple ID password because someone asked.” Via Paul Kafasis, who writes:
As long as Apple believes the last four digits of your credit card are enough to verify you, however, your Apple ID is definitely not safe.
An Apple ID is pretty much required these days, but you can at least limit the potential damage. Don’t use iCloud’s e-mail account, even as a backup address supplied to other services. Honan’s Gmail was compromised because the password recovery e-mail went to his me.com address. And don’t enable Find My Mac.
Apple ID
Nathaniel Popper (via Andy Baio):
The Knight Capital Group announced on Thursday that it lost $440 million when it sold all the stocks it accidentally bought Wednesday morning because a computer glitch.
Nanex Research:
When the time comes to deploy the new market making software, which is likely handled by a different group, the Tester is accidentally included in the release package and started on NYSE’s live system. On the morning of August 1st, the Tester is ready to do its job: test market making software. Except this time it’s no longer in the lab, it’s running on NYSE’s live system. And it’s about to test any market making software running, not just Knights. With real orders and real dollars. And it won’t tell anyone about it, because that’s not its function.
Matt Cutts (via Daniel Jalkut):
You can use Google Authenticator to do two-factor authentication with LastPass, WordPress, Amazon Web Services, Drupal, and DreamHost, or even use a YubiKey device. There’s even a Pluggable Authentication Module (PAM) so you can add two-factor authentication to any PAM-enabled application. That means you can use Google Authenticator to add two-factor authentication to SSH, for example.
It’s pretty neat that the Google Authenticator app works without a network connection.
Update (2012-09-21): Rich Siegel reminds us to unregister any authenticator apps before upgrading to a new phone.
Google Authenticator iOS iOS App Security Two-Factor Authentication (2FA)
Paul Kafasis:
So that’s how you land a one-ton, car-sized, nuclear-powered rover on a planet 150 million miles away. And oh, one other thing? Because of the 28 minute round-trip for radio signals between Mars and Earth, this all had to be done automatically, with no human intervention whatsoever. We could only sit back and wait to hear word of our success or the deafening silence which would indicate failure. Guided entry, parachute descent, powered descent, and an honest-to-goodness hovering sky crane, all pre-programmed to be able to handle anything an inhospitable foreign planet could throw at us.
Sebastian Anthony (via John Gruber):
In this case the Mars rover is powered by a RAD750, a single-board computer (motherboard, RAM, ROM, and CPU) produced by BAE. The RAD750 has been on the market for more than 10 years, and it’s currently one of the most popular on-board computers for spacecraft. In Curiosity’s case, the CPU is a PowerPC 750 (PowerPC G3 in Mac nomenclature) clocked at around 200MHz — which might seem slow, but it’s still hundreds of times faster than, say, the Apollo Guidance Computer used in the first Moon landings. Also on the motherboard are 256MB of DRAM, and 2GB of flash storage — which will be used to store video and scientific data before transmission to Earth.
See also: xkcd.
Update (2012-08-16): A Reddit AMA with members of the Curiosity team (via John Gruber):
You are right that the processor does feel acient. Our current smarthphones are more powerful. The reasoning for this is three-fold. First of all, the computer was selected about 8 years ago, so we have the latest and greated space certified parts that existed then. Second of all, it was the most rubost and proven space grade processor at that time. Thirdly, in order to make a processor radiation hardened it requires lots of tricks on the silicon that is not conducive to making it fast. Given that, it does not run any GUIs and can just focus on raw programming, and actually gets a lot done. All of the programming is done in C, and our toolchain is very similar to programming on any platform.
Brent Simmons:
I canceled my Facebook account. You should be afraid of me.
Andy Lee:
Isn’t that a tautology? If I share the file without modification, then the licensing terms are already in the file. If I remove the licensing terms from the file, then it’s no longer “without modification”, and I am then free to share the file sans licensing terms. That’s what I would naively think. Does the law include a rule of some kind to avoid this circularity?
Matt Neuburg:
Auto Save in Lion, users objected, was thus a potential trap, an invitation to cause the very thing it was supposedly designed to prevent — accidental data loss. The data might not really be lost, since the Versions database might hold an acceptable earlier state of the document; but finding that state in the clumsy Time Machine-like interface wasn’t easy. And what if, after saving a problematic change that you weren’t even aware of, you closed the document and didn’t return to it for days, perhaps weeks, opening it later only to be horrified and confused? Would Versions help you understand what had happened? Would the database still contain the desired document state? It all seemed so backwards, somehow: first make a
drastic accidental mistake, then later discover it (if you’re lucky) and scurry around trying to fix it — whereas, prior to Lion, you would have been alerted before making the mistake of saving the faulty document in the first place.
This is better in Mountain Lion. See also: Data Loss via “Save As” on 10.8.
However:
Please note, though, that I’m not claiming to be entirely happy with the Modern Document Model. Actually, to be quite honest, in my view, Auto Save is itself a massive mistake, an utterly erroneous pretense that the desktop is like iOS. Its deeply flawed nature is well revealed by what happens when you edit a file on a mounted remote disk: you get Auto Save without Versions, which even Apple has admitted is troublesome; see Adam Engst’s article on this topic, “Beware Lion’s Versions Bug on Network and Non-HFS+ Volumes,” 8 September 2011.
