Lloyd Chambers:
Time Machine has repeatedly and silently added both my Boot and Master volumes to its “Exclude these items...” list.
This is not a one-time thing, I have seen it happen 15-20 times in 3 months. This includes after erasing the backup drive and the original volumes, so it is not tied to a particular volume; it is a general bug. With OS X Lion and Mountain Lion.
I never saw this bug when I was using Leopard or Snow Leopard. With Lion, I stopped using Time Machine as it was severely slowing down my system and frequently corrupting its backups.
This is a guest post by Jonathan Grynspan. I followed his reporting of this issue on Twitter with interest. The basic issue is that, with the default settings, if your Mac is asleep or booted up and logged out, anyone who has your Apple ID and password can access your encrypted FileVault 2 files. This is true even if you have not shared your FileVault recovery key with Apple. Far more than 140 characters were needed to get the full picture, so I encouraged Jonathan to blog about it. As he does not currently have a blog, we decided to post his report here. —Michael
I’m Jonathan Grynspan. I write code. I’m a little wordy. This is gonna be a long one, ’cause of the wordiness.
I, like a number of other security-minded Mac users, turned on FileVault 2 before my new MacBook Air was even out of the box. Whole-drive encryption? Damn skippy! Turns out however that, as of Mountain Lion, FileVault 2 has a 50/50 chance of being completely broken on your system. There’s a backdoor that appears to have been accidentally built in by Apple, and it can be used by an attacker to gain root access on your system.
Mac OS X v10.7 Lion and later include a feature intended to help users with oddly spotty memory. If you’ve forgotten your login password, but remember your Apple ID password, you can reset your login password based off that. (If alarm bells are going off in your head right now, they might be because of Mat Honan’s recent bad luck involving his iCloud account, which doubles as an Apple ID.) In order to use this feature, you must enable it in System Preferences → Users & Groups. That looks like this:
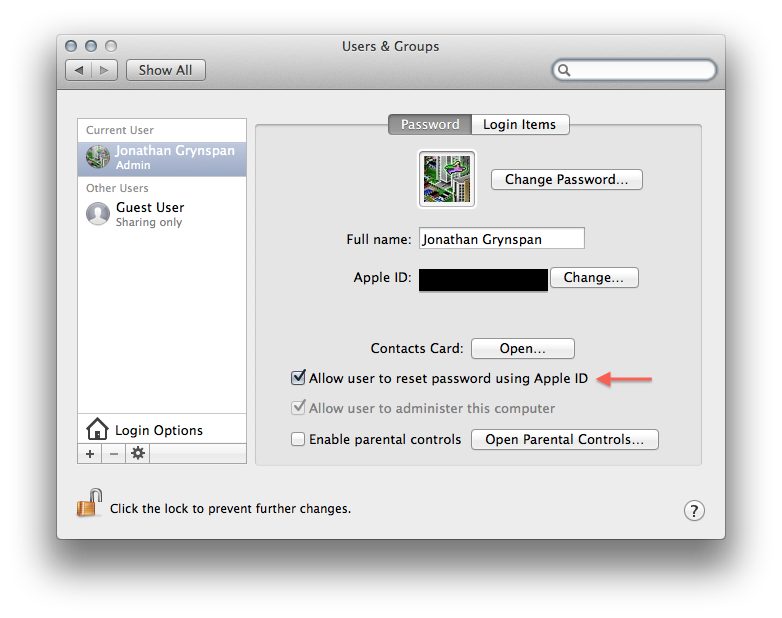
Worryingly, this was enabled by default on my MacBook Air as soon as I upgraded from the copy of Lion it shipped with. I did not enable this feature.
OS X also includes a feature called FileVault 2, as I previously mentioned, that encrypts your entire hard drive and requires your login password to decrypt it. When FileVault 2 is enabled, resetting your password by entering your Apple ID is intended to be disabled (as suggested by the FileVault 2 tech note linked above.) Problem is, it’s not disabled—the option is just hidden from view in System Preferences. As I found out a few days ago, if the setting is enabled when you encrypt your drive, the checkbox disappears and you cannot disable it. The only way to turn off Apple ID–based password recovery is to decrypt your drive, change the setting, and re-encrypt. That process can take a very long time depending on the size of your drive and whether it’s a hard disk or an SSD. The 1 TB drive on my iMac takes several hours to process completely.
