FileVault 2’s Apple ID Backdoor
This is a guest post by Jonathan Grynspan. I followed his reporting of this issue on Twitter with interest. The basic issue is that, with the default settings, if your Mac is asleep or booted up and logged out, anyone who has your Apple ID and password can access your encrypted FileVault 2 files. This is true even if you have not shared your FileVault recovery key with Apple. Far more than 140 characters were needed to get the full picture, so I encouraged Jonathan to blog about it. As he does not currently have a blog, we decided to post his report here. —Michael
I’m Jonathan Grynspan. I write code. I’m a little wordy. This is gonna be a long one, ’cause of the wordiness.
I, like a number of other security-minded Mac users, turned on FileVault 2 before my new MacBook Air was even out of the box. Whole-drive encryption? Damn skippy! Turns out however that, as of Mountain Lion, FileVault 2 has a 50/50 chance of being completely broken on your system. There’s a backdoor that appears to have been accidentally built in by Apple, and it can be used by an attacker to gain root access on your system.
Mac OS X v10.7 Lion and later include a feature intended to help users with oddly spotty memory. If you’ve forgotten your login password, but remember your Apple ID password, you can reset your login password based off that. (If alarm bells are going off in your head right now, they might be because of Mat Honan’s recent bad luck involving his iCloud account, which doubles as an Apple ID.) In order to use this feature, you must enable it in System Preferences → Users & Groups. That looks like this:
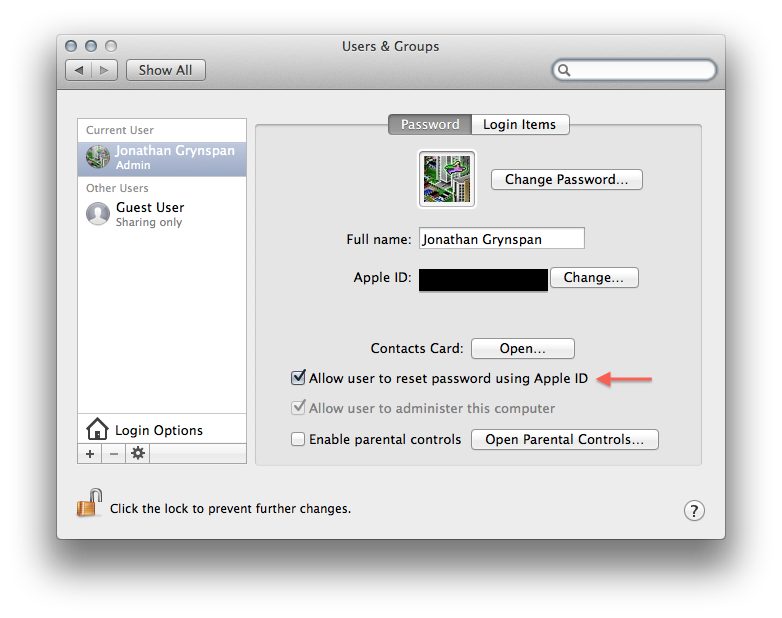
Worryingly, this was enabled by default on my MacBook Air as soon as I upgraded from the copy of Lion it shipped with. I did not enable this feature.
OS X also includes a feature called FileVault 2, as I previously mentioned, that encrypts your entire hard drive and requires your login password to decrypt it. When FileVault 2 is enabled, resetting your password by entering your Apple ID is intended to be disabled (as suggested by the FileVault 2 tech note linked above.) Problem is, it’s not disabled—the option is just hidden from view in System Preferences. As I found out a few days ago, if the setting is enabled when you encrypt your drive, the checkbox disappears and you cannot disable it1. The only way to turn off Apple ID–based password recovery is to decrypt your drive, change the setting, and re-encrypt. That process can take a very long time depending on the size of your drive and whether it’s a hard disk or an SSD. The 1 TB drive on my iMac takes several hours to process completely.
My iMac, though protected with FileVault 2, can be accessed fully (including root access via sudo using my login password) by an attacker who knows my Apple ID password, almost completely defeating FileVault 2. I should note that, to my knowledge, this issue requires physical access to your Mac2. That said, FileVault 2 is explicitly designed to protect against attacks even when the user has physical access; whole-drive encryption is kind of pointless otherwise. But it gets worse. An Apple employee might never touch your keyboard, but Apple ID–based password recovery as designed may allow a malicious Apple employee to gain access—there’s no guarantee or promise from Apple that turning off the feature in the OS UI actually disables the logic involved.