He also explains exactly what the “Close windows when quitting an application” checkbox does, which is not quite what I first thought. It does makes sense when you think about the new document model, but perhaps it would be better off as two separate options.
Document Model Mac Mac OS X 10.8 Mountain Lion
MASShortcut is an open-source project for recording, storing, and using global keyboard shortcuts (via Matt Gemmell). It bills itself as being more modern than Shortcut Recorder, although aside from the block-based API it’s not clear to me exactly what the advantages are. It doesn’t seem to support high-numbered function keys.
Sunday, August 5, 2012
Llyod Chambers:
If one edits a document, then chooses Save As, then BOTH the edited original document and the copy are saved, thus not only saving a new copy, but silently saving the original with the same changes, thus overwriting the original.
Mountain Lion’s document model is an improvement over Lion’s, but this is a pretty serious bug.
Document Model Mac Mac OS X 10.8 Mountain Lion
Saturday, August 4, 2012
Mat Honan (via Hacker News):
In short, someone gained entry to my iCloud account, used it to remote wipe all of my devices, and get entry into other accounts too.
It seems way too dangerous to allow anyone with access to your iCloud account to remote wipe your Mac. (Plus, is remote wiping really necessary if you have FileVault enabled?) It looks like the only way to disable remote wipe is to disable the entire Find My Mac feature in the iCloud pane of System Preferences.
Secondly, the new Allow my Apple ID to reset this user’s password is potentially dangerous. Or, if you’re using File Vault 2, there’s the similar option to store your recovery key with Apple.
Backing up to the cloud is great, but those backups are only as safe as your password, so they shouldn’t be your only backups.
Update (2012-08-04): Daniel Jalkut:
One way to protect yourself is by declining to delegate authentication to third parties. When enrolling in a new service that offers Twitter or Facebook authentication, I usually go through the nuisance of creating a new account instead. That way I can choose a unique passphrase, and store that in my keychain. I prefer this to allowing numerous items to be implicitly added to my Twitter or Facebook “keychain.” Don’t put all your eggs in one basket, as they say. (Well, that’s what I’m doing with my keychain, but I am empowered to personally protect it and to back it up as I see fit.)
Update (2012-08-05): Mat Honan:
I know how it was done now. Confirmed with both the hacker and Apple. It wasn’t password related. They got in via Apple tech support and some clever social engineering that let them bypass security questions.
Update (2012-08-05): Jonathan Grynspan reports that there’s a bug that can allow anyone with access to your Apple ID (which obviously includes Apple itself) to access your FileVault-encrypted drive, even if you’ve not shared your FileVault recovery key with Apple.
Update (2012-08-06): Mat Honan:
At 4:33 p.m., according to Apple’s tech support records, someone called AppleCare claiming to be me. Apple says the caller reported that he couldn’t get into his .Me email — which, of course was my .me email.
In response, Apple issued a temporary password. It did this despite the caller’s inability to answer security questions I had set up. And it did this after the hacker supplied only two pieces of information that anyone with an Internet connection and a phone can discover.
Update (2012-08-17): Mat Honan:
My data came back to me on an external hard drive, organized by file types. The thing I cared most about, above all else, was my photo library. And there, in a folder full of JPGs, was photo after photo after photo that I had feared were gone forever. Subfolders were organized by the year, month and day files were created. I went immediately to the folder that bore the date my daughter was born. They were there. Everything was there. We were floored. I nearly cried.
Update (2017-09-20): Juli Clover:
Over the last day or two, several Mac users appear to have been locked out of their machines after hackers signed into their iCloud accounts and initiated a remote lock using Find My iPhone.
Apple ID FileVault Find My iPhone Find My Mac iCloud Mac Security Top Posts
Mike Abdullah:
So I did a search for “power assertions os x” and frankly came up pretty blank. It seems Apple’s documentation mostly consists of reproducing chunks of the header files. Not to worry, they’re fairly easy to understand, so here for the benefit of future generations is a simple example…
Power assertions are a technology for preventing the Mac from going to sleep automatically. Mountain Lion is more aggressive about doing this, so applications need to tell it which operations shouldn’t be interrupted. He’s also posted a simple Cocoa wrapper for the relevant I/O Kit APIs.
Update (2012-08-09): Keith Harrison:
The pmset command (/usr/bin/pmset) provides command-line access to many of the power management settings that are visible in the Energy Saver preferences pane. In addition it provides a way to view and manage power assertions. For example if I use iTunes to play some music it allows the display to sleep but a power assertion prevents the system from entering the idle sleep mode.
It can also show you which processes are preventing sleep.
Kirk McElhearn:
You’re probably familiar with the ability to Shift-click to extend a selection, and Command-click to make a non-contiguous selection. But the ability to combine both of these can be very useful when you want to select a number of items in a list.