My iMac, though protected with FileVault 2, can be accessed fully (including root access via sudo using my login password) by an attacker who knows my Apple ID password, almost completely defeating FileVault 2. I should note that, to my knowledge, this issue requires physical access to your Mac. That said, FileVault 2 is explicitly designed to protect against attacks even when the user has physical access; whole-drive encryption is kind of pointless otherwise. But it gets worse. An Apple employee might never touch your keyboard, but Apple ID–based password recovery as designed may allow a malicious Apple employee to gain access—there’s no guarantee or promise from Apple that turning off the feature in the OS UI actually disables the logic involved.
I don’t want to be alarmist. I believe this was an honest oversight by Apple’s engineers, and one that can be corrected in a point release. I’m a loyal Apple user and have been for years. I make a living writing code that only runs on Apple products. But Apple’s boilerplate response when I reported this backdoor was worrisome at best:
Thank you for filing this issue via Apple’s bug reporting system. Apple takes every report of a potential security issue very seriously. After examining your report we do not see any actual security implications. [emphasis mine]
My Apple ID controls much of my data—especially the data I associate with my dealings with Apple, Inc. My login password, on the other hand, protects via FileVault 2’s encryption: every photo of my loved ones that I’ve ever taken; identifying information including my address, phone number, Social Insurance Number, and passport number; all my banking records and tax returns; my medical records…this is personal stuff, not work stuff. I don’t want somebody to be able to decrypt my drive and see it because they have an unrelated Internet-facing password.
Worse, what if I had incriminating evidence on my hard drive (e.g. some movie torrents, or photos of me and my friends and eleven herbs and spices)? A government (foreign or domestic) could serve Apple with a warrant and unlock my encrypted drive for me and I wouldn’t be able to stop them—I don’t even know if turning off the feature in System Preferences would actually do any good! Kim Dotcom would go apeshit over this backdoor.
If the system is coming up from a cold boot, the option to use your Apple ID is not present, presumably because the system can’t load network drivers until it has decrypted them. You’re safe at that point. But once the system is up, if you log out or turn on the screen saver or close the lid or somehow wind up at the login screen, the option appears and can be used. When the setting is enabled, the password hint popup looks like this:
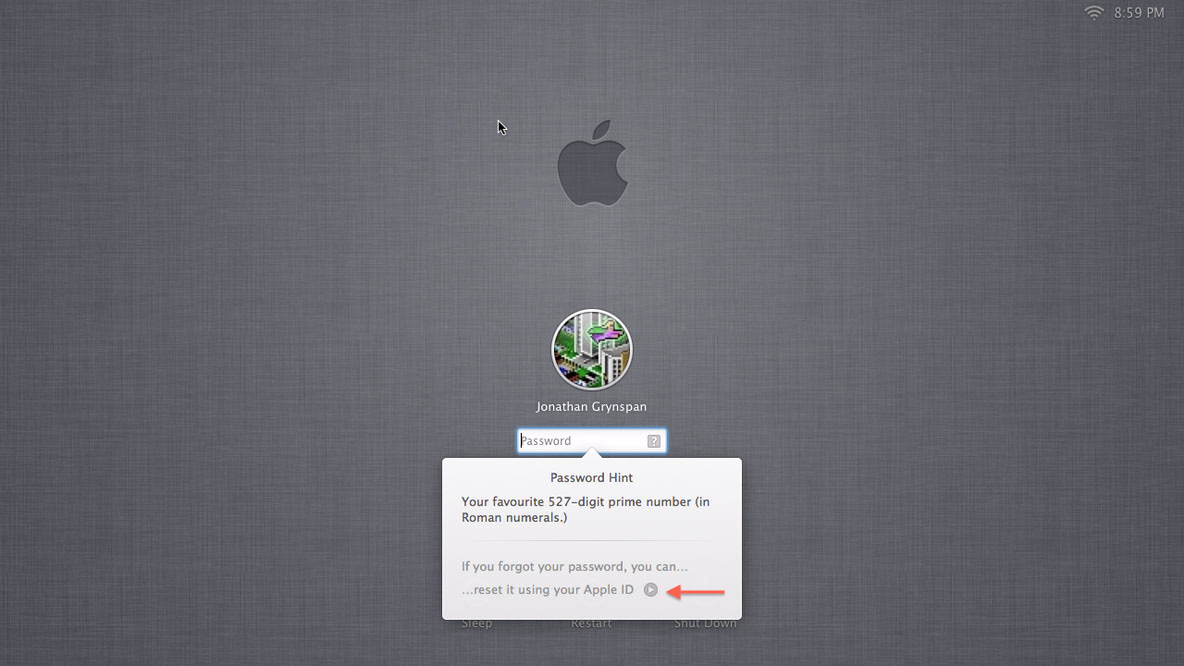
And the attacker can use that arrow button to gain access very quickly. There is therefore a workaround, but it requires vigilance. Whenever you leave your computer for more than a few seconds, shut it down entirely. Don’t let it go to the login screen unless it’s the one presented by FileVault 2 at boot time. And don’t let your Mac out of your sight.