I don’t want to be alarmist. I believe this was an honest oversight by Apple’s engineers, and one that can be corrected in a point release. I’m a loyal Apple user and have been for years. I make a living writing code that only runs on Apple products. But Apple’s boilerplate response when I reported this backdoor was worrisome at best:
Thank you for filing this issue via Apple’s bug reporting system. Apple takes every report of a potential security issue very seriously. After examining your report we do not see any actual security implications. [emphasis mine]
My Apple ID controls much of my data—especially the data I associate with my dealings with Apple, Inc. My login password, on the other hand, protects via FileVault 2’s encryption: every photo of my loved ones that I’ve ever taken; identifying information including my address, phone number, Social Insurance Number, and passport number; all my banking records and tax returns; my medical records…this is personal stuff, not work stuff. I don’t want somebody to be able to decrypt my drive and see it because they have an unrelated Internet-facing password.
Worse, what if I had incriminating evidence on my hard drive (e.g. some movie torrents, or photos of me and my friends and eleven herbs and spices)? A government (foreign or domestic) could serve Apple with a warrant and unlock my encrypted drive for me and I wouldn’t be able to stop them—I don’t even know if turning off the feature in System Preferences would actually do any good! Kim Dotcom would go apeshit over this backdoor.
If the system is coming up from a cold boot, the option to use your Apple ID is not present, presumably because the system can’t load network drivers until it has decrypted them. You’re safe at that point. But once the system is up, if you log out or turn on the screen saver or close the lid or somehow wind up at the login screen, the option appears and can be used. When the setting is enabled, the password hint popup looks like this:
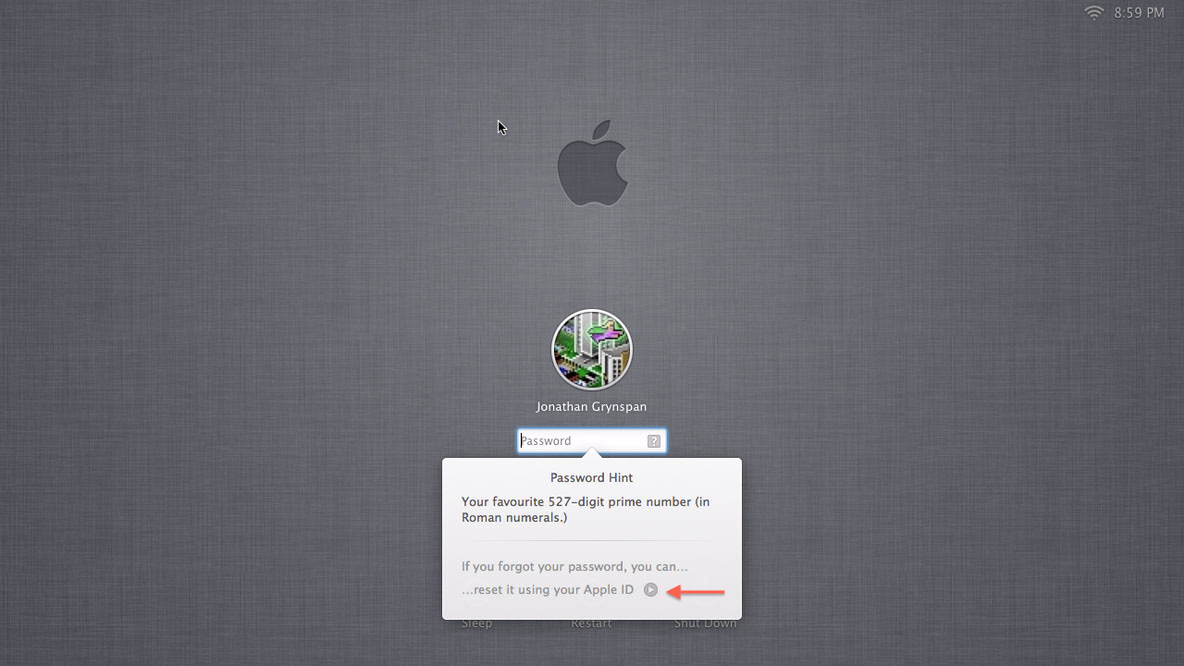
And the attacker can use that arrow button to gain access very quickly. There is therefore a workaround, but it requires vigilance. Whenever you leave your computer for more than a few seconds, shut it down entirely. Don’t let it go to the login screen unless it’s the one presented by FileVault 2 at boot time. And don’t let your Mac out of your sight.
My thanks to Michael for giving me a soapbox on which to stand here.