Jon Harrop (via
Dave Dribin):
All modern functional language implementations continue to box excessively. JVM-based languages like Clojure and Scala have little choice because the VM they target cannot even express value types. OCaml sheds type information early in its compilation process and resorts to tagged integers and boxing at run-time to handle polymorphism. Consequently, OCaml will often box individual floating point numbers and always boxes tuples. For example, a triple of bytes in OCaml is represented by a pointer (with an implicit 1-bit tag embedded in it that gets checked repeatedly at run-time) to a heap-allocated block with a 64 bit header and 192 bit body containing three tagged 63-bit integers (where the 3 tags are, again, repeatedly examined at run time!). This is clearly insane.
Friday, August 3, 2012
David Pogue:
When you look at it one way, the tech industry is about constant innovation, steady progress. Of course some things will become obsolete. Of course there will be new features that your older computer can’t exploit.
But if you look at it another way, the whole thing is a scam to make us keep buying new stuff over and over again. A new phone every two years. A new computer every four. Bad for our wallets, bad for the environment.
Mathias Bynens has posted a shell script with lots of commands (defaults write and otherwise) for tweaking OS X settings (via Clark Goble). There are a bunch that I hadn’t seen before, but I want to draw particular attention to the use of /usr/libexec/PlistBuddy, which somehow I’d never seen before. I had been using /usr/bin/defaults to manipulate arbitrary property list files (by passing a full path, minus the .plist), but I’ve recently been advised not to use it for that.
Esoteric Preferences Mac Mac OS X 10.8 Mountain Lion
Paul Kim (via Nicholas Riley):
Apparently this will sound strange to a certain segment of people, but I’m also not interested in having a huge number of customers, in and of itself. I don’t really get satisfaction from people who buy the product in a promo or based on hype and don’t use it. I’m not hit-driven. I want users buying my product, not consumers. What really motivates me is when I hear about people that have been using it for years and it’s one the first things they install whenever they get a new machine. It’s when people get excited as I am about new features. It’s when users comes up with unique ways of using the product that I wouldn’t have come up with myself.
Ditto.
Kellan Elliott-McCrea’s oldtweets is a search engine for the first year of Twitter (via Core Intuition). It doesn’t seem to have found any of my tweets, but I already archived them via Tweet Nest a while ago.
I’ve already linked to Daniel Jalkut’s Subscribe to Feed—which adds an RSS button back to Safari 6—in my Mountain Lion notes, but I wanted to give it its own post. It’s a great piece of work and the first solid reason I’ve had for enabling Safari extensions.
Matt Neuburg:
Optimistic attempts by various Apple boosters to justify this astonishing behavior have not, in my view, met with any success. The best that can be said for it is that, given the existence of additional Lion and Mountain Lion features such as Auto Save and Resume (which, together, allow an application’s state to be restored the next time it is launched), the distinction between whether an application is running or not is of diminished importance. That might be the case, if an automatically terminated application’s icon remained in the Dock and the Command-Tab switcher, so that you could conveniently relaunch it; and some pundits have suggested that the icon’s failure in this regard was just a minor bug which
Apple would fix in due course. But the fact is that throughout all versions of Lion, and now in Mountain Lion, Apple has not altered this aspect of Automatic Termination’s behavior; an automatically terminated application’s icon is still removed from the Dock and the Command-Tab switcher, just as it would be if the user had quit the application deliberately. And so the user, who did not quit the application deliberately, is puzzled and annoyed, and in order to continue using this application must now search for it and relaunch it all over again.
Erik J. Barzeski:
Mail in Lion properly responded from the same email address that received the email. Mail in Mountain Lion does not and instead replies from the default email address, regardless of the setting(s) chosen in the preferences.
Kirk McElhearn:
Generally, if you have multiple e-mail accounts, when you reply to a message, your reply uses the same account the message was sent to. But I’ve been finding that Mail does not correctly choose the account, and have seen a number of messages bouncing because the selected account is not a member of the mailing lists.
Update (2012-08-08): Joe Kissell:
However, in Mountain Lion, Apple significantly changed the rules by which Mail chooses the default From account for outgoing messages. As a result, if you don’t carefully (and manually) check each outgoing message, you might find that you’re sending messages from an unintended account. This can have serious consequences if, for example, you end up sending work email from a personal account or vice-versa.
Update (2013-03-14): This is apparently fixed in Mac OS X 10.8.3.
Apple Mail Bug Mac Mac App Mac OS X 10.8 Mountain Lion
Wednesday, August 1, 2012
Keith Harrison:
Most of the time the compiler will add the ivar for you when it adds the required accessor methods. However there are certain situations where you will still need to add the instance variable for yourself. In general the compiler will generate the instance variable automatically any time it generates at least one of the accessor methods.
Edge Cases episode 11:
Wolf Rentzsch talks with Andrew Pontious about Mac App Store irrelevance, the Sparrow acquisition, and so-called “pop software” and its impact upon independent software developer livelihoods.
I like the rejected titles list.