My thanks to Michael for giving me a soapbox on which to stand here.
Apple ID FileVault Mac Mac OS X 10.7 Lion Mac OS X 10.8 Mountain Lion Security Top Posts
Kevin Malakoff (via Hacker News):
_.m is a port of Underscore.js to Objective-C. It strives to provide the fullest feature set possible in a way that is familiar to JavaScript developers (despite the differences between JavaScript and Objective-C).
There are some neat features and ideas here, but it would be interesting to see how they could be expressed with more Objective-C-style naming and syntax. I think most of the utility is in the functionality, not the low character count.
See also: Underscore.m (via Groxx).
Update (2012-08-12): Clark Goble mentions Underscore.ObjC.
Nathan Olivarez-Giles and Mat Honan:
An Apple worker with knowledge of the situation, speaking on condition of anonymity, told Wired that the over-the-phone password freeze would last at least 24 hours. The employee speculated that the freeze was put in place to give Apple more time to determine what security policies needed to be changed, if any.
This is a good first step.
In an earlier attempt on Tuesday to change an AppleID password (which is the same password used to log into iCloud and iTunes), Apple customer service offered up a different response, saying that passwords could only be changed over the phone if we were able to supply a serial number for a device linked to the AppleID in question — for example, an iPhone, iPad or MacBook computer.
This seems like a bad idea, as anyone who had not specifically deactivated a device before selling or donating it would be vulnerable.
Yesterday, Apple issued a statement noting that “we found that our own internal policies were not followed completely.” However, Wired’s internal source at Apple said that if the support representative who took the hacker’s call issued a temporary password based on an Apple ID, billing address, and the last four digits of a credit card, he or she would have “absolutely” been in compliance with Apple policy.
Kenneth Ballenegger:
We have many computing devices; Macs, iPhones, and iPads, and we want to be able to pick up any of them and have access to our data. They need to sync instantly and effortlessly. This means that they require a backend web software component. This means running and maintaining servers. Writing code in a foreign programming language and dealing with a wholly new class of problems. (How do you scale your backend software? Which language / platform / framework do you use? At which point do you re-architect for a distributed system? Wait, this shit runs on Linux?)
This is one thing that, from an outside perspective, Microsoft seems to have done rather well. For more than ten years, it’s been shipping a unified framework (.NET) and language (C#) for Web and desktop programming. NeXT had WebObjects/EOF and Objective-C, then it moved WebObjects to Java and added the Cocoa-Java bridge on the desktop, and we know how that went.
I just came across a link to Lloyd Chambers’s epic Drobo review from 2009:
The DiskTester results are shown below. These are the slowest results with Firewire 800 I’ve ever seen, by at least a factor of two, and about 1/3 the speed achievable with a laptop hard drive in an OWC On-The-Go case.
I didn’t understand the fascination when Drobo first came out and still don’t really see the appeal. It’s not fast, it’s not cheap, and you need at least two if you want to have a backup. What are you really gaining from all the custom hardware and software?
In the wake of Mat Honan’s story, Marko Karppinen shares his story from 2008 in which “Apple just gave out my Apple ID password because someone asked.” Via Paul Kafasis, who writes:
As long as Apple believes the last four digits of your credit card are enough to verify you, however, your Apple ID is definitely not safe.
An Apple ID is pretty much required these days, but you can at least limit the potential damage. Don’t use iCloud’s e-mail account, even as a backup address supplied to other services. Honan’s Gmail was compromised because the password recovery e-mail went to his me.com address. And don’t enable Find My Mac.
Apple ID
Nathaniel Popper (via Andy Baio):
The Knight Capital Group announced on Thursday that it lost $440 million when it sold all the stocks it accidentally bought Wednesday morning because a computer glitch.