1 This is the behaviour on Mountain Lion. Neither Michael nor I have been able to verify how Lion behaves. ↩
2 This isn’t entirely true. I took this screenshot using Screen Sharing (since I can’t exactly save a screenshot to the desktop or clipboard before I’ve logged in.) Having done so, I realized that enabling Screen Sharing may expose an even bigger hole, but I don’t know for certain. I have my doubts about command-line access (e.g. SSH) too. ↩
34 Comments RSS · Twitter
Does this still apply if you opt out of storing your FileVault encryption key with your Apple ID?
[...] internaute révèle que le logiciel de chiffrement de disque FileVault 2 utilisé sur Mountain Lion active par défaut la possibilité de réinitialiser le mot de passe de votre machine Apple via la s... (password pour les services en ligne). Au delà de cette activation par défaut réalisée sans en [...]
Don't trust Bitlocker, FileVault2, or anything else except Truecrypt. You have really confidential data to protect? Put it in a Truecrypt volume file. Do not save the password in the Keychain. Set d password using 12-16 characters. I have made DVD-R discs that appear blank but actually contains an encrypted hidden partition.
This might be a problem - but imho it is is not a FileVault/WDE issue.
WDE only protects you if your system is turned off. If the system is up and running but locked, WDE is already defeated. Once you booted it, everything is decrypted transparently. The lock has nothing to do with WDE.
You could unlock the system for example with a Firewire/Thunderbolt device, that has DMA access. We did that before.
bye, ju
As mentioned, another workaround after experiencing the issue might be to decrypt (wait), make sure the checkbox is unchecked, encrypt (wait). Can someone confirm?
The easiest solution in this case may be to take the Apple ID info out of your account's listing in Users & Groups. Here's how to do this:
1. Open System Preferences
2. Go to Users & Groups
3. Select your account.
4. In the "Apple ID:" section, click on the "Change...." button.
5. In the drop-down window that appears, select your Apple ID account.
6. Click the minus (-) button in the lower-left corner of the window. Your Apple ID should be removed.
7. Click the "Done" button.
Your Apple ID will no longer be associated with your account, which removes the ability to use your Apple ID to reset your password.
@Erik: Yes, and that's what I did. The problem is that the average user isn't even going to know about this because there's no other exposure in the UI when FileVault 2 is enabled (the checkbox in System Preferences is hidden.)
@Rich: For the average user, who is prompted with a big and pretty screen at first launch to enter his/her Apple ID and then is likely to never touch it again, this isn't viable. I'm not sure if this limits app functionality though--what *does* Apple use that setting for other than password reset?
(Then again, the average user probably won't turn on FileVault 2.)
My Mac running Mountain Lion & FV2 doesn't have that checkbox in Users & Groups. My User & Groups preferences pane looks exactly like yours except for that one checkbox that mine does not have. Ideas?
Jonathan,
You raise a good point. Here's a post on my own site for how to avoid associating your Apple ID with your Mac's account on Mountain Lion:
Hopefully, it's detailed enough that anyone can follow it.
@Brian Part of the issue that Jonathan is reporting is that Mountain Lion hides the checkbox when FileVault is enabled, so you can’t see (or change) whether Apple ID–based resetting is enabled. You have to make sure the setting is correct before turning on FileVault.
If you click that 'Change...' button in your Account settings, you have the option to add/remove AppleIDs. If you make a change there, the EncryptedRoot.plist.wipekey on the Recovery HD is regenerated. That likely means that the accounts that are allowed to login to FileVault have been synced there.
@Stefan: That sounds promising, but it's supposition at this point and I'd like to see a more formal audit of this system/feature. That's beyond my abilities. :)
If the Mountain Lion upgrade enabled "Allow user to reset password using Apple ID" on your MBA, this is a bug specific to certain configurations. In particular, this *did not* happen when I upgraded my MBA from Lion to Mountain Lion, nor did it happen when I upgraded a copy of my "template VM " of Lion 10.7.4 to Mountain Lion using the App Store installer this evening to confirm my own recollections.
[...] pisze Johnatan Grynspan, w jego przypadku ta opcja po aktualizacji systemu do Mountain Liona była domyślnie włączona! I [...]
[...] pisze Johnatan Grynspan, w jego przypadku ta opcja po aktualizacji systemu do Mountain Liona była domyślnie włączona! I [...]
Doesn't this only happen if you choose to have Apple keep a backup copy of your key? If you don't allow apple to keep a copy of your key during FV2 setup then this option will not be there and cant be accessed with your iCloud account password.
@jerry No, that’s what’s tricky about this. The files can be accessed using your Apple ID even if you didn’t share your FileVault key with Apple.
I heard that apple shuts down fw and tb drivers when user is logged out so that DMA access to memory is prevented.
Can anybody confirm?
According to http://support.apple.com/kb/HT4790 the message that pops up if you type your password incorrectly three times is...
If you forgot your password, you can… …reset it using your recovery key.
This sounds like the option to reset your password via your Apple ID is removed automatically when you use FileVault2. Can anyone confirm?
@Tim Dearborn I think that article is talking about a different issue. The recovery key comes into play if the Mac is off. If the Mac is on (i.e. FileVault has already been unlocked) but asleep or logged out, all you need is the Apple ID and password (regardless of whether you shared the recovery key with Apple).
[...] note, it does not appear that two-step verification is needed to remote wipe or to access FileVault-encrypted files on a locked but powered-on Mac. It seems more likely that someone would get my Apple ID password than that I would need to remote [...]
Hello all. I understand the security aspect of FV but lets face it, some (a lot) of us dont know what we are doing sometimes. Have locked my main user in FV and after upgrade cannot access this user profile, even after reinstalling previous OS. Back up and Time Machine have been useless. Dont think there are enough warnings before upgrade and what you should and should not do.
Michael, thank you for Spamsieve - have used for years!
Hello.
A few days ago I encrypted my boot hard drive using FV2 on Mountain Lion (10.8.4).
When I did it I wasn't aware of this issue (not the smartest move to encrypt first and the look for vulnerabilities later, I get it now...), so I had the "Allow user to reset password using Apple ID" active and obviously now, after the encryption, the checkbox is gone and I can't disable it.
Since I wanted to see if the issue described in this post is still a problem with the current release of Mac OS X, I tried to reboot my MBP and I wrote the wrong password 3 times; the system though didn't ask me for the Apple ID access, just for the encryption key generated during the process (which obviously I didn't store with Apple).
I wonder if Apple has closed the Apple ID "possible workaround" after this article was published and if then it is not an issue anymore with 10.8.4.
Better safe than sorry, I removed my Apple ID from the Users panel of System Preferences (though I am not sure that it would have worked without the decrypt>disable>encrypt again solution, but again I'm not asked to input my Apple ID so...).
Thanks a lot.
Sara
@Sara The cold boot has always worked as you describe. The Apple ID security issue only applies if the Mac is already on but the screen is locked due to sleep, the screensaver, or being logged out.
@Michael Oh, I didn't get it, thanks.
I just tried both logging out and running the screensaver (password-protected) and although I typed the wrong password multiple times, I've never been asked to login with my Apple ID.
So I imagine that a) Mountain Lion 10.8.4 fixed that b) Removing the Apple ID from the Users panel in System Preferences was enough to solve the problem
Thanks again
Sara
[...] Forskare har tidigare kunna knäcka Apples slumpgenererade lösenord på mindre än 1 minut, och det visar sig nu att dessa slumpvis genererade lösenord inte alls är slumpvis genererade, utan följer ett förutbestämt mönster. Apple’s filevault 2 som används flitigt i Mac, är en säkerhetslösning som har till syfte att skydda informationen från obehöriga, men det har nu framkommit att både Apple och NSA läser av denna information även när den är inaktiverad av användaren. [...]
[...] information and privileges, including the ability to remote wipe iOS devices and access your Mac, even if you didn’t share your FileVault 2 recovery key with Apple. It doesn’t seem prudent to [...]
[…] reboots — you must unlock the system at boot to get at the decryption keys). Also, be aware your Apple ID is a potential security hole as well (unset your Apple ID for all accounts to avoid this). Note that the filesystem and […]
[…] The login password (but not the password of the login keychain) can also be reset with an Apple ID. There’s a checkbox for allowing that when creating an account. I think it was checked by default. The option can be disabled later in the Users & Groups preference pane. If the option was enabled before you turned FileVault on, you cannot disable it without turning FileVault off and back on. See Michael Tsai – Blog – FileVault 2’s Apple ID Backdoor. […]
[…] gain access to your e-mail, calendar, and documents (and, in typical configurations, could even log on to your machine if he had access to […]
[…] The login password (but not the password of the login keychain) can also be reset with an Apple ID. There’s a checkbox for allowing that when creating an account. I think it was checked by default. The option can be disabled later in the Users & Groups preference pane. If the option was enabled before you turned FileVault on, you cannot disable it without turning FileVault off and back on. See Michael Tsai – Blog – FileVault 2’s Apple ID Backdoor. […]