Nanex Research:
When the time comes to deploy the new market making software, which is likely handled by a different group, the Tester is accidentally included in the release package and started on NYSE’s live system. On the morning of August 1st, the Tester is ready to do its job: test market making software. Except this time it’s no longer in the lab, it’s running on NYSE’s live system. And it’s about to test any market making software running, not just Knights. With real orders and real dollars. And it won’t tell anyone about it, because that’s not its function.
Paul Kafasis:
So that’s how you land a one-ton, car-sized, nuclear-powered rover on a planet 150 million miles away. And oh, one other thing? Because of the 28 minute round-trip for radio signals between Mars and Earth, this all had to be done automatically, with no human intervention whatsoever. We could only sit back and wait to hear word of our success or the deafening silence which would indicate failure. Guided entry, parachute descent, powered descent, and an honest-to-goodness hovering sky crane, all pre-programmed to be able to handle anything an inhospitable foreign planet could throw at us.
Sebastian Anthony (via John Gruber):
In this case the Mars rover is powered by a RAD750, a single-board computer (motherboard, RAM, ROM, and CPU) produced by BAE. The RAD750 has been on the market for more than 10 years, and it’s currently one of the most popular on-board computers for spacecraft. In Curiosity’s case, the CPU is a PowerPC 750 (PowerPC G3 in Mac nomenclature) clocked at around 200MHz — which might seem slow, but it’s still hundreds of times faster than, say, the Apollo Guidance Computer used in the first Moon landings. Also on the motherboard are 256MB of DRAM, and 2GB of flash storage — which will be used to store video and scientific data before transmission to Earth.
See also: xkcd.
Update (2012-08-16): A Reddit AMA with members of the Curiosity team (via John Gruber):
You are right that the processor does feel acient. Our current smarthphones are more powerful. The reasoning for this is three-fold. First of all, the computer was selected about 8 years ago, so we have the latest and greated space certified parts that existed then. Second of all, it was the most rubost and proven space grade processor at that time. Thirdly, in order to make a processor radiation hardened it requires lots of tricks on the silicon that is not conducive to making it fast. Given that, it does not run any GUIs and can just focus on raw programming, and actually gets a lot done. All of the programming is done in C, and our toolchain is very similar to programming on any platform.
Andy Lee:
Isn’t that a tautology? If I share the file without modification, then the licensing terms are already in the file. If I remove the licensing terms from the file, then it’s no longer “without modification”, and I am then free to share the file sans licensing terms. That’s what I would naively think. Does the law include a rule of some kind to avoid this circularity?
Matt Neuburg:
Auto Save in Lion, users objected, was thus a potential trap, an invitation to cause the very thing it was supposedly designed to prevent — accidental data loss. The data might not really be lost, since the Versions database might hold an acceptable earlier state of the document; but finding that state in the clumsy Time Machine-like interface wasn’t easy. And what if, after saving a problematic change that you weren’t even aware of, you closed the document and didn’t return to it for days, perhaps weeks, opening it later only to be horrified and confused? Would Versions help you understand what had happened? Would the database still contain the desired document state? It all seemed so backwards, somehow: first make a
drastic accidental mistake, then later discover it (if you’re lucky) and scurry around trying to fix it — whereas, prior to Lion, you would have been alerted before making the mistake of saving the faulty document in the first place.
This is better in Mountain Lion. See also: Data Loss via “Save As” on 10.8.
However:
Please note, though, that I’m not claiming to be entirely happy with the Modern Document Model. Actually, to be quite honest, in my view, Auto Save is itself a massive mistake, an utterly erroneous pretense that the desktop is like iOS. Its deeply flawed nature is well revealed by what happens when you edit a file on a mounted remote disk: you get Auto Save without Versions, which even Apple has admitted is troublesome; see Adam Engst’s article on this topic, “Beware Lion’s Versions Bug on Network and Non-HFS+ Volumes,” 8 September 2011.
He also explains exactly what the “Close windows when quitting an application” checkbox does, which is not quite what I first thought. It does makes sense when you think about the new document model, but perhaps it would be better off as two separate options.
Document Model Mac Mac OS X 10.8 Mountain Lion
MASShortcut is an open-source project for recording, storing, and using global keyboard shortcuts (via Matt Gemmell). It bills itself as being more modern than Shortcut Recorder, although aside from the block-based API it’s not clear to me exactly what the advantages are. It doesn’t seem to support high-numbered function keys.

